Manage roles
Roles are an RBAC component that contain a set of permissions. Roles define what actions, such as viewing, creating, editing, or deleting, can be taken on Harness resources. When you assign a role to a user, user group, or service account, the permissions defined in the role are granted to the target user, group, or service account.
Harness includes some built-in roles, and you can create custom roles, which are useful for limited and fine-grained access control.
Roles are scope-specific, and you can create them at any scope. For example, a role created at the project scope is only available in that project.
Roles and resource groups work together
Roles are applied together with resource groups to create a complete set of permissions and access. For example:
- You can assign the Organization Admin role with a resource group that is limited to specific projects or specific organizations.
- You can assign the Pipeline Executor role with a resource group that only allows access to specific pipelines, rather than all pipelines in the project.
RBAC is additive. The total expanse of a user/service account's permissions and access is the sum of all the roles and resource groups from all user groups they belong to, as well as any roles and resource groups assigned directly to them as an individual user/service account.
It is important to follow the principle of least privilege (PoLP). This is a security principle that means users are granted the absolute minimum access/permissions necessary to complete their tasks and nothing more.
While Harness includes some built-in roles and resource groups, to ensure the least privilege, consider:
- Being selective in the way you apply roles and resource groups.
- Creating your own roles and resource groups as needed for refined access control.
Built-in roles
Harness includes several built-in roles. To examine the permissions assigned to these roles, view them in Harness:
-
In Harness, go to the scope where the role exists.
- To view a role at the account scope, select Account Settings, and then select Access Control.
- To view a role at the organization scope, go to Account Settings, select Organizations, select the relevant organization, and then select Access Control.
- To view a role at the project scope, go to Projects, select the relevant project, and then select Access Control.
-
Select Roles in the header.
-
Select the role you want to view. For details about specific permissions, go to the Permissions reference.
Built-in roles can be hidden. This functionality is behind the feature flags PL_HIDE_PROJECT_LEVEL_MANAGED_ROLE, PL_HIDE_ORGANIZATION_LEVEL_MANAGED_ROLE, and PL_HIDE_ACCOUNT_LEVEL_MANAGED_ROLE. Contact Harness Support to enable the features.
Platform roles
These roles are not specific to any modules. They are for administration and oversight of an entire Harness account, organization, or project. They also provide access to cross-module components, such as dashboards and pipelines.
| Role | Scope |
|---|---|
| Account Admin | Account |
| Account Viewer | Account |
| Dashboard Admin | Account |
| Dashboard Viewer | Account |
| Billing Admin | Account |
| Organization Admin | Organization |
| Organization Viewer | Organization |
| Project Admin | Project |
| Project Viewer | Project |
| Pipeline Executor | Project |
Module-specific roles
Harness creates these roles for you depending on the modules you use. These roles exist at all scopes.
- Feature Flag Manage Role
- CET Admin
- Chaos Admin
- CCM Admin
- CCM Viewer
- Security Testing AppSec Role
- Security Testing Developer Role
- GitOps Admin Role
- Code Admin (for Harness Code Repository)
Manage roles in Harness
To manage roles in Harness, you need a role, such as Account Admin, that has permission to view, create/edit, and delete roles.
Create a role
-
In Harness, go to the scope where you want to create the role.
- To create a role at the account scope, select Account Settings, and then select Access Control.
- To create a role at the organization scope, go to Account Settings, select Organizations, select the relevant organization, and then select Access Control.
- To create a role at the project scope, go to Projects, select the relevant project, and then select Access Control.
-
Select Roles in the header, and then select New Role.
-
Enter a Name for the role. Description and Tags are optional.
-
Select Save.
