Add a CyberArk Conjur custom secret manager
You can link CyberArk Conjur to Harness and use it to store any sensitive data you use in Harness, including secrets.
Before you begin
You need an understanding of:
CyberArk Conjur secret manager permission requirements
- Make sure you have Create/Edit permissions for secrets.
- Make sure you have Create/Edit permissions for connectors.
Step 1: Create a Secret Manager Template
You can create a Secret Manager Template at the account, org, or project scope.
This topic shows you how to create a Secret Manager Template at the Project scope.
-
In your Harness Account, go to your Project.
-
Select Project Settings, then under Project-level resources, select Templates.
-
Select New Template, then select Secret Manager.
-
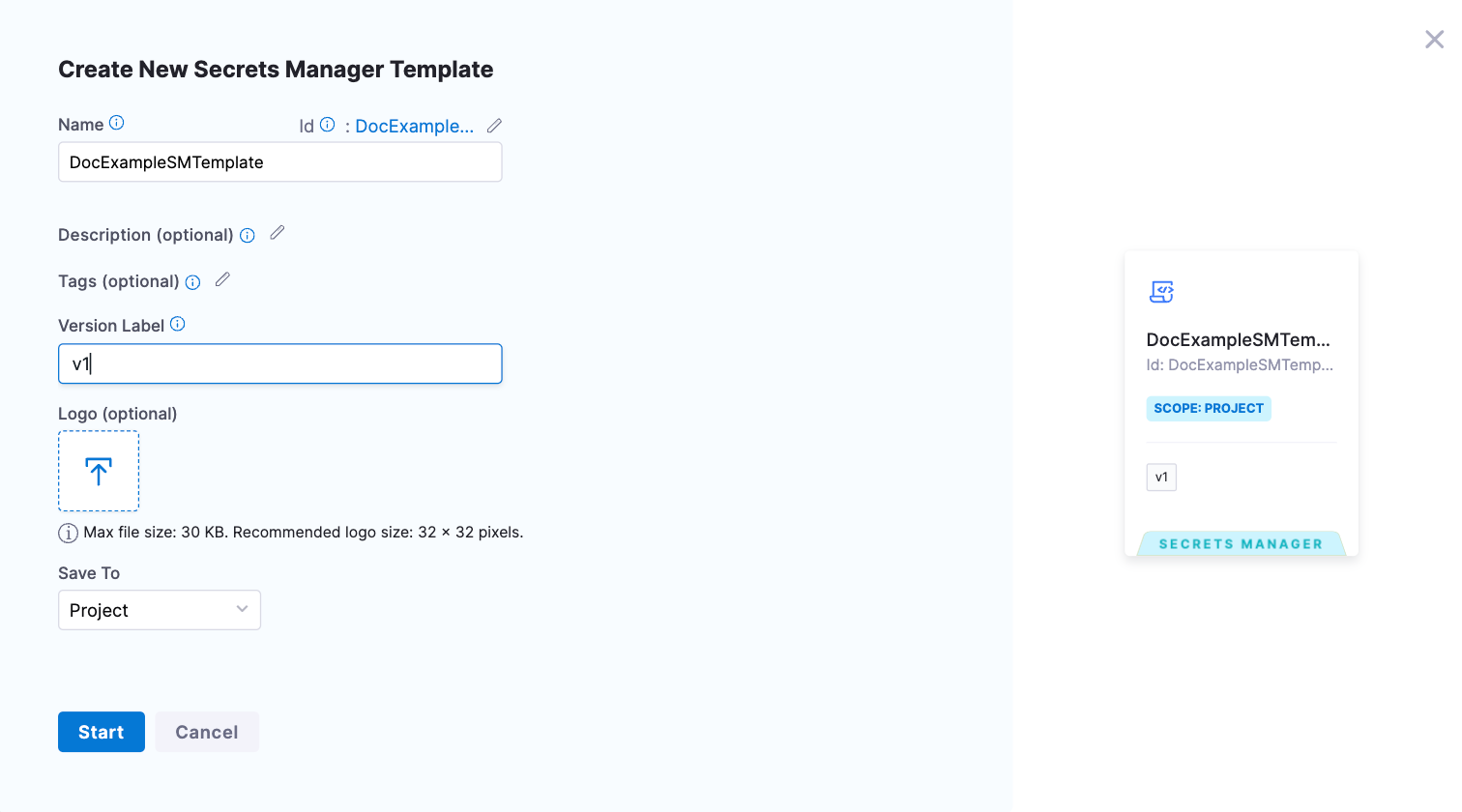
Enter a Name for your template.
