Approve Base Image
In many organizations, security teams vet and approve specific base images for developers to use. Even if these images contain known vulnerabilities, they are considered acceptable. STO's Base Image Approval feature helps you implement this process and enforce policies on it. This document covers:
- What is Base Image Approval?
- How to Approve a Base Image?
- Policies for Vulnerabilities from Application and Base Images
-
This feature is behind the feature flags
STO_BASE_IMAGEandSTO_BASE_IMAGE_DETECTION. Contact Harness Support to enable this flag. -
Currently, this feature is supported only for scans using Orchestration scan mode. Support for Ingestion and Extraction scan modes will be available soon.
What is Base Image Approval?
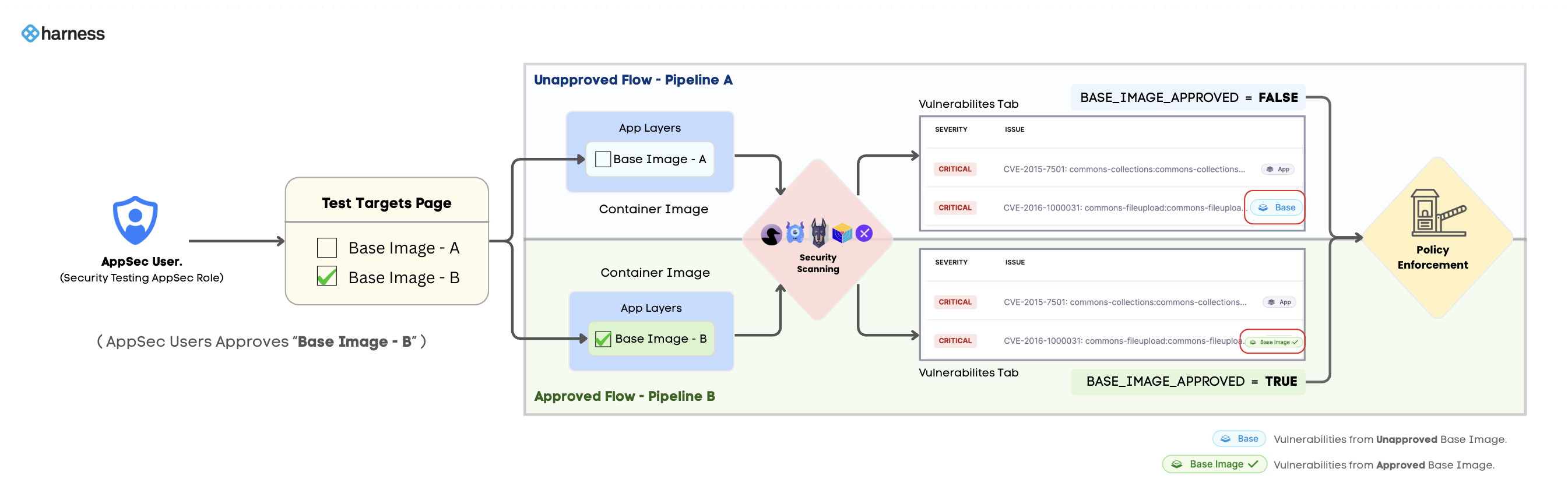
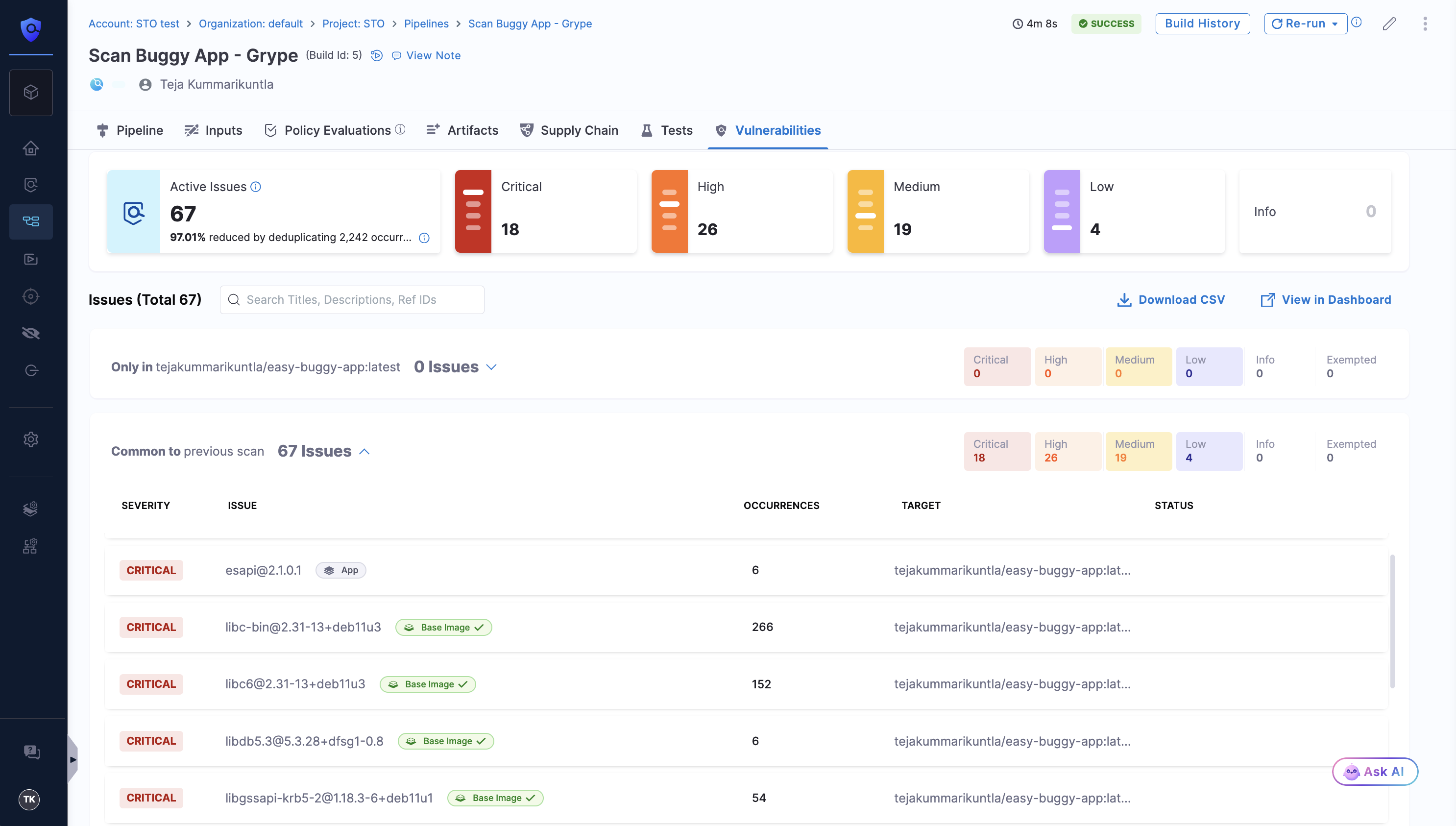
Base Image Approval is a manual process where you explicitly approve one or more tags of a base image target in STO. This action signals that the selected base image tags are trusted for use in your pipelines. When you scan an application image built on an approved base image tag, you will find the scan results with the following indicators:
- UI Indicator: Vulnerabilities originating from the approved base image are marked with a green
Base Imagelabel in the Vulnerabilities tab. Vulnerabilities from unapproved base images are marked in blue. - Step Output Variable: The
BASE_IMAGE_APPROVEDoutput variable in the scanner step is set totrue. This variable allows you to create policies to ignore vulnerabilities from approved base images.
How to Approve a Base Image
Before approving a base image, make sure you’ve reviewed What is Base Image Approval? and understood the process. To approve a base image, you must have the Approve / Reject permission for Test Targets in the project where you want to approve the base image. Or you must have the Security Testing AppSec role assigned. Refer to the RBAC documentation for more information.
Approving a base image in a project is applied across the entire account. Once approved, the base image is considered trusted throughout the account, including all organizations and projects even those you may not have direct access to. Be aware that the approval will be applied at the account level.