-
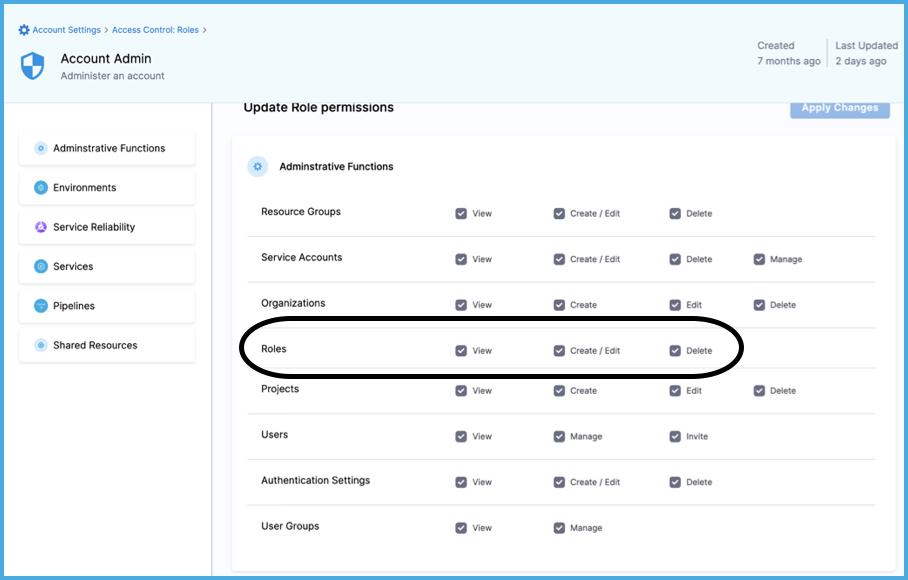
Select permissions for the role.
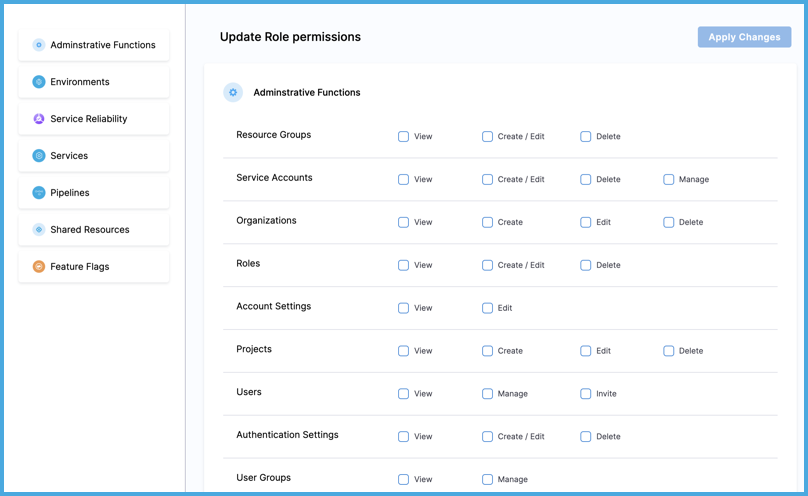
-
Select Apply Changes.
Edit a role
-
In Harness, go to the scope where the role exists.
- To edit a role at the account scope, select Account Settings, and then select Access Control.
- To edit a role at the organization scope, go to Account Settings, select Organizations, select the relevant organization, and then select Access Control.
- To edit a role at the project scope, go to Projects, select the relevant project, and then select Access Control.
-
Select Roles in the header.
-
Locate the role you want to edit.
-
Select More options (⋮) on the role card, and then select Edit.
-
Edit the role's name, description, or tags, if needed, and then select Save.
-
Edit the role's permissions, and then select Apply Changes. For details about specific permissions, go to the Permissions reference.
Delete a role
-
In Harness, go to the scope where the role exists.
- To delete a role at the account scope, select Account Settings, and then select Access Control.
- To delete a role at the organization scope, go to Account Settings, select Organizations, select the relevant organization, and then select Access Control.
- To delete a role at the project scope, go to Projects, select the relevant project, and then select Access Control.
-
Select Roles in the header.
-
Locate the role you want to delete.
-
Select More options (⋮) on the role card, and then select Delete.
Continue RBAC configuration
Creating roles is one part of configuring RBAC in Harness.
