Manage access control for CCM perspective folders
You can now manage access to Perspective folders by assigning Resource Groups to users bound by the roles assigned to them.
Perform the following steps to restrict access to a Resource Group:
-
In Harness, go to Account Settings.
-
Select Access Control.
-
Select Roles.
-
Click + New Role to create a custom role with the following permissions. For example, CCM Custom Role.
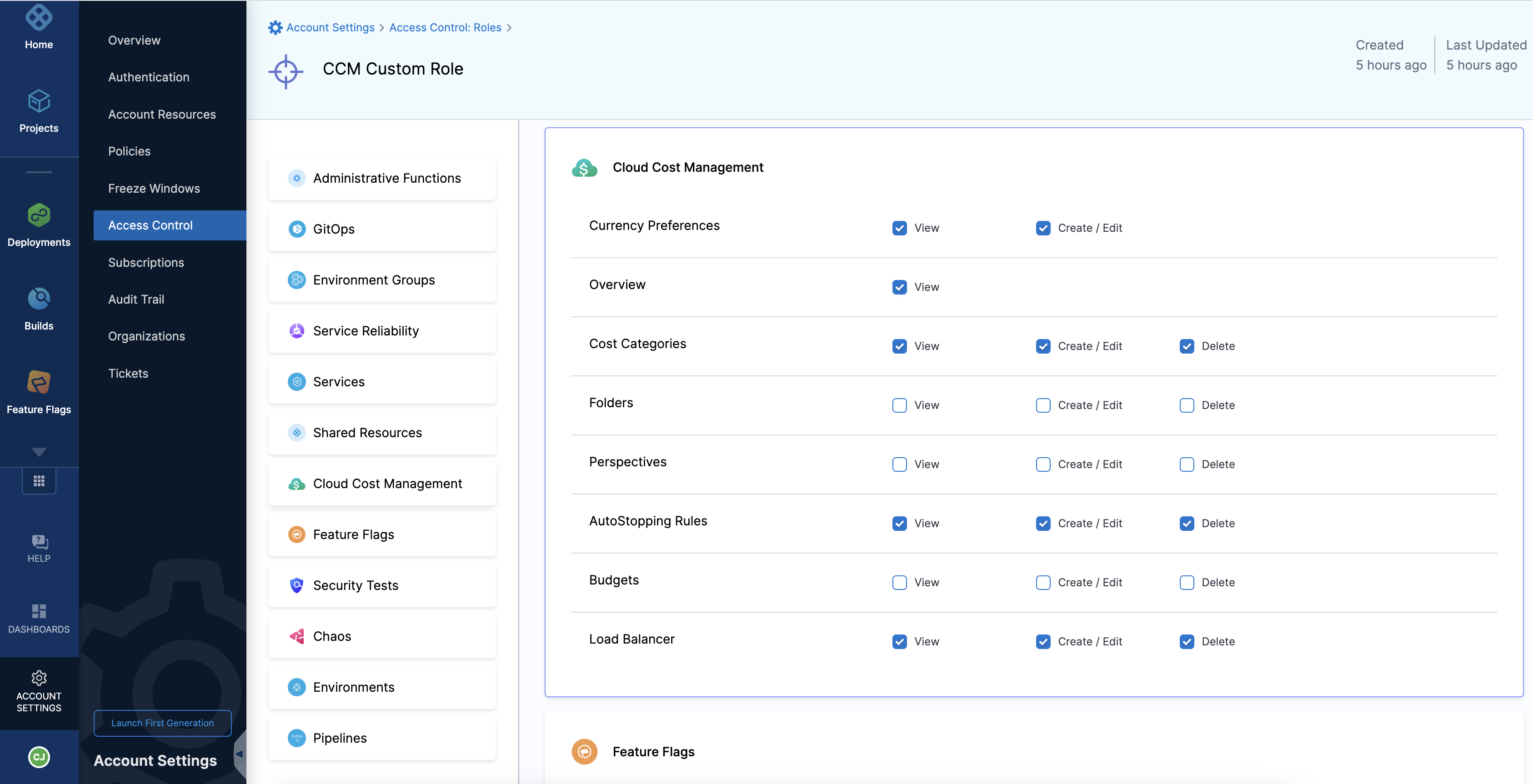
-
Create another custom role with a different set of permissions.