-
(Optional) In Description, select the pencil icon and enter a description.
-
(Optional) In Tags, select the pencil icon and assign a tag.
-
Enter a Version Label.
-
(Optional) Select the upload icon and upload a Logo.
-
Under Save To, select Project, then select Start.
-
Select your Script Type, then select your script location.
-
Enter the following script in Script.
CONJUR_APPLIANCE_URL='<+spec.environmentVariables.CONJUR_APPLIANCE_URL>'
HOST_ID='<+secretManager.environmentVariables.HOST_ID>'
API_KEY='<+secrets.getValue(<+spec.environmentVariables.API_KEY_SECRET_ID>)>'
AUTHENTICATOR='<+secretManager.environmentVariables.AUTHENTICATOR>'
ACCOUNT='<+secretManager.environmentVariables.ACCOUNT>'
KIND='variable'
IDENTIFIER='<+secretManager.environmentVariables.IDENTIFIER>'
# Authenticate first to get an access token
# ref: https://docs.conjur.org/Latest/en/Content/Developer/Conjur_API_Authenticate.htm
FULL_AUTH_URL="$CONJUR_APPLIANCE_URL/$AUTHENTICATOR/$ACCOUNT/$HOST_ID/authenticate"
ACCEPT_HEADER='Accept-Encoding: base64'
ACCESS_TOKEN=$(curl --request POST --header "$ACCEPT_HEADER" --data "$API_KEY" "$FULL_AUTH_URL")
# Use the token to retrieve a secret
RETRIEVAL_URL="$CONJUR_APPLIANCE_URL/secrets/$ACCOUNT/$KIND/$IDENTIFIER"
AUTH_HEADER="Authorization: Token token=\"${ACCESS_TOKEN}\""
ACCEPT_HEADER_JSON="Accept: application/json"
secret="$(curl --request GET $RETRIEVAL_URL --header "$AUTH_HEADER" --header "$ACCEPT_HEADER_JSON")"
# Check the exit status of the curl command
if [ $? -ne 0 ]; then
exit 1
fi
- Select Configuration, then Select Add Input Variable.
- Set up the following input variables.
CONJUR_APPLIANCE_URL- Type: String
- Value:
<+input>
HOST_ID- Type: String
- Value:
<+input>
API_KEY_SECRET_ID- Type: String
- Value:
conjur_api_key
AUTHENTICATOR- Type: String
- Value:
<+input>
ACCOUNT- Type: String
- Value:
<+input>
IDENTIFIER- Type: String
- Value:
<+input>
- Select Save.
For detailed steps to create a Secret Manager Template, go to Create a Secret Manager Template.
