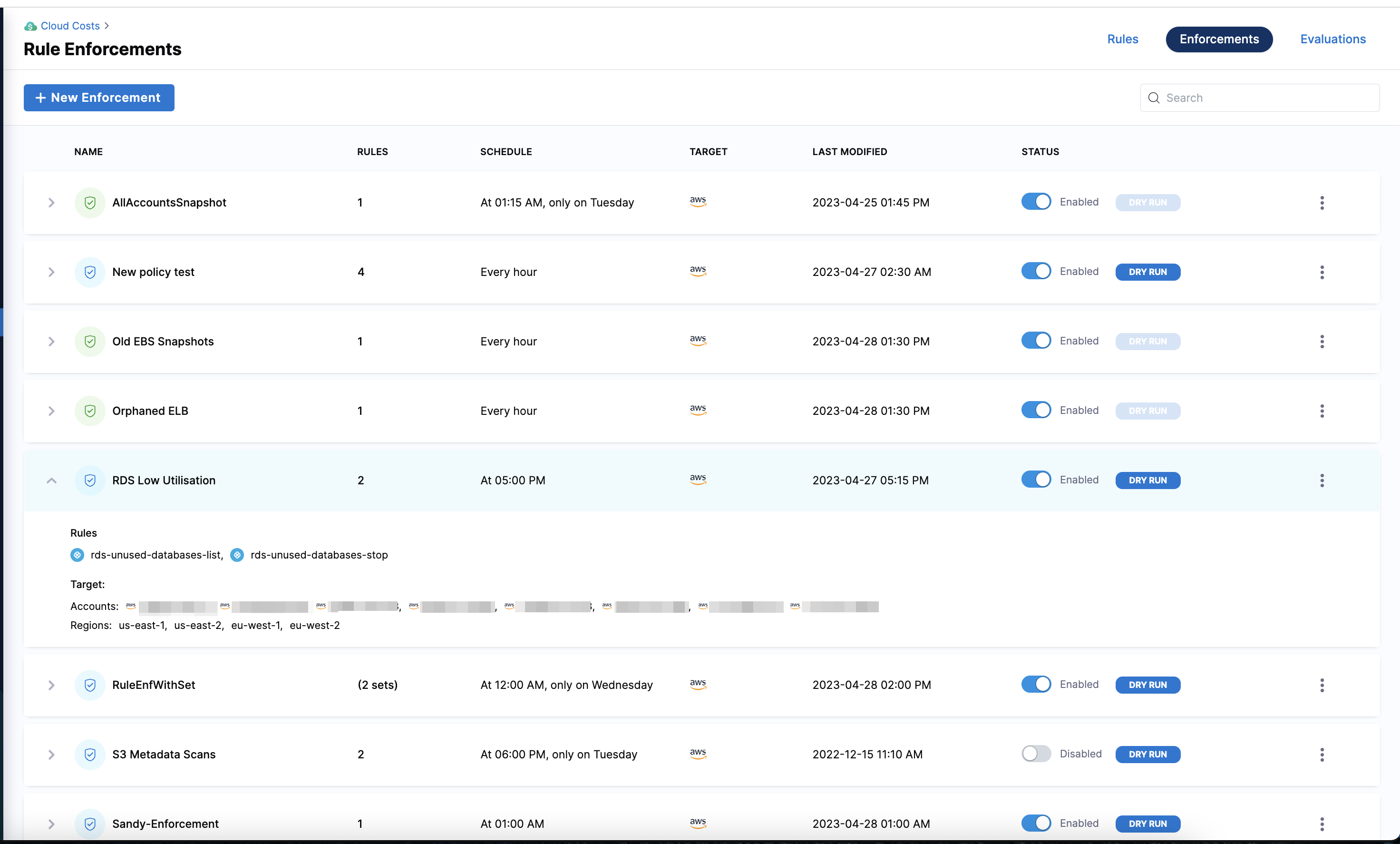
Manage access control for asset governance rules
RBAC enables effective governance of cloud assets by granting access and permissions strictly based on the roles and responsibilities of users, allowing them to execute only specific rules on specific cloud accounts.
Perform the following steps to restrict rule execution access:
Create roles
- In the Harness application, go to Account Settings.
- Select Access Control.
- Select Roles.
