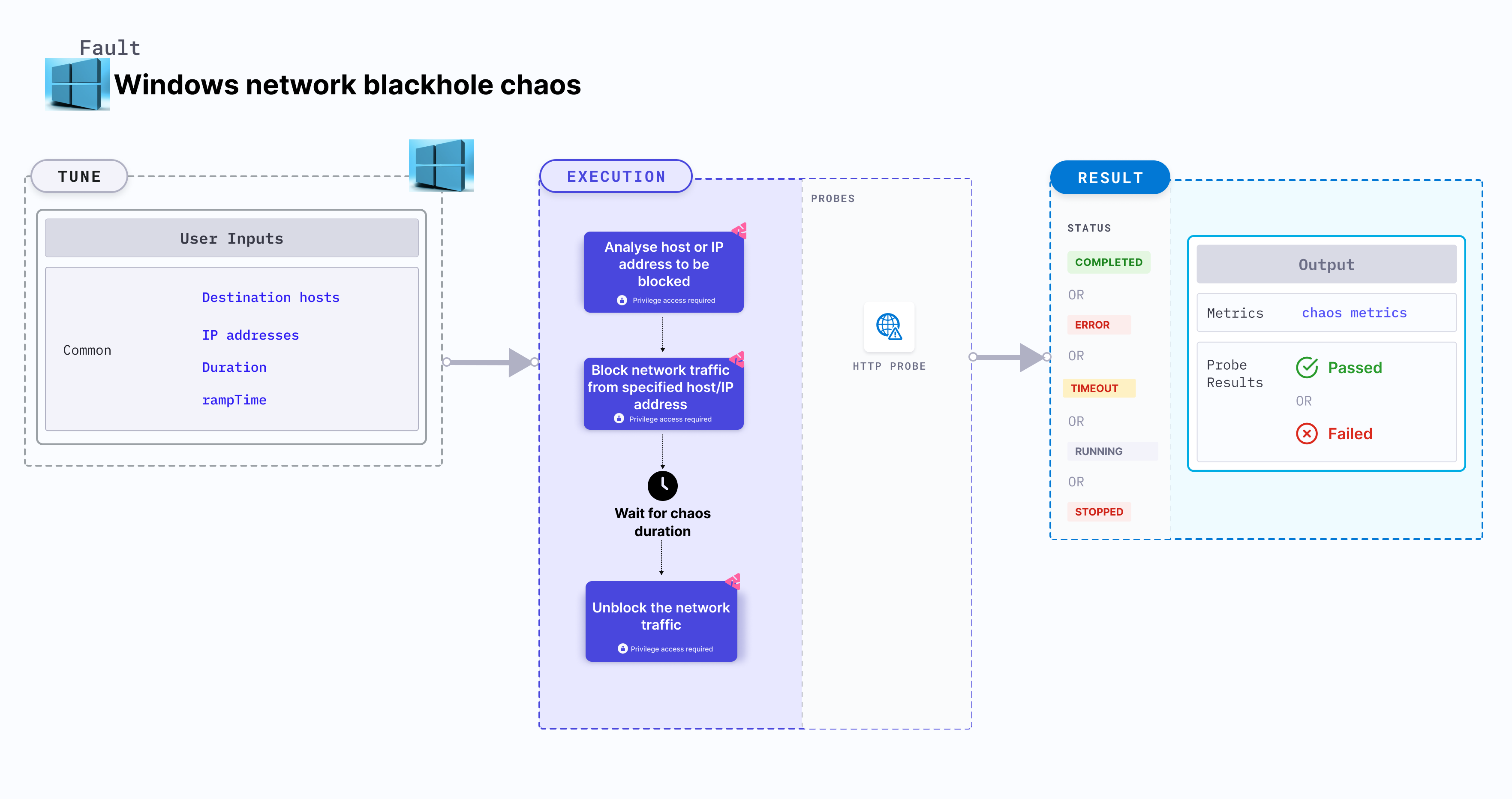
Windows Network Blackhole Chaos
Windows network blackhole chaos simulates a network blackhole scenario on Windows OS based VM.
- It checks the performance of the application running on the Windows VMs under network blackhole conditions.
Use cases
- Windows network blackhole chaos determines the resilience of an application when a network blackhole scenario is simulated on a Windows VM.
- It simulates the situation of network isolation for processes running on the application, which degrades their performance.
- It helps verify the application's ability to handle network failures and its failover mechanisms.
Prerequisites
- Ensure that the prerequisites are fulfilled before executing the experiment.
Mandatory tunables
| Tunable | Description | Notes |
|---|---|---|
| TOTAL_CHAOS_DURATION | Duration that you specify, through which chaos is injected into the target resource (in seconds). | Default: 60s. For more information, go to duration of the chaos. |
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| DESTINATION_HOSTS | Comma-separated list of destination hosts to block. | For example, github.com,harness.io. For more information, go to destination hosts. |
| IP_ADDRESSES | Comma-separated list of IP addresses to block. | For example, 10.0.0.1,10.0.0.2. For more information, go to IP addresses. |
| SERVER_HOST | Provide the server host when running global blackhole chaos that is without destination hosts and IP addresses. | For example, app.harness.io. For more information, go to server host. |
| RAMP_TIME | Period to wait before and after injecting chaos (in seconds). | Default: 0 s. For more information, go to ramp time. |
If the environment variables DESTINATION_HOSTS or IP_ADDRESSES are left empty, the default behaviour is to target all hosts. To limit the impact on all the hosts, you can specify the IP addresses of the service (use commas to separate multiple values) or the DNS or the FQDN names of the services in DESTINATION_HOSTS.
Destination hosts and IP addresses
The DESTINATION_HOSTS environment variable specifies the destination hosts that are to be blocked on the target Windows VM.
The IP_ADDRESSES environment variable specifies the IP addresses to block on the target Windows VM.
Following YAML snippet illustrates the use of this input variable.
apiVersion: litmuschaos.io/v1alpha1
kind: MachineChaosExperiment
metadata:
name: windows-blackhole-chaos-4ap
labels:
context: windows-blackhole-chaos
name: windows-blackhole-chaos-4ap
spec:
infraType: "windows"
steps:
- - name: windows-blackhole-chaos-4ap
tasks:
- name: windows-blackhole-chaos-4ap
infraId: ""
definition:
chaos:
fault: windows-blackhole-chaos
env:
- name: DESTINATION_HOSTS
value: "github.com"
- name: IP_ADDRESSES
value: "10.0.0.1"
- name: DURATION
value: "30s"
- name: RAMP_TIME
value: ""
Global blackhole chaos
When neither the DESTINATION_HOSTS nor the IP_ADDRESSES environment variables are provided, the experiment initiates a global blackhole chaos. This means all the network traffic will be blocked except for communication with a specific server infrastructure. You can specify the host for the server infrastructure using the SERVER_HOST environment variable, as demonstrated in the following example.
Following YAML snippet illustrates the use of this input variable.
apiVersion: litmuschaos.io/v1alpha1
kind: MachineChaosExperiment
metadata:
name: windows-blackhole-chaos-4ap
labels:
context: windows-blackhole-chaos
name: windows-blackhole-chaos-4ap
spec:
infraType: "windows"
steps:
- - name: windows-blackhole-chaos-4ap
tasks:
- name: windows-blackhole-chaos-4ap
infraId: ""
definition:
chaos:
fault: windows-blackhole-chaos
env:
- name: DESTINATION_HOSTS
value: ""
- name: IP_ADDRESSES
value: ""
- name: SERVER_HOST
value: ""
- name: DURATION
value: "30s"
- name: RAMP_TIME
value: ""