Harness SCA Scanner
Harness native Software Composition Analysis (SCA) scanner integrates directly within your CI/CD pipelines to scan container images to find vulnerabilities in OS packages and libraries installed in the image - without requiring external scanners or connectors.
With one-click configuration, Harness automatically manages authentication and licensing, while providing built-in data flow visualization, reachability analysis to determine whether a vulnerability is exploitable, and AI-powered remediation to help developers quickly understand and fix issues.
The SCA step works natively within STO, with all findings unified and visible alongside results from other security scanners.
Licensing
Running the Harness SCA step in STO pipelines requires a Harness SCA Enterprise license.
For licensing details or to enable the Enterprise license, contact Harness Sales.
Free Trial
A 45-day free trial is available. If you are an existing Harness STO customer and want to access the Harness scanners, contact the Harness sales representative to have them enabled for your account.
The following topics contain useful information for setting up scanner integrations in STO:
Harness SCA scanner is being gradually rolled out and is currently enabled for some customers. Full availability across all accounts is coming soon.
Harness SCA step settings for STO scans
To view Reachability information in Harness SCA, you must run the Harness SAST scanner. The scanner uses SAST based data flow analysis to understand how data moves through your code and determine whether an issue is reachable.
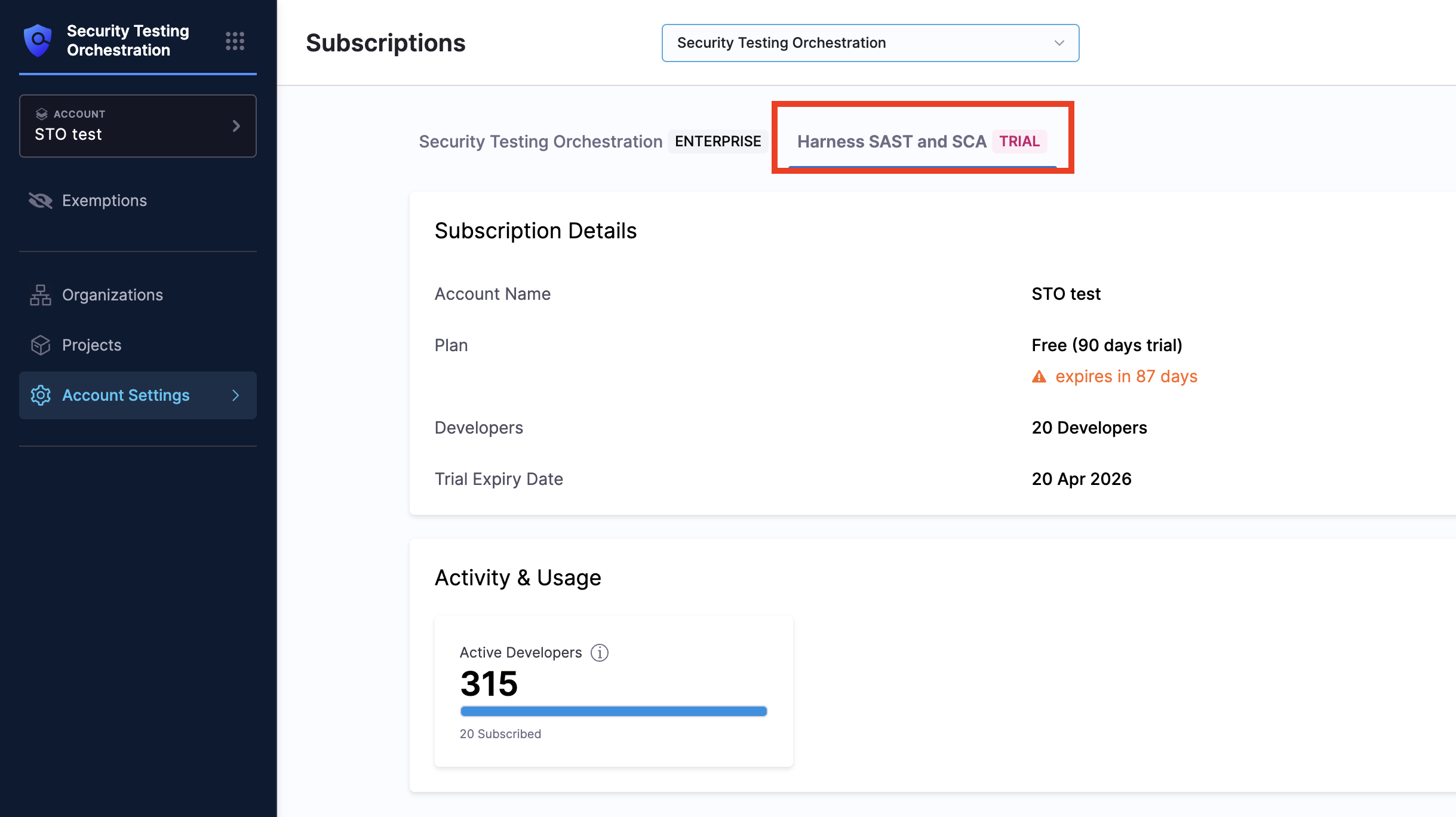
Setting up the Harness SCA scanner is the same as configuring any other built-in scanner step. The required configuration for the scanner step is handled automatically, making the setup process simple and straightforward. Here’s how to set it up:
-
In your Build or Security stage, open the step palette by clicking the Add Step option in your pipeline.