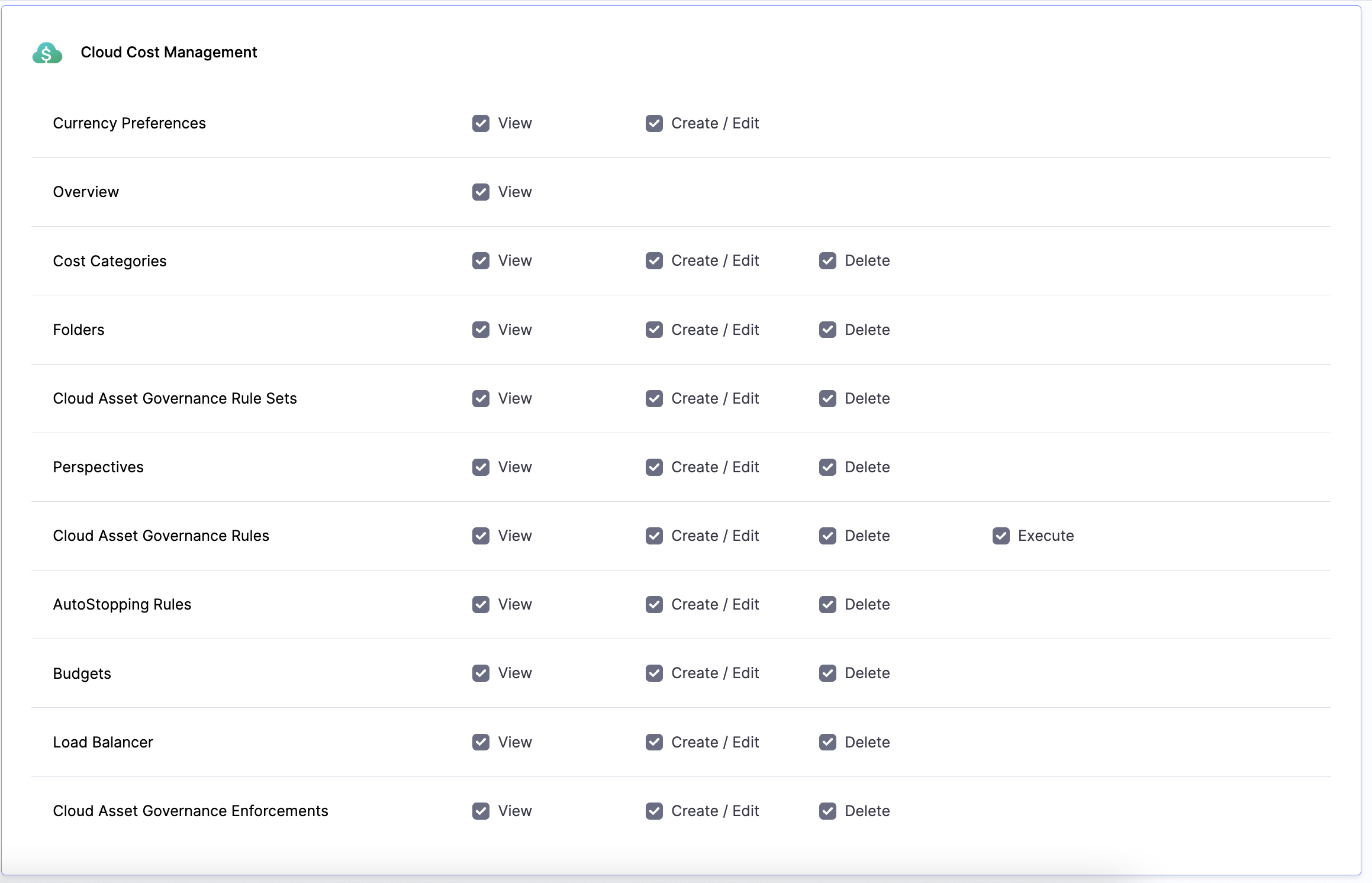
- Select + New Role to create a custom role with restricted permissions as shown in the following screenshot.

- Create another role with
Executepermissions to enable the execution of the governance rules.