A base image can only be approved in the project where it was last scanned. If you try to approve it elsewhere, the approval will not take effect.
Identify the Correct Project to Approve
To identify the correct project:
- Go to your pipeline execution window.
- Switch to Vulnerabilities tab.
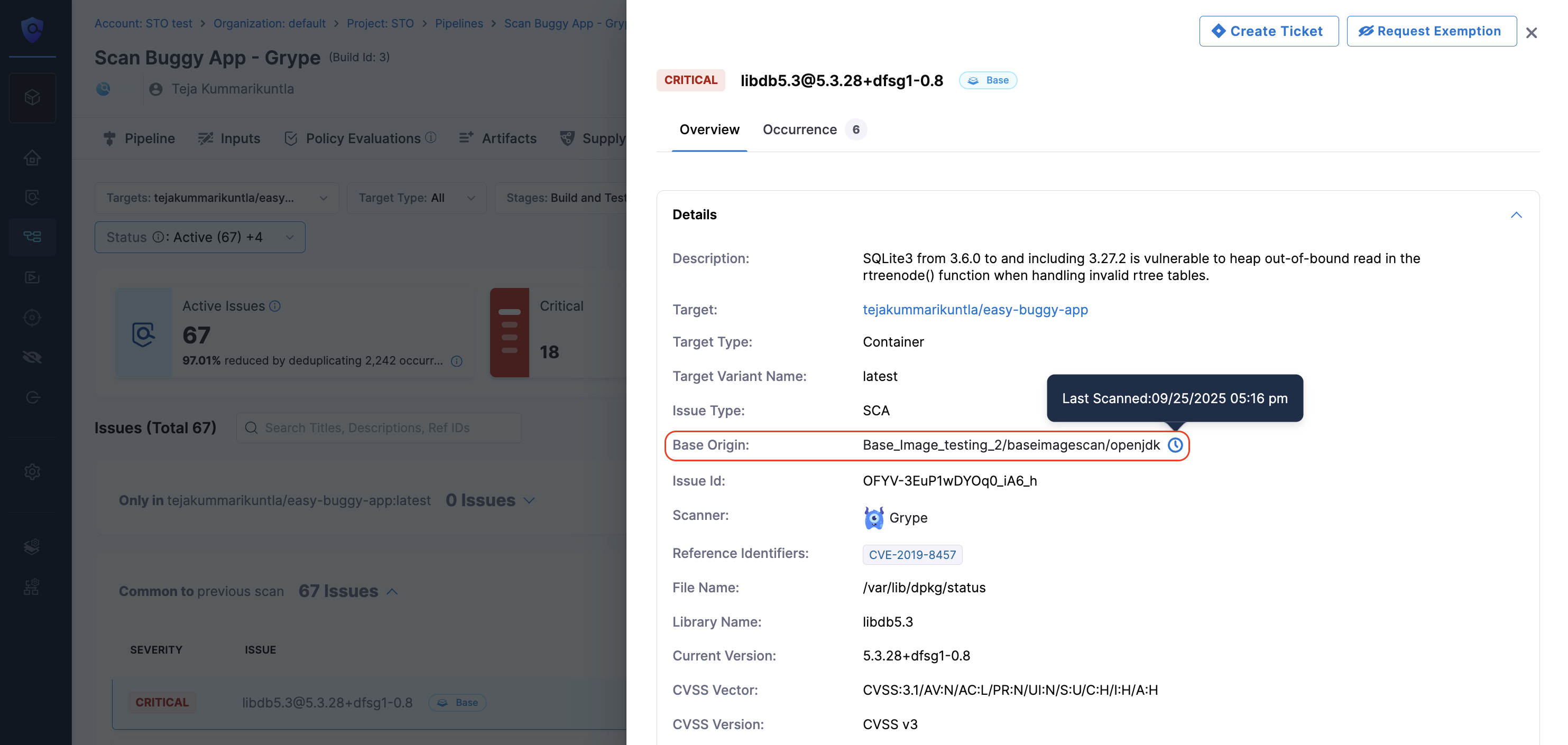
- Open the issue details of a vulnerability labeled with
Base. - Check the Base Origin field. This field displays the project name where the base image was last scanned.