-
Navigate to the Harness Security Scanners section under the Security Tests category. Select the Harness SCA step.

-
Provide the container information from which you want to pull your container images.
-
By default, all the below fields are configured automatically by the Harness SCA scanner.
- Set the Scan Mode to Orchestration.
- Set the Scan Configuration to Default
- Set the Target Type to Container Image.
To run the Harness SCA scan step in the pipeline, no further configuration is required; If you want to add additional scan settings, you can configure the following below fields in the step.
- HAR
- Third-Party
- Local
-
Registry: Select the Harness Registry configured for the Harness Artifact Registry where your artifact is stored.
-
Image: Enter the name of your image with tag or digest, such as
imagename:tagorimagename:digest.
The registry type where the image is stored:
-
Docker v2 A registry that uses the Docker Registry v2 API such as Docker Hub, Google Container Registry, or Google Artifact Registry. STO will automatically pull and scan the container image or OCI/Docker archive.
- Image: Enter the name of your image using either a tag or a digest. For example:
my-docker-org/repo-name:tagormy-docker-org/repo-name@sha256:<digest>
- Image: Enter the name of your image using either a tag or a digest. For example:
-
AWS ECR Set your AWS ECR connector with image details. STO will automatically pull and scan the container image or OCI/Docker archive.
- Image: Image: Enter the name of your image with tag or digest. For example: such as
my-docker-repo/my-artifact:latestormy-docker-repo/my-artifact@sha256:<digest>. - Access ID: The Access ID is the AWS Access Key ID used to authenticate with Amazon ECR.
- Access Token: The Access Token is the AWS Secret Access Key associated with the Access ID.
- Region: The region where the image to scan is located, as defined by the cloud provider such as AWS.
- Image: Image: Enter the name of your image with tag or digest. For example: such as
-
Jfrog Artifactory Set your Jfrog Artifactory connector with image details. STO will automatically pull and scan the container image or OCI/Docker archive.
- Image: Specify the fully qualified image name stored in JFrog Artifactory. For example: such as
<registry>/<repository>/<image>:<tag>or<registry>/<repository>/<image>@sha256:<digest> - Access ID/Username: The username to log in to the image registry.
- Access Token: The access token used to log in to the image registry. This is usually a password or an API key.
- Image: Specify the fully qualified image name stored in JFrog Artifactory. For example: such as
You should create a Harness text secret with your encrypted token and reference the secret using the format <+secrets.getValue("container-access-id")>. For more information, go to Add and Reference Text Secrets.
-
Local Image in this Stage Scan a local image built and stored within the context of the current stage (via
/var/run/docker.sockregistered as a stage level volume mount). For this, you will need to configure Docker-in-Docker as a background step. STO will identify and scan the container image matching the step configuration inside the Docker-in-Docker background within that stage. -
Local OCI/Docker archive in this Stage Scan an OCI or Docker archive created and stored within the current stage. STO will scan the archive based on the path configured in the workspace field during the step. Ensure that the path to which the archive is saved is a shared volume mount.
