Aqua Trivy scanner reference for STO
You can scan your container images using Aqua Trivy, a comprehensive and versatile open-source scanner.
STO supports container scans only with Aqua Trivy.
Important notes for running Aqua Trivy scans in STO
Docker-in-Docker requirements
The following use cases require a Docker-in-Docker background step in your pipeline:
- Container image scans on Kubernetes and Docker build infrastructures
- Required for Orchestration and Dataload scan modes
- Security steps (not step palettes) on Kubernetes and Docker build infrastructures
- Required for all target types and Orchestration/DataLoad modes
The following use cases do not require Docker-in-Docker:
- Harness Cloud AMD64 build infrastructures
- SAST/DAST/configuration scans that use scanner templates (not Security steps)
- Ingestion scans where the data file has already been generated
Set up a Docker-in-Docker background step
-
Go to the stage where you want to run the scan.
-
In Overview, add the shared path
/var/run. -
In Execution, do the following:
-
Click Add Step and then choose Background.
-
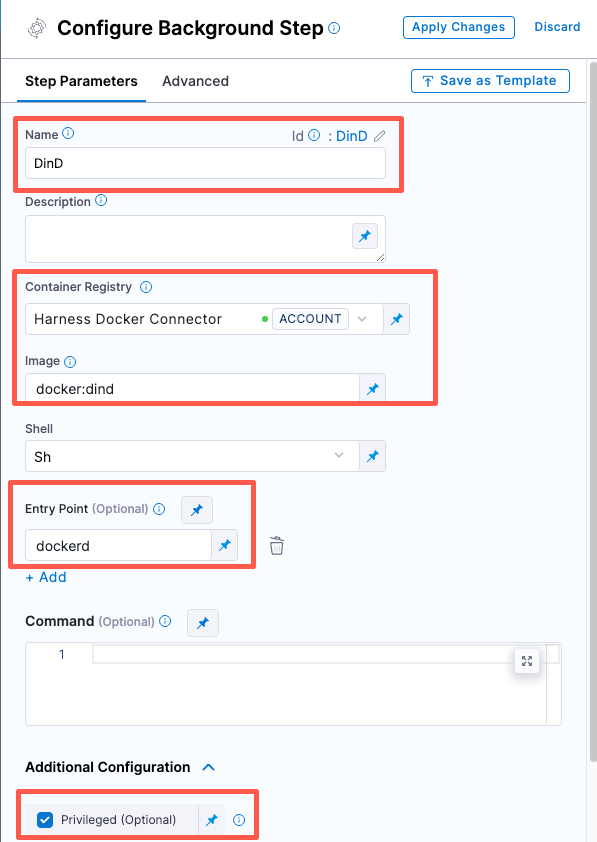
Configure the Background step as follows:
-
Dependency Name =
dind -
Container Registry = The Docker connector to download the DinD image. If you don't have one defined, go to Docker connector settings reference.
-
Image =
docker:dind -
Under Entry Point, add the following:
dockerdIn most cases, using
dockerdis a faster and more secure way to set up the background step. For more information, go to the TLS section in the Docker quick reference.
If the DinD service doesn't start with
dockerd, clear the Entry Point field and then run the pipeline again. This starts the service with the default entry point.- Under Optional Configuration, select the Privileged checkbox.
-
-
- Visual setup
- YAML setup
Add a Background step to your pipeline and set it up as follows:
- step:
type: Background
name: background-dind-service
identifier: Background_1
spec:
connectorRef: CONTAINER_IMAGE_REGISTRY_CONNECTOR
image: docker:dind
shell: Sh
entrypoint:
- dockerd
privileged: true
Root access requirements
You need to run the scan step with root access if either of the following apply:
-
You need to run a Docker-in-Docker background service.
-
You need to add trusted certificates to your scan images at runtime.
You can set up your STO scan images and pipelines to run scans as non-root and establish trust for your own proxies using custom certificates. For more information, go to Configure STO to Download Images from a Private Registry.
For more information
The following topics contain useful information for setting up scanner integrations in STO:
Aqua Trivy step settings for STO scans
The recommended workflow is add an AquaTrivy step to a Security Tests or CI Build stage and then configure it as described below.
Scan
Scan Mode
- Orchestration Configure the step to run a scan and then ingest, normalize, and deduplicate the results.
- Ingestion Configure the step to read scan results from a data file and then ingest, normalize, and deduplicate the data.
Scan Configuration
The predefined configuration to use for the scan. All scan steps have at least one configuration.
Target
Type
- Container Image Scan the layers, libraries, and packages in a container image.