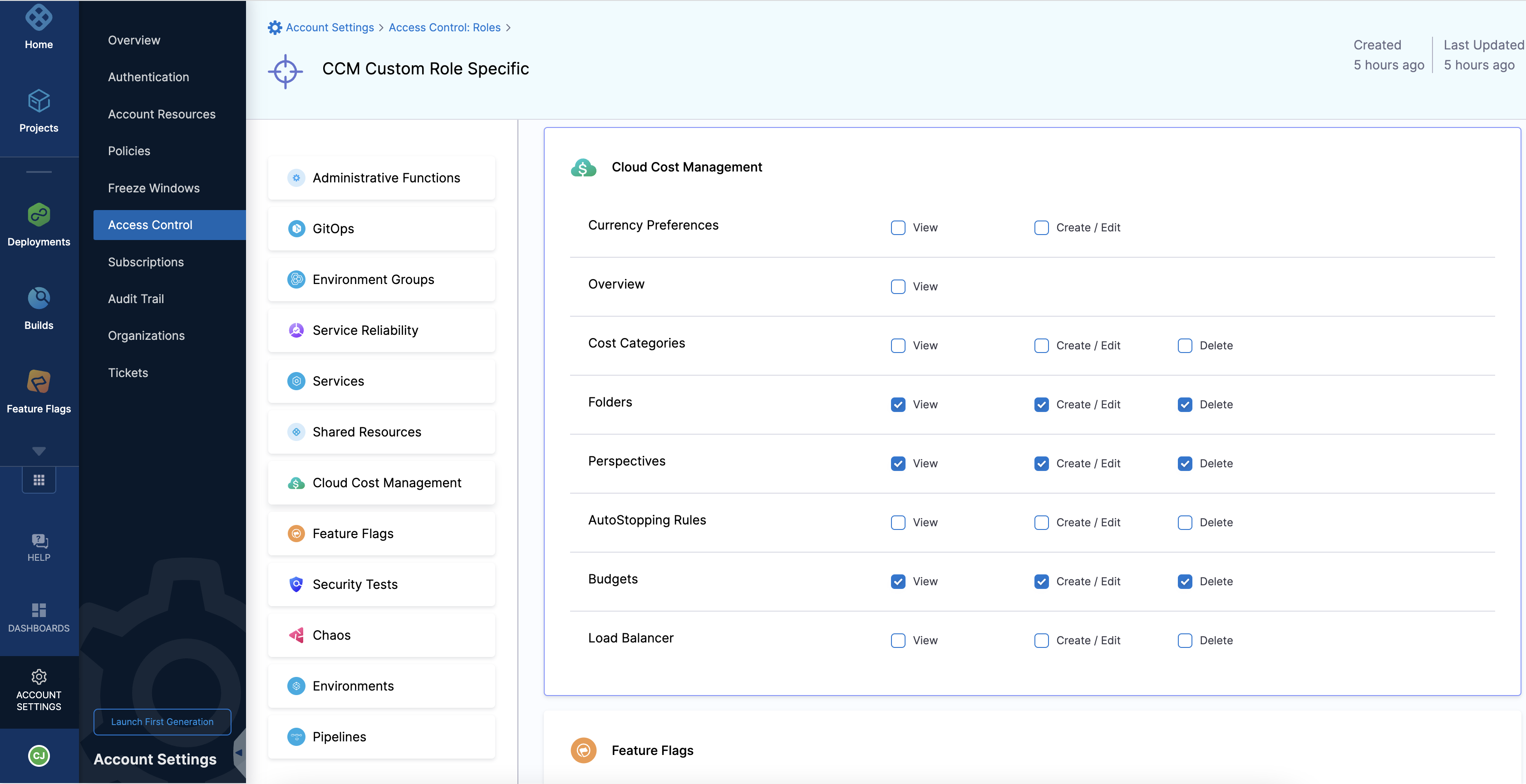
-
Select Resource Groups.
-
Click + New Resource Group to create a new resource group.