For example, the Base Origin might appear as: Base_Image_testing_2/baseimagescan/openjdk. This aligns with the format OrgName/ProjectName/TargetName. You can approve the base image in the baseimagescan project.
To approve a base image, follow the steps:
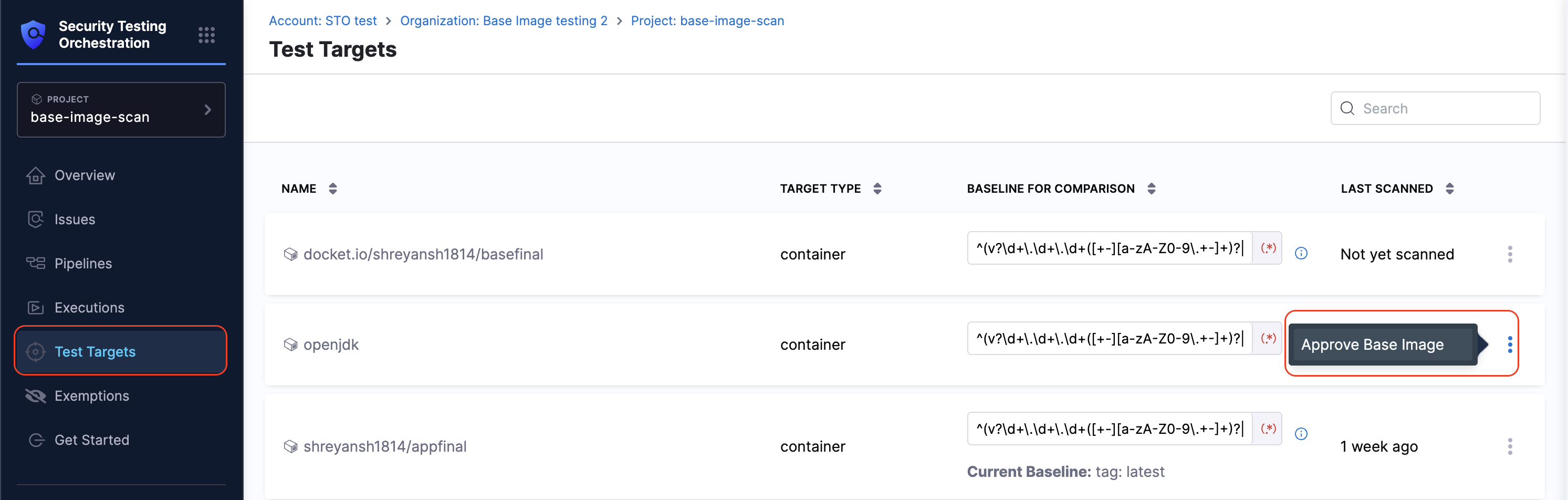
- Go to Test Targets page from the left navigation.
- Find your base image (target) in the list. (for example,
openjdk). - Click the ellipsis menu on the right and select Approve Base Image.