Example YAML
template:
name: Conjur
identifier: Conjur
versionLabel: "1.0"
type: SecretManager
tags: {}
icon:
spec:
shell: Bash
delegateSelectors: []
source:
type: Inline
spec:
script: |-
CONJUR_APPLIANCE_URL='<+spec.environmentVariables.CONJUR_APPLIANCE_URL>'
HOST_ID='<+secretManager.environmentVariables.HOST_ID>'
API_KEY='<+secrets.getValue(<+spec.environmentVariables.API_KEY_SECRET_ID>)>'
AUTHENTICATOR='<+secretManager.environmentVariables.AUTHENTICATOR>'
ACCOUNT='<+secretManager.environmentVariables.ACCOUNT>'
KIND='variable'
IDENTIFIER='<+secretManager.environmentVariables.IDENTIFIER>'
# Authenticate first to get an access token
# ref: https://docs.conjur.org/Latest/en/Content/Developer/Conjur_API_Authenticate.htm
FULL_AUTH_URL="$CONJUR_APPLIANCE_URL/$AUTHENTICATOR/$ACCOUNT/$HOST_ID/authenticate"
ACCEPT_HEADER='Accept-Encoding: base64'
ACCESS_TOKEN=$(curl --request POST --header "$ACCEPT_HEADER" --data "$API_KEY" "$FULL_AUTH_URL")
# Use the token to retrieve a secret
RETRIEVAL_URL="$CONJUR_APPLIANCE_URL/secrets/$ACCOUNT/$KIND/$IDENTIFIER"
AUTH_HEADER="Authorization: Token token=\"${ACCESS_TOKEN}\""
ACCEPT_HEADER_JSON="Accept: application/json"
secret="$(curl --request GET $RETRIEVAL_URL --header "$AUTH_HEADER" --header "$ACCEPT_HEADER_JSON")"
# Check the exit status of the curl command
if [ $? -ne 0 ]; then
exit 1
fi
environmentVariables:
- name: CONJUR_APPLIANCE_URL
type: String
value: <+input>
- name: HOST_ID
type: String
value: <+input>
- name: API_KEY_SECRET_ID
type: String
value: <+input>
- name: AUTHENTICATOR
type: String
value: <+input>
- name: ACCOUNT
type: String
value: <+input>
- name: IDENTIFIER
type: String
value: <+input>
outputVariables: []
onDelegate: true
Step 2: Add a Custom Secret Manager
You can add a Custom Secret Manager at the account, org, and project scope.
To do this, go to Project, Organization, or Account settings.
This topic shows you how to add a Custom Secret Manager in the project scope.
-
In your Harness Account, go to your Project.
-
In Project Setup, select Connectors and then select New Connector.
-