Roles, which grant permissions, work alongside resource groups, which grant access.
After configuring roles and resource group, you assign them to users, user groups, and service accounts.
Add permissions access to specific resources selected via Custom Resource Group
You can do role bindings to a user and attach the user to a specific resource group at the Account, Project, or Organization scope.
To add new users to a custom Resource Group with role bindings, do the following:
- In Harness, go to Account Settings, Organization Settings, or Project Settings, depending on the scope at which you want to add new users to a custom Resource Group and do role bindings.
- Under Access Control, select Resource Groups.
- Create a new Resource Group, select the desired resource types, and click Save.
- Return to Account Settings. Under Access Control, select Users.
- Click New User, enter the user's email, then, under Role Bindings, select Add.
- Under Roles, click Select a role, then choose Account Admin or any custom role with all permissions selected for the resources in the resource group from the dropdown.
- Under Resource Groups, click All Resources Including and select your Resource Group.
- Click Apply to send an invitation to the user's email. After the user accepts the invite, the role-binding process is complete.
The user can now sign in to their account and access only those resources allowed in the resource groups with their Account Admin permissions.
To add role bindings to an existing user:
- In Harness, go to Account Settings, Organization Settings, or Project Settings, depending on the scope at which you want to add new users to a custom Resource Group and do role bindings.
- Under Access Control, select Resource Groups.
- Create a new Resource Group, select the desired resource types, and then select Save.
- Return to Account Settings. Under Access Control, select Users.
- Search for the user to whom you want to assign the Account Admin role or any custom role with all permissions selected for the resources in the resource group, and then select the user.
- Go to the Role Bindings tab, then select Manage Role Bindings.
- Under Role Bindings, select Add.
- Under Roles, click Select a role, and then select Account Admin.
- Under Resource Groups, select All Resources Including, and then select your Resource Group.
- Select Apply. You will receive a notification stating Role Assignments updated successfully, and the role binding process is complete.
The user can now sign in to their account and access only those resources allowed in the resource groups with their Account Admin permissions.
Reuse roles across scopes
You can further streamline role management by reusing roles across scopes in Harness, simplifying access control configuration across your account, organizations, and projects. By creating a role at the account level, you can easily assign it to users, user groups, or service accounts at more granular levels like the organization or project scope.
You can only reuse custom roles across scopes. Built-in roles are not reusable.
This feature is behind the feature flag PL_ROLE_REUSABILITY_ACROSS_CHILD_SCOPES. Contact Harness Support to enable the feature.
Example: Reusing roles across scopes
This example walks through reusing a role across scopes. The role is created at the account scope and then assigned to users at the organization and project scopes.
Create a role at the account scope
- In Harness, go to Account Settings, and then select Access Control.
- Select Roles in the header, and then select New Role.
- For Name, enter
TEST_ROLE. Description and Tags are optional. - Select Save.
- Select the following permissions:
- For Pipelines, select Execute.
- Select Apply Changes.
