Pod JVM Solace Exception
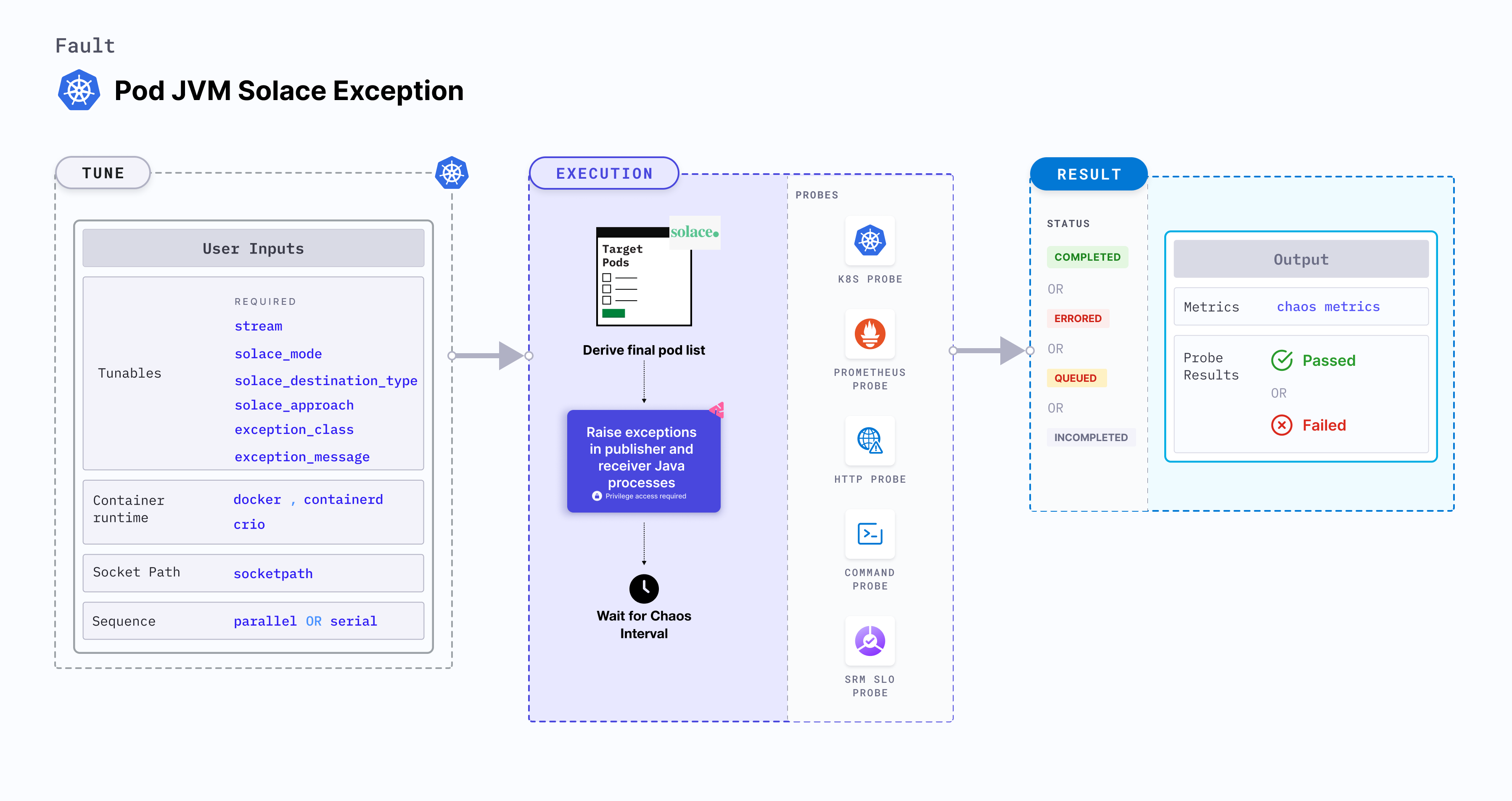
Pod JVM Solace Exception fault simulates Solace messaging failures by raising exceptions in both publisher and receiver Java processes running inside a Kubernetes pod. This helps test the application's behavior and resilience against messaging disruptions.
tip
JVM chaos faults use the Byteman utility to inject chaos faults into the JVM.
Use cases
Pod JVM Solace exception:
- Simulates Solace messaging exceptions to evaluate how the application handles messaging failures, assess system resilience under error conditions, and identify potential vulnerabilities in message processing and fault tolerance.