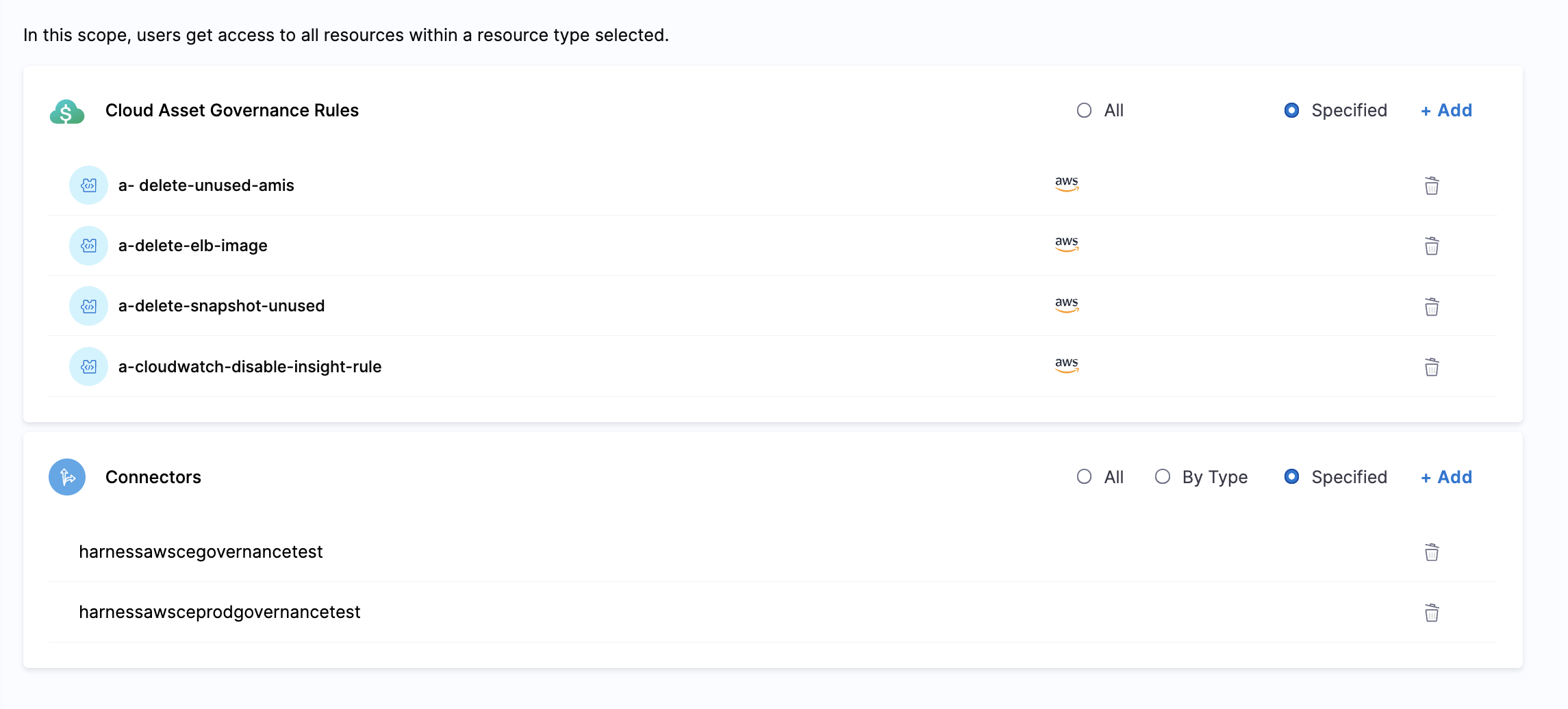
Create resource groups
Create a new resource group to bind with this role. You could create a resource group with specific rules and connectors that you want to allow access to. Connectors allow you to execute rules in the cloud account tied to them.
-
Select Resource Groups.
-
Click + New Resource Group to create a new resource group. For example, RBAC GOV.
-
Select Account only in the Resource Scope dropdown list.
-
In the Resources pane, select Cloud Cost management > Cloud Asset Governance Rules.
-
To restrict access to specific rules, select Specified, and then select Add.
-
In the Resources pane, select Shared Resources > Connectors.
-
To restrict access to specific cloud accounts, select Specified, and then select Add.
The following screenshot is an example of a resource group with limited number of rules and accounts:
Bind the roles with the resource groups
- To bind the Role with the Resource Group, go to the Users tab on the Access Control page.
- Select the user you want to restrict access to.
- Select Manage Roles.
- Select Add in the Manage Role Bindings window.