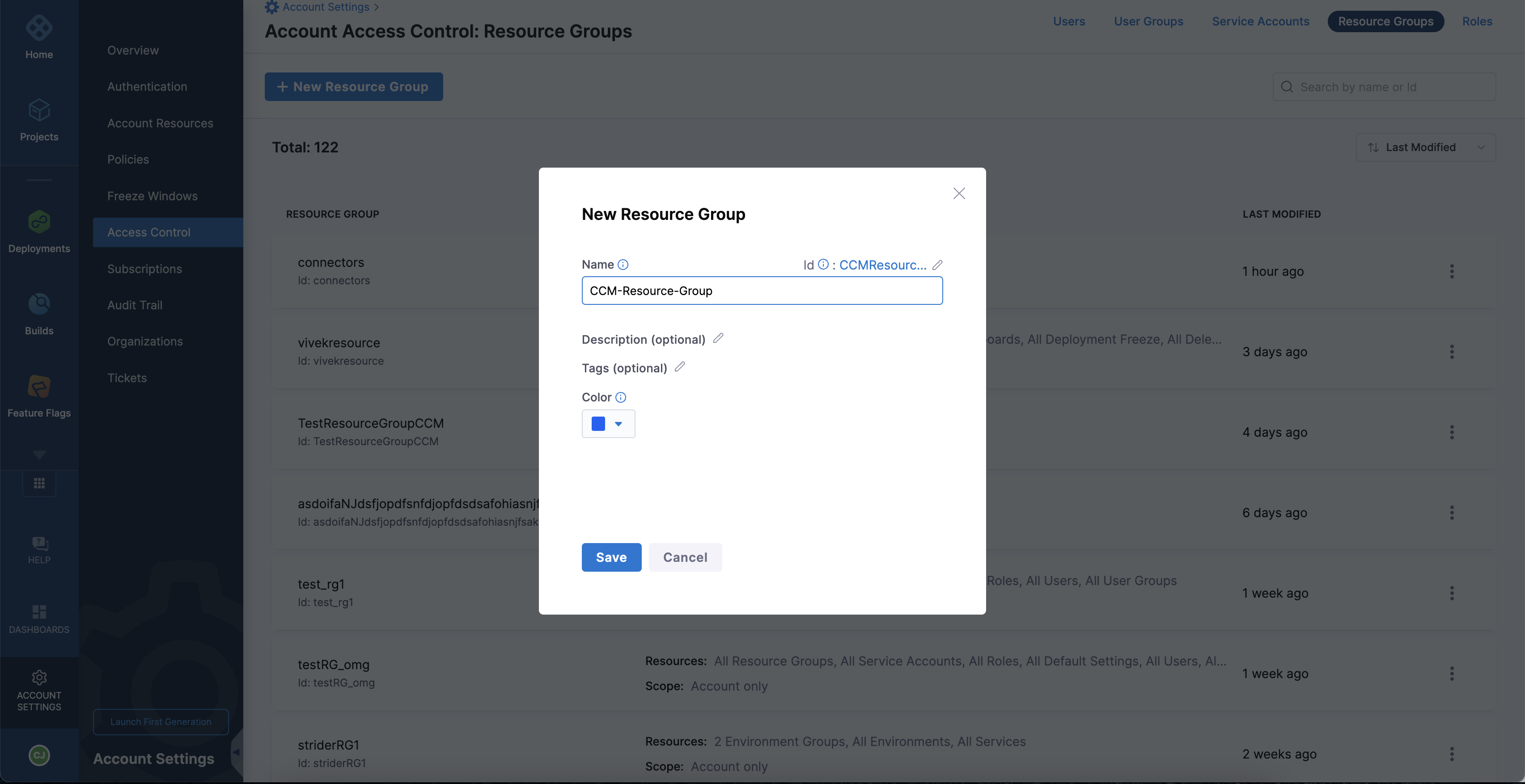
-
Select Account only in the Resource Scope dropdown list.