-
Image Enter the name of your image with tag or digest, such as
imagename:tag.
Target
Type
- Container Image Scan the layers, libraries, and packages in a container image.
Target and Variant Detection
When Auto is enabled for container images, the step detects the target and variant using the Container Image Name and Tag defined in the step or runtime input.
Note the following:
- Auto is not available when the Scan Mode is Ingestion.
- By default, Auto is selected when you add the step. You can change this setting if needed.
Name
The identifier for the target, such as codebaseAlpha or jsmith/myalphaservice. Descriptive target names make it much easier to navigate your scan data in the STO UI.
It is good practice to specify a baseline for every target.
Variant
The identifier for the specific variant to scan. This is usually the branch name, image tag, or product version. Harness maintains a historical trend for each variant.
Workspace
This field is visible only when you select Repository as the Target Type.
Use this field to specify an individual folder or file to scan. For example, if you want to scan a specific file like /tmp/example/test.py, set the workspace path to:
/harness/tmp/example/test.py
-
The Harness SCA scanner is not supported in SMP.
-
With a Harness SCA Enterprise license, you also get access to the Qwiet AI by Harness platform. AppSec users can log in to the platform.
-
The Qwiet AI dashboard does not support exemptions, so any issues you mark as exempt in Harness STO will not appear as exempted in Qwiet AI. Exemptions must be managed in Harness STO only.
Scan Tool
App Name
Provide a unique name to identify this scanning application. All scan results for this application are grouped and tracked under this name in the Qwiet AI by Harness dashboard.
Log Level
The minimum severity of the messages you want to include in your scan logs. You can specify one of the following:
- DEBUG
- INFO
- WARNING
- ERROR
Additional CLI flags
Fail on Severity
Every STO scan step has a Fail on Severity setting. If the scan finds any vulnerability with the specified severity level or higher, the pipeline fails automatically. You can specify one of the following:
CRITICALHIGHMEDIUMLOWINFONONE— Do not fail on severity
The YAML definition looks like this: fail_on_severity : critical # | high | medium | low | info | none
Settings
You can use this field to specify environment variables for your scanner.
Additional Configuration
The fields under Additional Configuration vary based on the type of infrastructure. Depending on the infrastructure type selected, some fields may or may not appear in your settings. Below are the details for each field
- Override Security Test Image
- Privileged
- Image Pull Policy
- Run as User
- Set Container Resources
- Timeout
Advanced settings
In the Advanced settings, you can use the following options:
View Harness SCA Scan results in the Vulnerabilities tab