- Select the Role with permissions to execute rules, and the newly created resource group (RBAC GOV) to allow access only to certain rules and accounts.
- Add another role binding. Select the role without permission to execute rules, and then select
All resources including child scopesfrom the Resource Groups dropdown.
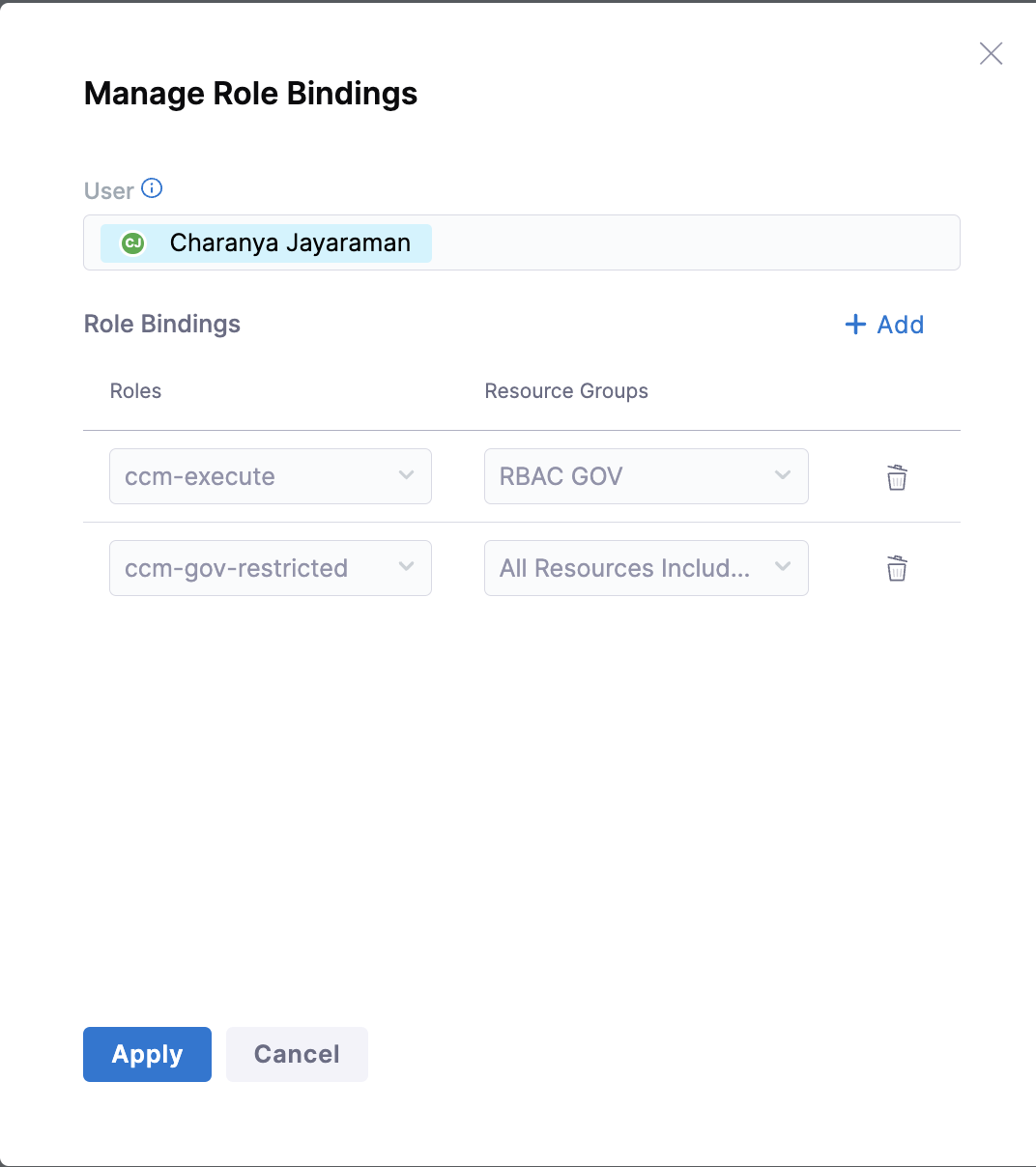
In the given example, the ccm-execute role allows the user to execute governance rules on the RBAC GOV resource group (specific resources), and the ccm-gov-restricted role restricts the user from executing the governance rules.