-
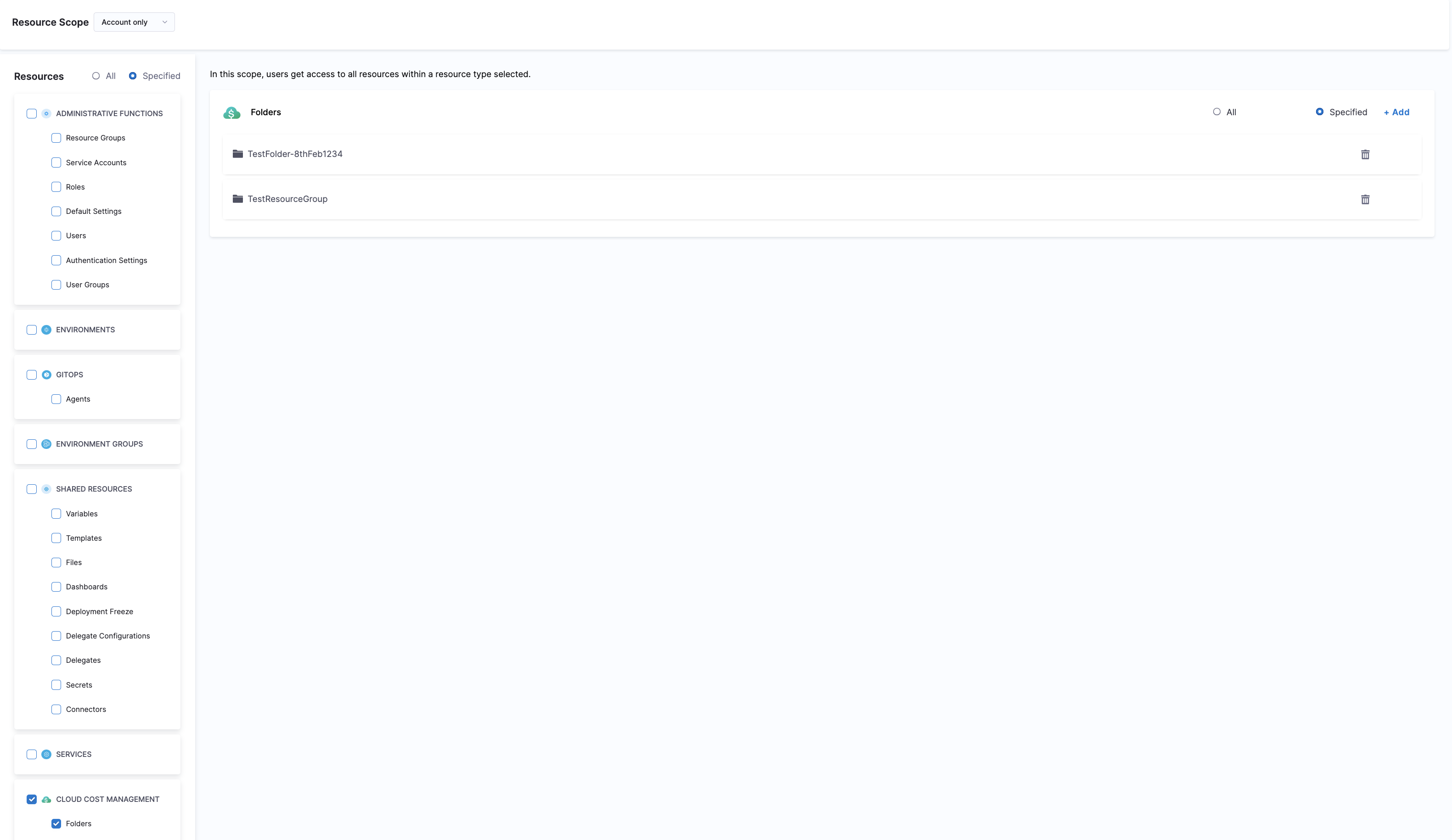
In the Resources pane, select Cloud Cost management > Folders.