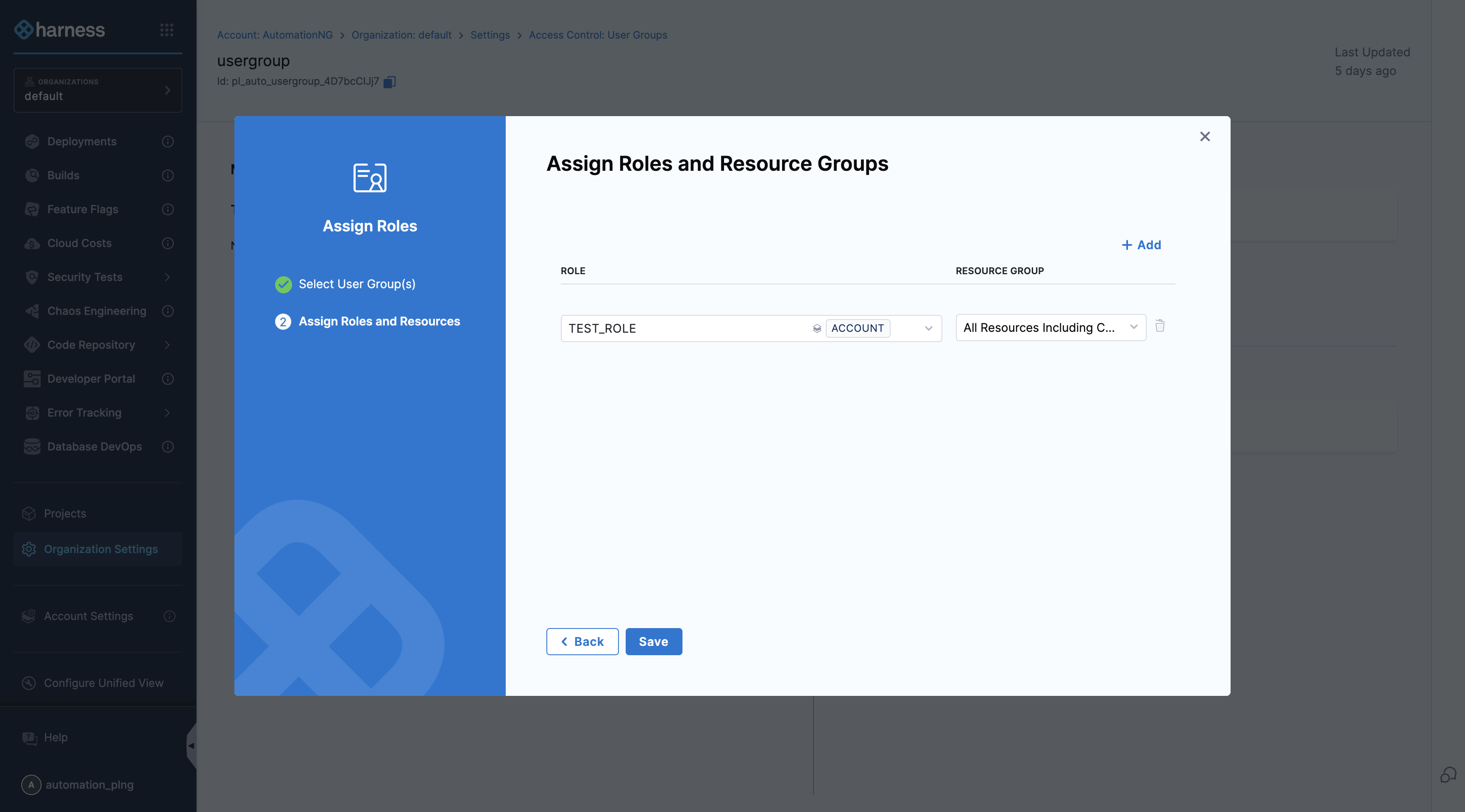
Assign the role to users at the organization scope
- In Harness, go to Account Settings, select Organizations, select the relevant organization, and then select Access Control.
- Select User Groups in the header, and then select the User Group you want to assign the role to.
- Select Manage Role Bindings.
- Under Role Bindings, select Add.
- Under Select an Existing Role, select Account in the header and then select the role you want to assign.