Detect target and variant
When auto-detect is enabled for container images, the step detects the target and variant using the Container Image Name and Tag defined in the step or runtime input.
Note the following:
- Auto-detection is not available when the Scan Mode is Ingestion.
- Auto-detect is the default selection for new pipelines. Manual is the default for old pipelines, but you might find that neither radio button is selected in the UI.
Name
The identifier for the target, such as codebaseAlpha or jsmith/myalphaservice. Descriptive target names make it much easier to navigate your scan data in the STO UI.
It is good practice to specify a baseline for every target.
Variant
The identifier for the specific variant to scan. This is usually the branch name, image tag, or product version. Harness maintains a historical trend for each variant.
Container image
Type
The registry type where the image is stored:
-
Docker v2 A registry that uses the Docker Registry v2 API such as Docker Hub, Google Container Registry, or Google Artifact Registry.
-
Local Image
Domain
The URL of the registry that contains the image to scan. Examples include:
docker.ioapp.harness.io/registryus-east1-docker.pkg.devus.gcr.io
Name
The image name. For non-local images, you also need to specify the image repository. Example: jsmith/myalphaservice
Tag
The image tag. Examples: latest, 1.2.3
Access ID
The username to log in to the image registry.
Access Token
The access token used to log in to the image registry. In most cases this is a password or an API key.
You should create a Harness text secret with your encrypted token and reference the secret using the format <+secrets.getValue("project.container-access-id")>. For more information, go to Add and Reference Text Secrets.
Region
The region where the image to scan is located, as defined by the cloud provider such as AWS.
Ingestion
Ingestion File
The path to your scan results when running an Ingestion scan, for example /shared/scan_results/myscan.latest.sarif.
-
The data file must be in a supported format for the scanner.
-
The data file must be accessible to the scan step. It's good practice to save your results files to a shared path in your stage. In the visual editor, go to the stage where you're running the scan. Then go to Overview > Shared Paths. You can also add the path to the YAML stage definition like this:
- stage:
spec:
sharedPaths:
- /shared/scan_results
Log Level
The minimum severity of the messages you want to include in your scan logs. You can specify one of the following:
- DEBUG
- INFO
- WARNING
- ERROR
Additional CLI flags
Use this field to run the trivy image scanner with flags such as:
--ignore-unfixed --scanners vuln
With these flags, the scanner reports only on vulnerabilities with known fixes.
Passing additional CLI flags is an advanced feature. Harness recommends the following best practices:
-
Test your flags and arguments thoroughly before you use them in your Harness pipelines. Some flags might not work in the context of STO.
-
Don't add flags that are already used in the default configuration of the scan step.
To check the default configuration, go to a pipeline execution where the scan step ran with no additional flags. Check the log output for the scan step. You should see a line like this:
Command [ scancmd -f json -o /tmp/output.json ]In this case, don't add
-for-oto Additional CLI flags.
Fail on Severity
Every Security step has a Fail on Severity setting. If the scan finds any vulnerability with the specified severity level or higher, the pipeline fails automatically. You can specify one of the following:
CRITICALHIGHMEDIUMLOWINFONONE— Do not fail on severity
The YAML definition looks like this: fail_on_severity : critical # | high | medium | low | info | none
Settings
You can use this field to specify environment variables for your scanner.
Additional Configuration
In the Additional Configuration settings, you can use the following options:
Advanced settings
In the Advanced settings, you can use the following options:
YAML pipeline example
Here's an example of the pipeline you created in this tutorial. If you copy this example, replace the placeholder values with appropriate values for your project and organization.
pipeline:
projectIdentifier: YOUR_PROJECT_ID
orgIdentifier: YOUR_HARNESS_ORG_ID
tags: {}
stages:
- stage:
name: build
identifier: build
type: CI
spec:
cloneCodebase: false
sharedPaths:
- /var/run
- /shared/scan_results
execution:
steps:
- step:
type: AquaTrivy
name: AquaTrivy_1
identifier: AquaTrivy_1
spec:
mode: orchestration
config: default
target:
type: container
name: redhat/ubi8-minimal
variant: latest
advanced:
log:
level: info
args:
cli: "--scanners vuln"
privileged: true
image:
type: docker_v2
name: redhat/ubi8-minimal
domain: docker.io
tag: latest
sbom:
format: spdx-json
platform:
os: Linux
arch: Amd64
runtime:
type: Cloud
spec: {}
caching:
enabled: false
paths: []
slsa_provenance:
enabled: false
description: ""
identifier: trivyorchestration
name: trivy-orchestration