After you complete the pipeline run with the Harness SCA scanner, in the vulnerabilities tab, apply the Issue Type filter as SCA to view the vulnerabilities identified by the Harness SCA scanner.
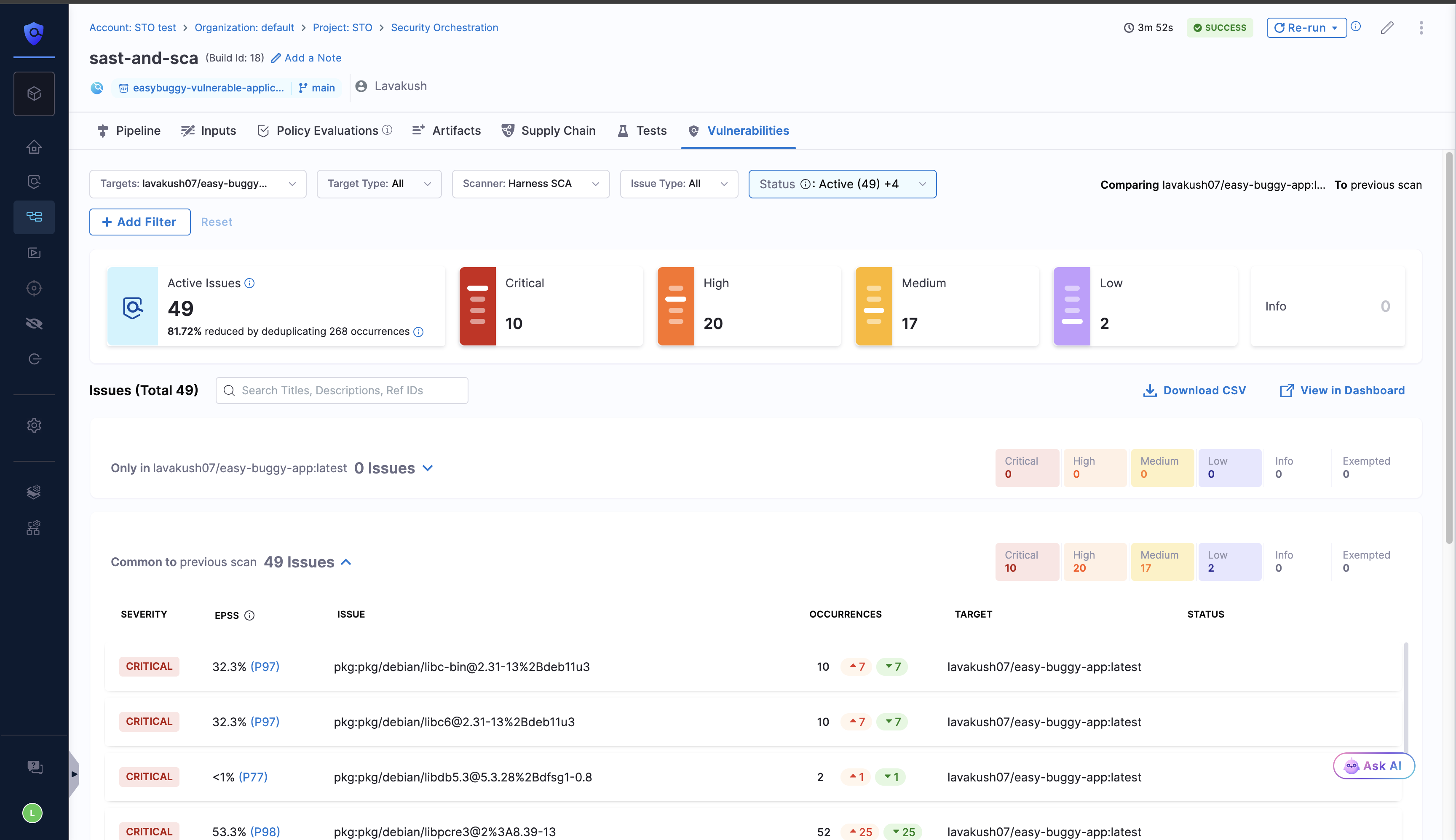
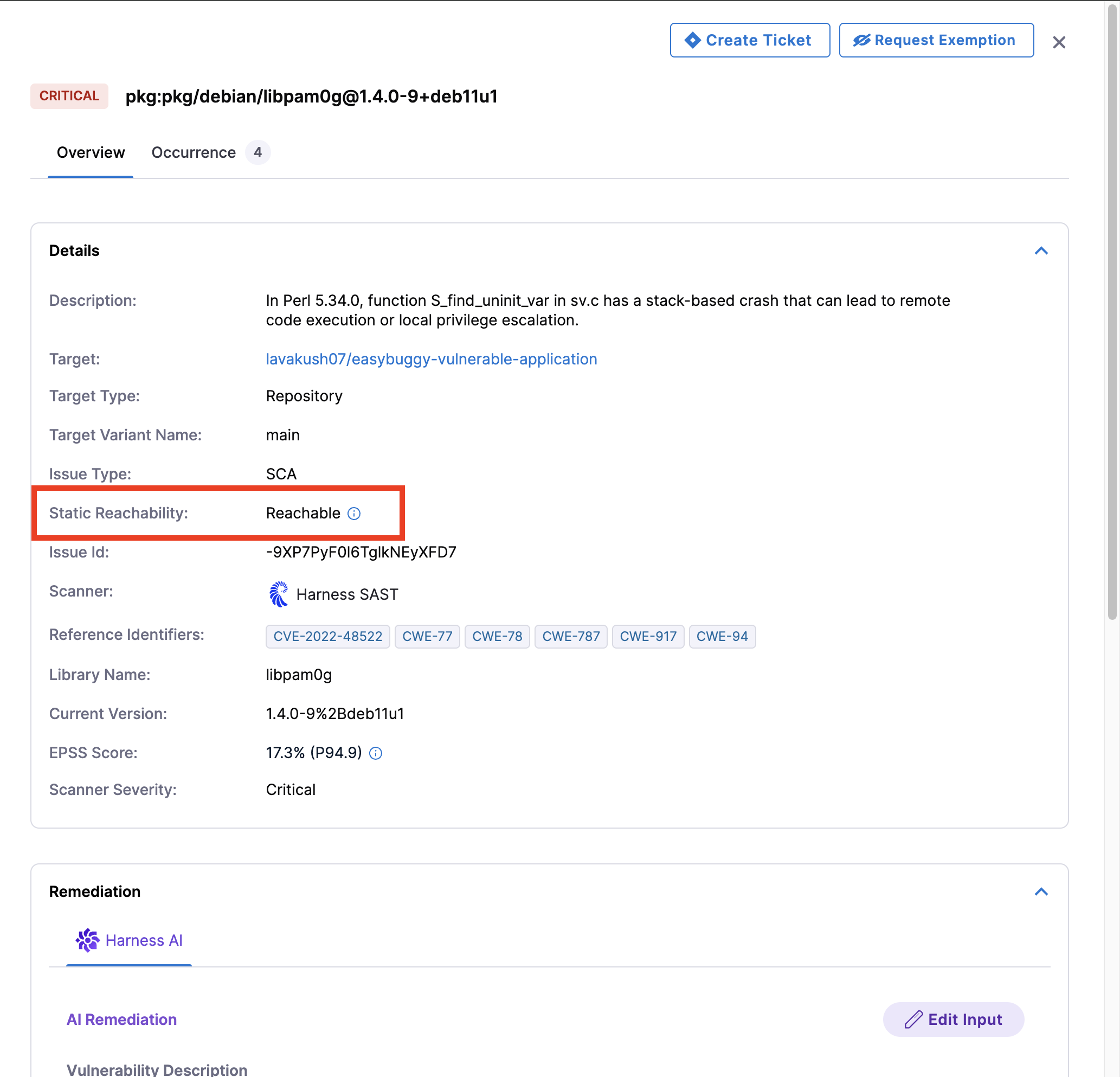
Static Reachability
A vulnerability is considered as Reachable when an attacker can reach the affected code (CVE) through a controlled path from application input. A vulnerability is marked as Reachable if at least one of its occurrences is reachable. Exempted occurrences are not considered. You can view the Reachability for each of the occurrences of a security issue in the Vulnerabilities and Issues page.
After a successful pipeline run, the Vulnerabilities tab shows whether a vulnerability is marked as Reachable. On the Vulnerabilities page, use the Reachability filter to view findings by reachability. This helps reduce noise and focus on vulnerabilities that pose real risk. Learn more.
IDE Integration
Harness provides a code extension that helps you shift security even further left by allowing you to identify and fix vulnerabilities as you write code. It integrates directly into the developer workflow through IDE plugins for VS Code and JetBrains, with support for AI-native IDEs such as Cursor and Windsurf coming soon.
Harness also provides a CLI to run SAST and SCA scans locally, to help you identify code vulnerabilities and dependency risks before pushing code to your repository. Learn more on how to install, authenticate, and use the CLI commands in the Harness CLI.