- Tests the impact of messaging exceptions on the end-user experience, ensuring the application behaves gracefully under Solace message delivery failures. This includes validating retries, fallback mechanisms, and error recovery strategies to maintain communication integrity.
- Ensures that the application can handle Solace messaging exceptions without critical failure. Test error-handling strategies, automatic recovery processes, and failover configurations to verify that the system remains operational despite messaging disruptions.
Mandatory tunables
| Tunable | Description | Notes |
|---|---|---|
| STREAM | The name of the topic or queue where message delivery will be simulated. | For more information, go to Parameters |
| SOLACE_MODE | The type of Solace messaging role | It can be either publisher or consumer. For more information, go to Parameters |
| SOLACE_DESTINATION_TYPE | Type of the solace destination | It can be either topic or queue. For more information, go to Parameters |
| SOLACE_APPROACH | Implementation approach used by the target application | It can be either jms, jcsmp, or java. For more information, go to Parameters |
| EXCEPTION_CLASS | The name of the exception class. | For more information, go to Parameters |
| EXCEPTION_MESSAGE | The exception message to be raised. | For more information, go to Parameters |
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| TOTAL_CHAOS_DURATION | Duration through which chaos is injected into the target resource. Should be provided in [numeric-hours]h[numeric-minutes]m[numeric-seconds]s format. | Default: 30s. Examples: 1m25s, 1h3m2s, 1h3s. For more information, go to duration of the chaos. |
| TRANSACTION_PERCENTAGE | The percentage of total calls to be targeted. | Supports percentage in (0.00,1.00] range. If not provided, it targets all matching calls. For more information, go to Parameters |
| POD_AFFECTED_PERCENTAGE | Percentage of total pods to target. Provide numeric values. | Default: 0 (corresponds to 1 replica). For more information, go to pods affected percentage. |
| JAVA_HOME | Path to the Java installation directory. | For example, /tmp/dir/jdk. |
| BYTEMAN_PORT | Port used by the Byteman agent. | Default: 9091. |
| CONTAINER_RUNTIME | Container runtime interface for the cluster. | Default: containerd. Support values: docker, containerd and crio. For more information, go to container runtime. |
| SOCKET_PATH | Path of the containerd or crio or docker socket file. | Default: /run/containerd/containerd.sock. For more information, go to socket path. |
| RAMP_TIME | Period to wait before and after injecting chaos. Should be provided in [numeric-hours]h[numeric-minutes]m[numeric-seconds]s format. | Default: 0s. Examples: 1m25s, 1h3m2s, 1h3s. For more information, go to ramp time. |
| SEQUENCE | Sequence of chaos execution for multiple target pods. | Default: parallel. Supports serial and parallel. For more information, go to sequence of chaos execution. |
| TARGET_CONTAINER | Name of the container subject to API header modification. | None. For more information, go to target specific container |
| TARGET_PODS | Comma-separated list of application pod names subject to pod HTTP modify body. | If not provided, the fault selects target pods randomly based on provided appLabels. For more information, go to target specific pods. |
| NODE_LABEL | It filters the target pods that are scheduled on nodes matching the specified NODE_LABEL. | For more information, go to node label. |
| LIB_IMAGE | Image used to inject chaos. | Default: harness/ddcr-faults:main-latest. For more information, go to image used by the helper pod. |
Parameters
The following YAML snippet illustrates the use of these tunables:
kind: KubernetesChaosExperiment
apiVersion: litmuschaos.io/v1alpha1
metadata:
name: pod-jvm-solace-exception
namespace: hce
spec:
tasks:
- definition:
chaos:
env:
- name: TOTAL_CHAOS_DURATION
value: "60"
# name of the topic or queue
- name: STREAM
value: "solace/chaos"
# the type of Solace messaging role
- name: SOLACE_MODE
value: "publisher"
# type of the solace destination
- name: SOLACE_DESTINATION_TYPE
value: "topic"
# implementation approach used by the target application
- name: SOLACE_APPROACH
value: "jms"
# name of the exception class
- name: EXCEPTION_CLASS
value: "IllegalArgumentException"
# provide the exception message
- name: EXCEPTION_MESSAGE
value: "CHAOS BOOM!"
# provide the transaction percentage
- name: TRANSACTION_PERCENTAGE
value: "50"