In Secret Managers, select Custom Secret Manager. The Custom Secret Manager settings open.

-
Enter a Name for your Custom Secret Manager. Select Continue.
-
Select Select Template. The Template Library appears with all the Secret Manager Templates listed.
-
Select the desired scope and select a your CyberArk Conjur Secret Manager template from the Template Library.
You can also search for a specific Secret Manager Template by entering its name in Search. Once you select the Secret Manager Template, the details are displayed in the Template Studio.
-
Select Use Template.
-
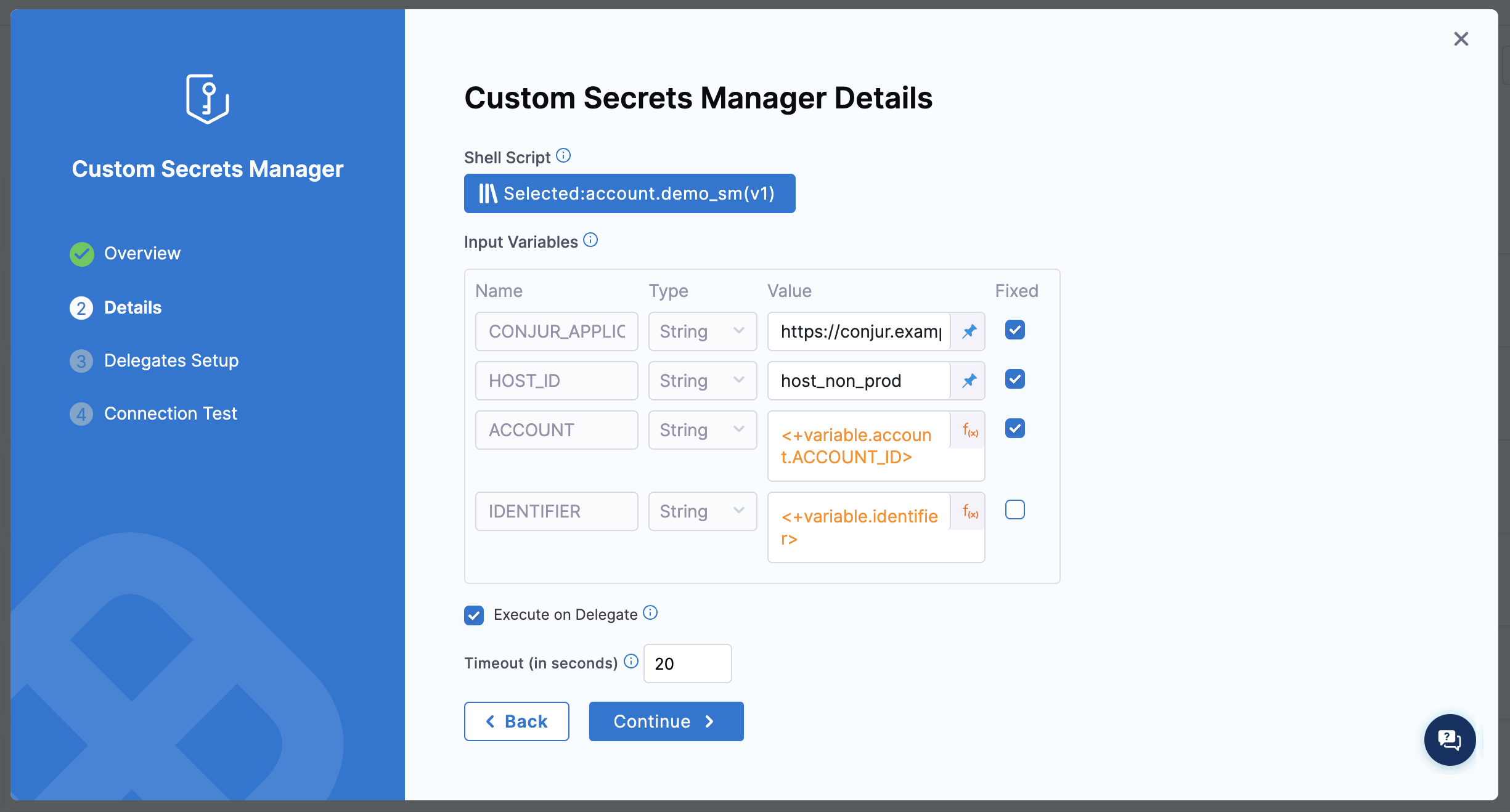
Enter values for the required Input Variables. Harness allows you to use Fixed Values and Runtime Inputs.
-
Select Fixed for the
CONJUR_APPLIANCE_URL,HOST_ID,AUTHENTICATOR,API_KEY_SECRET_ID, andACCOUNT. -
The
API_KEY_SECRET_IDshould be an identifier for a Harness Secret, to be used for authenticating with Conjur. Create the secret using any secret manager other than Conjur. Based on where you create the secret, this can be in the format ofaccount.secretid,org.secretid, or justsecretid. -
The following values are used to authenticate with Conjur using this API URL format:
$CONJUR_APPLIANCE_URL/$AUTHENTICATOR/$ACCOUNT/$HOST_ID/authenticate -
The following values are used to fetch a secret from Conjur using this API URL format:
$CONJUR_APPLIANCE_URL/secrets/$ACCOUNT/$KIND/$IDENTIFIER -
Set the
IDENTIFIERto not be Fixed, and provide an example secret identifier to be used for testing the connection.The
IDENTIFIERshould be in the following format:<vault>/<lob-user>/<safe>/<account>/<property>
-
-
Select Continue.
-
In Delegates Setup, enter Selectors for specific Delegates that you want to allow to connect to this Connector. Select Save and Continue.
-
In Connection Test, select Finish after your connection is successful.
Step 3: Use the Custom Secret Manager
Create an Encrypted Text using the Custom Secrets Manager you created earlier. Enter the name and values of all the Input Variables defined while creating the Shell Script Template.
For more information on creating Encrypted Text Secret, go to Add Encrypted Text.