-
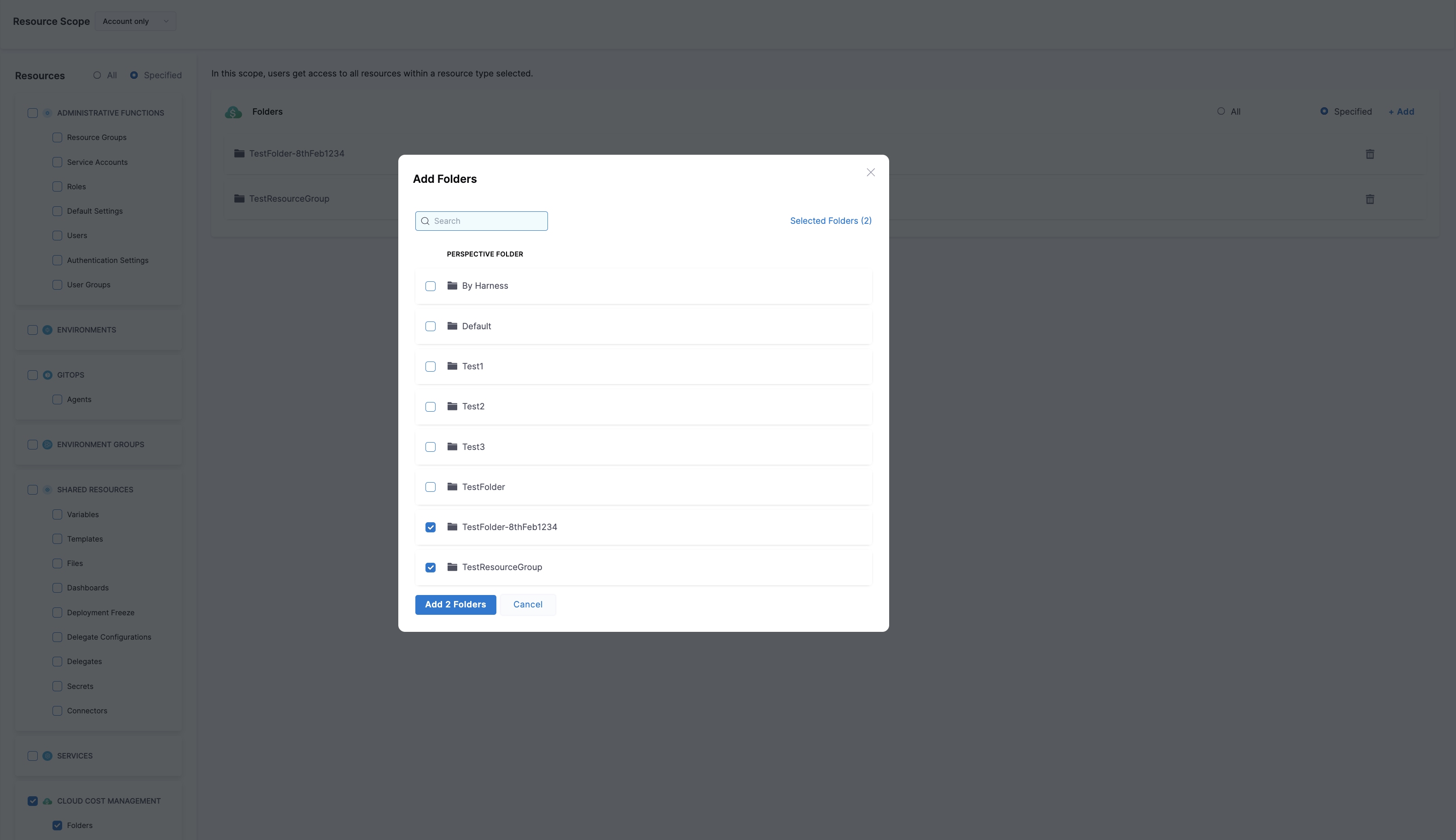
To restrict access to specific folders, select Specified and then click Add.
-
Add the selected folders and save the resource group settings.
-
To bind the Role with the Resource Group, go to the Users tab on the Access Control page.
-
Select the user you want to restrict access to.
-
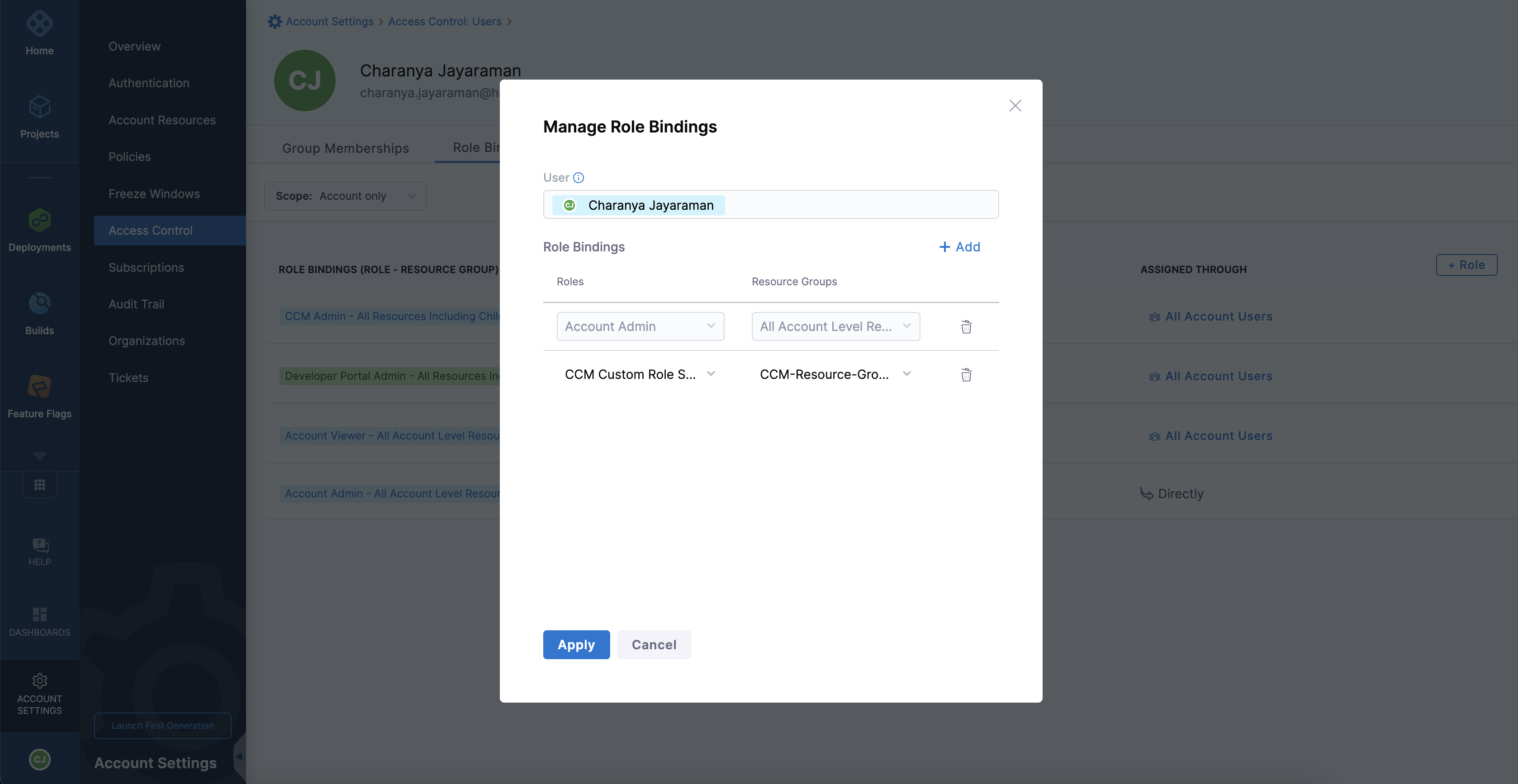
Click Manage Roles.
-
Click Add in the Manage Role Bindings window.
-
Select the Role and the newly created Resource Group to restrict access to folders.
-
Select another Role and Resource Group to provide access to all other resources.
-
Click Apply.
In Harness, the Perspectives page shows only the folders that the user has been granted access to. This means that the user cannot see or interact with any folder that they do not have permission to access.
A user can create Budgets for Perspectives only within the folders that they have been granted access to. For more information about Budgets, go to Create a Budget.
Similarly, on the Anomalies page, the visibility of the anomalies could be divided in four cases as explained in the table below:
| Use Case | Behaviour |
|---|---|
| User has both Anomalies View Permission & Perspective View Permission | User would be able to view all the anomalies based on Anomalies View Permission |
| User has Anomalies View Permission but does not have Perspective View Permission | User would be able to view all the anomalies based on Anomalies View Permission |
| User does not have Anomalies View Permission but has Perspective View Permission | Anomalies would be filtered based on Perspective View Permission which uses perspective rules for filtering |
| User do not have either Anomalies View Permission or Perspective View Permission | User won't be able to see any anomalies |
Similarly, on the Recommendations page, the visibility of the recommendations could be divided in four cases as explained in the table below:
| Use Case | Behaviour |
|---|---|
| User has both Recommendations View Permission & Perspective View Permission | User would be able to view all the recommendations based on Recommendations View Permission |
| User has Recommendations View Permission but does not have Perspective View Permission | User would be able to view all the recommendations based on Recommendations View Permission |
| User does not have Recommendations View Permission but has Perspective View Permission | Recommendations would be filtered based on Perspective View Permission which uses perspective rules for filtering |
| User do not have either Recommendations View Permission or Perspective View Permission | User won't be able to see any recommendations |
For more information, go to Recommendations.
A user with folder restrictions does not have permission to create new folders. This means that the user can only work within the existing folder structure that has been set up for them by an administrator.