Verifying permissions
-
On the Asset Governance Rules page, you can see that the Enforce rule option is enabled only for those rules included in the resource group. The rest are disabled. When you hover over a rule for which you have no
Executepermission, a message appears as shown in the following screenshot: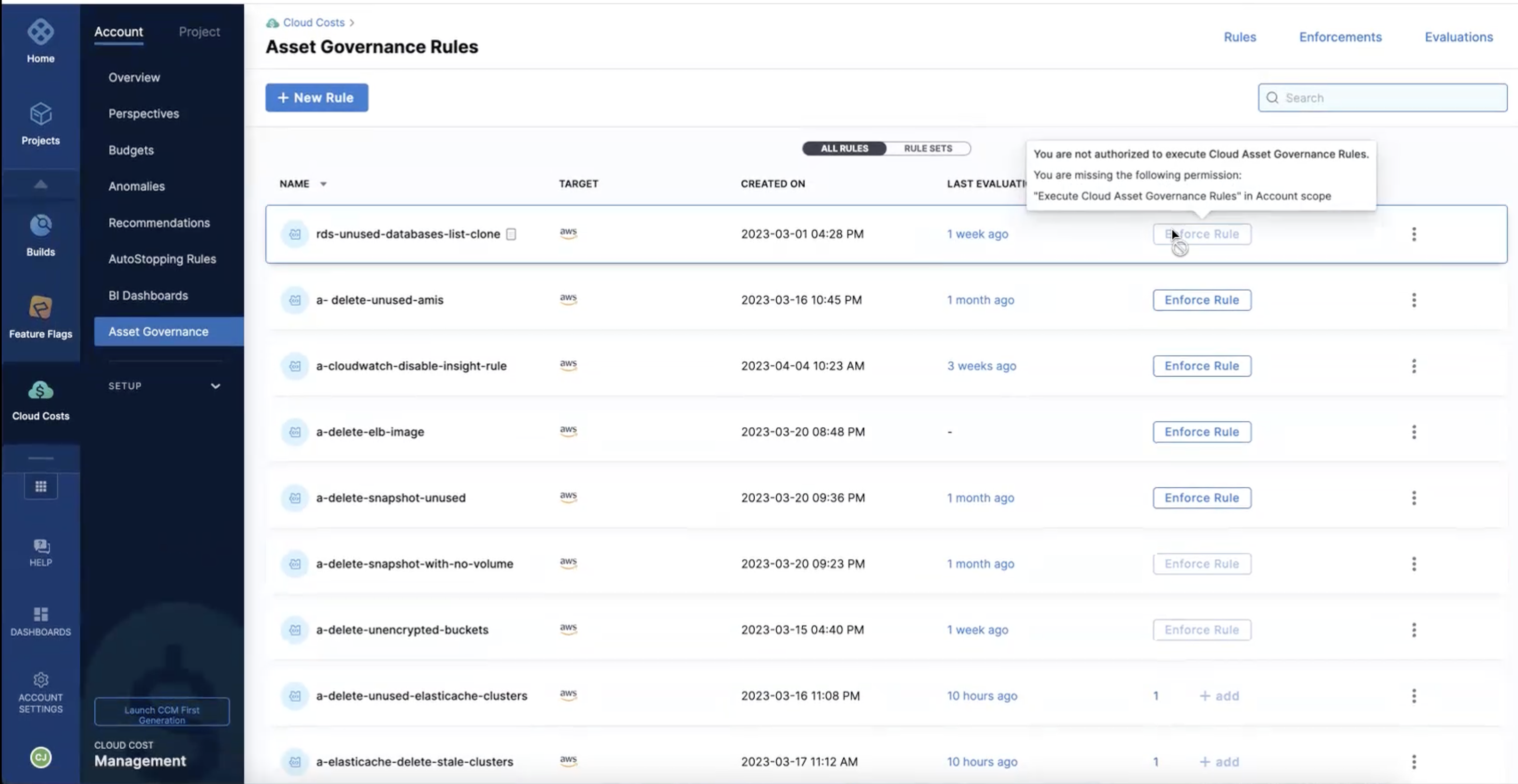
-
You are not allowed to edit or delete the rules without the
Executepermission. However, you can clone these rules. -
You can create a rule set only with the rules for which you have permissions.
-
When editing an enforcement, you must have the necessary permissions for all the rules and target accounts that you want to include in the enforcement.