- In the dialog, select one or more tags of the base image to approve (for example,
bookworm-slim).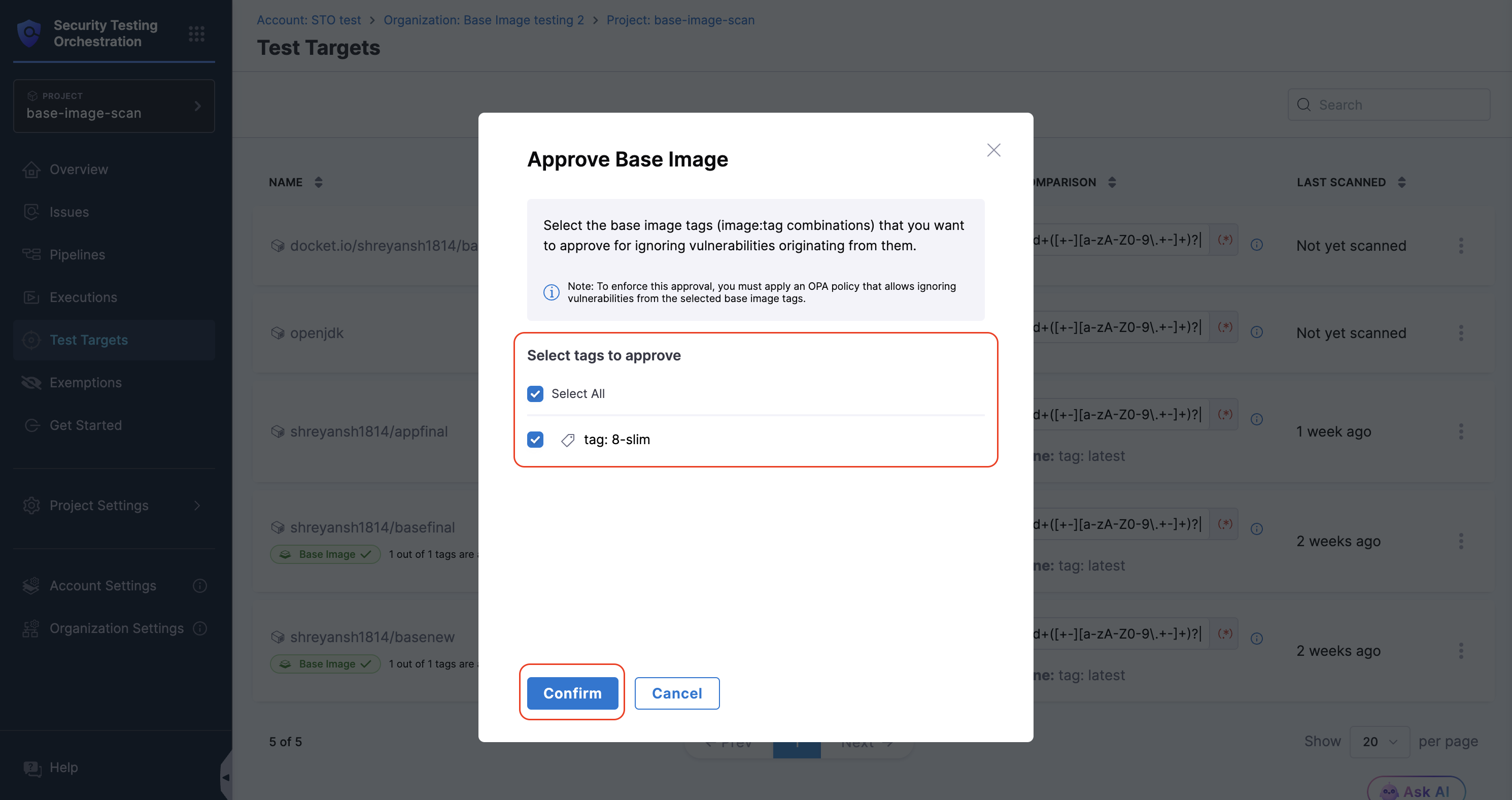
- Click Submit.
To unapprove a base image, you can follow the same steps and deselect the tags you want to unapprove and click Confirm. The approval or unapproval takes effect from the next pipeline execution.
How to view Vulnerabilities from Approved Base Image
To view the vulnerabilities associated with the approved base image, follow these steps:
Before proceeding, make sure that:
- You have configured base image detection.
- You approved the base image by following the steps in How to Approve a Base Image. Once approved, the approval will take place from the next pipeline execution after the approval.
- Go to Security Testing Orchestration module.
- Go to Execution page from the left navigation.
- Find the pipeline execution with your container image scanning and open it.
- Go to Vulnerabilities tab.
- You will see the vulnerabilities from approved base image marked with a green
Base Imagelabel.
Policies for Vulnerabilities from Application and Base Images
You can enforce policies on vulnerabilities from both application layers and base images by using the step output variables of your scanner step. Refer to Step Output Variables for App and Base Image Vulnerabilities for details.
Depending on your use case, you can apply the following sample policies:
- Warn or Block Vulnerabilities from Application Layer: Use this policy to enforce actions on vulnerabilities originating from the application layers of the container image.
- Warn or Block Vulnerabilities from Base Image: Use this policy to check if the base image is approved. If it is not approved, you can configure the policy to warn or block vulnerabilities from the base image.