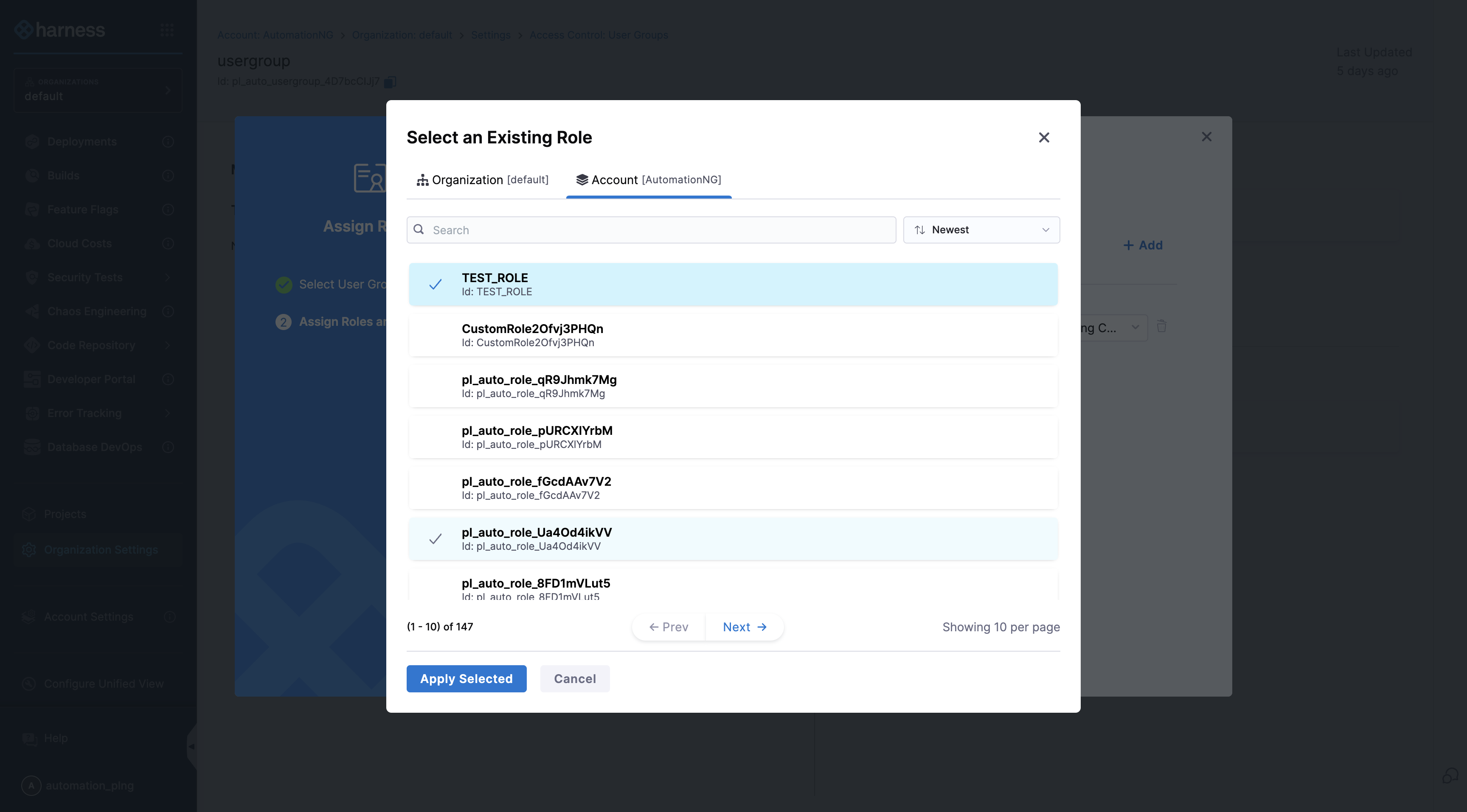
- Select Apply Selected.
- Select Save.
View principals assigned to a role
This feature is behind the feature flag PL_ROLE_REUSABILITY_ACROSS_CHILD_SCOPES. Contact Harness Support to enable the feature.
To view principals assigned to a specified role, navigate to the appropriate scope (account, organization, or project) and follow the steps below.
Note: The steps below use the Account scope and Account Admin role as an example. You can follow the same steps for the Organization and Project scopes.
- Interactive
- Manual
- Navigate to the scope’s Settings → Access Control → Roles.
- Locate or search for the specific role.
- Click on the role, switch to the Assigned to tab.
- By default, the "Users" list appears for the assigned role. You can also switch to the "User Groups" or "Service Accounts" tabs to view principals for the specified role.