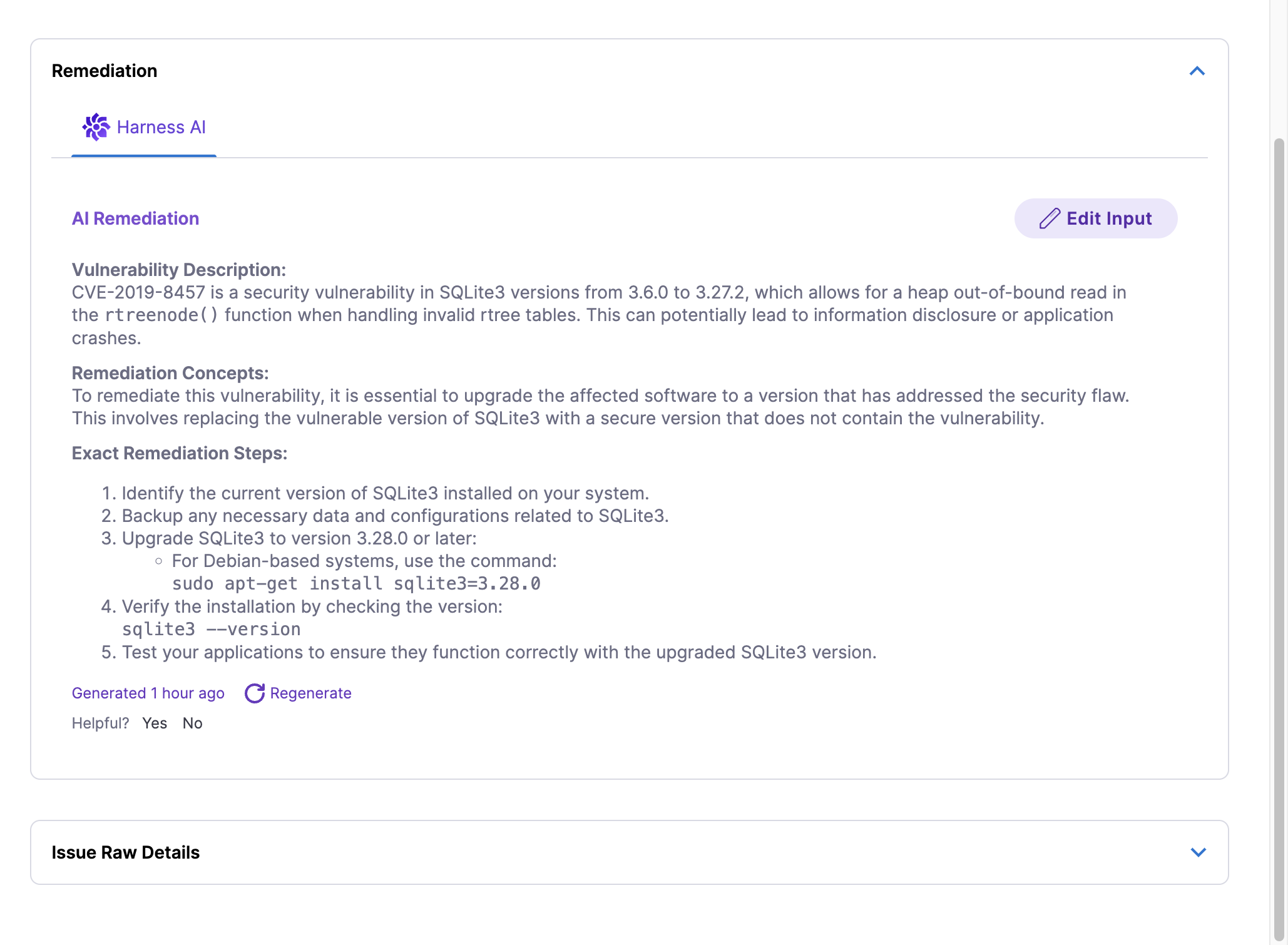
AI remediation for Harness SCA Security Issues
Harness AI analyzes security issues and provides AI remediation within the security details for each specific issue. This includes an analysis of the issue, remediation concepts, and step-by-step instructions to fix them. Additionally, for SCA issues, Harness AI recommends safer package versions for upgrade, with remediation details available for each occurrence of an issue.
Enforce OPA Policy to block the Static Reachable Vulnerabilities
Enforce OPA Policy to automatically warn or block pipelines based on static reachability, exploitability, and license metadata, to help you prevent risky deployments and maintain security and compliance.
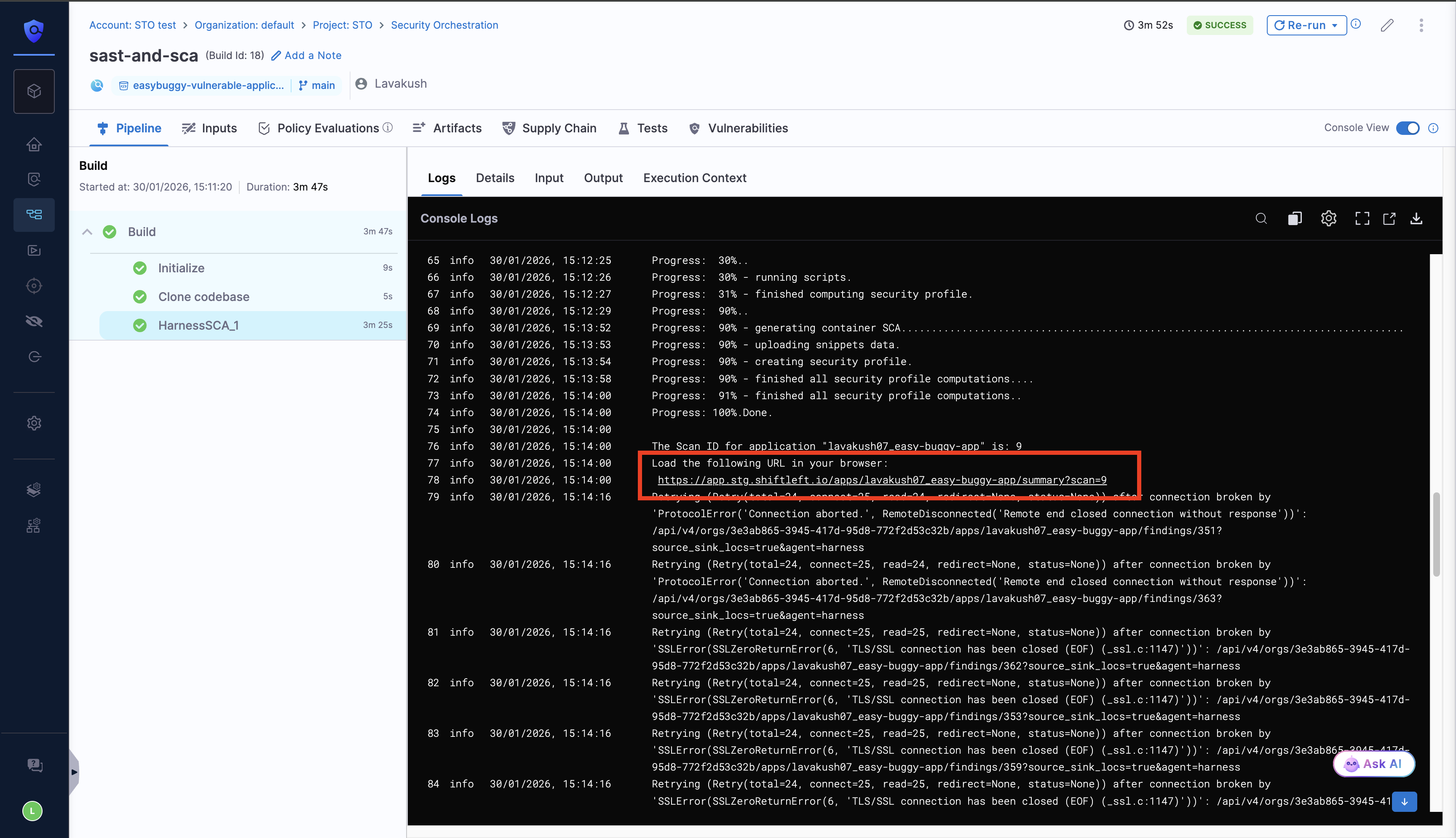
View Harness SCA Scan results in the Qwiet AI Dashboard
After you complete the pipeline run with the Harness SCA scanner, in the scan logs, you can click the provided shiftleftlink, which redirects you to the Qwiet AI dashboard, where you can explore detailed scan results and analyze identified issues.
Alternatively, you can manually log in to the Qwiet AI by Harness dashboard and search for the application name that corresponds to the target name used in the scan.
You can view the generated SBOM for container image dependencies, along with the scan summary and compliance results, in the Qwiet AI by Harness dashboard. These details are currently available only in Qwiet AI by Harness dashboard and are not currently supported in Harness STO.
License Usage
Usage is calculated based on Active Developers. An Active Developer is an individual who, within the last 90 days, has created or modified code, configurations, content, or artifacts that are scanned by STO. An individual is counted only once, even if they contribute to multiple scanned repositories.
You can view your current usage and subscription details on the STO subscription page under the Harness SAST and SCA sub-tab