Request Issue Exemption
Issue exemptions help unblock pipelines by allowing security teams to temporarily bypass specific security issues that would otherwise fail the build. To understand how exemptions fit into your security workflow, refer to the issue exemptions workflow.
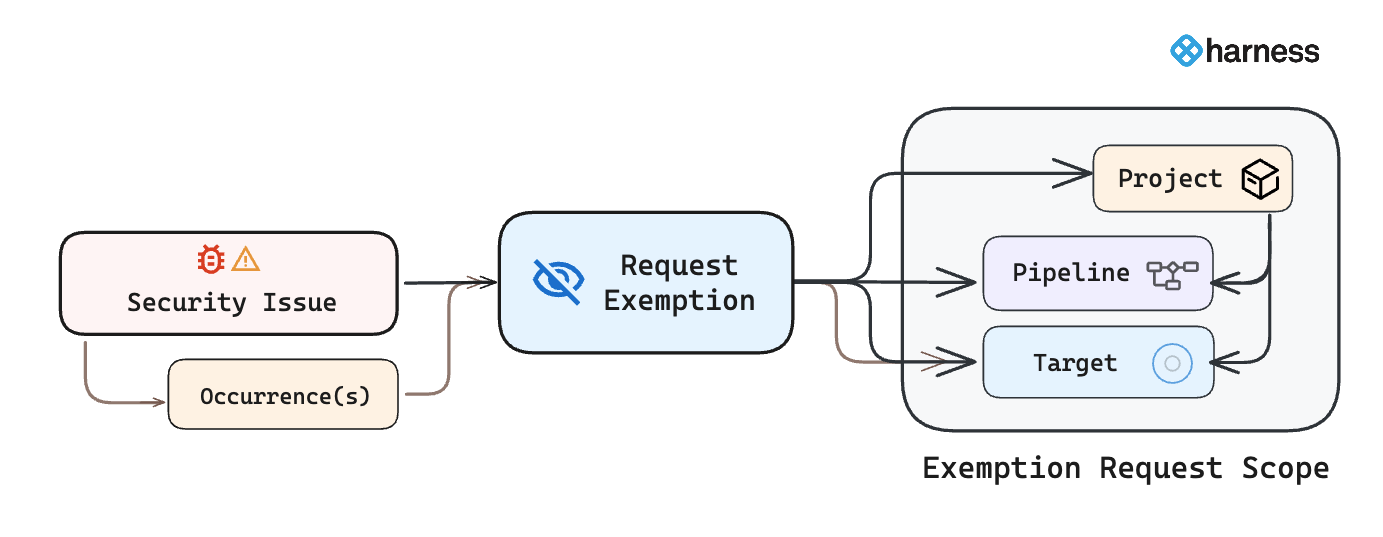
You can create exemption requests either for the entire issue or for specific occurrences within an issue:
- Create Exemption Request for an Issue: When creating an exemption request for an entire issue, you can set the exemption scope at the Project, Pipeline, or Target level. Refer to this section for detailed instructions.
- Create Exemption Request for Occurrences within Issue: When creating exemption request for selected occurrences of an issue, the exemption scope is limited to the Target level. Refer to this section for step-by-step guidance.
Reviewers have the flexibility to approve exemption requests either at the requested scope or extend the scope to the Organization or Account level during the review process. For more details, refer to Manage Issue Exemptions. To view submitted requests, refer to View Issue Exemptions.
To create an exemption request, you must have the necessary permissions (Exemptions: View, Create/Edit) at the Project level, or you can have the Security Testing Developer or Security Testing AppSec roles assigned. Refer Permissions required for issue exemptions for more details.
Create Exemption Request for an Issue
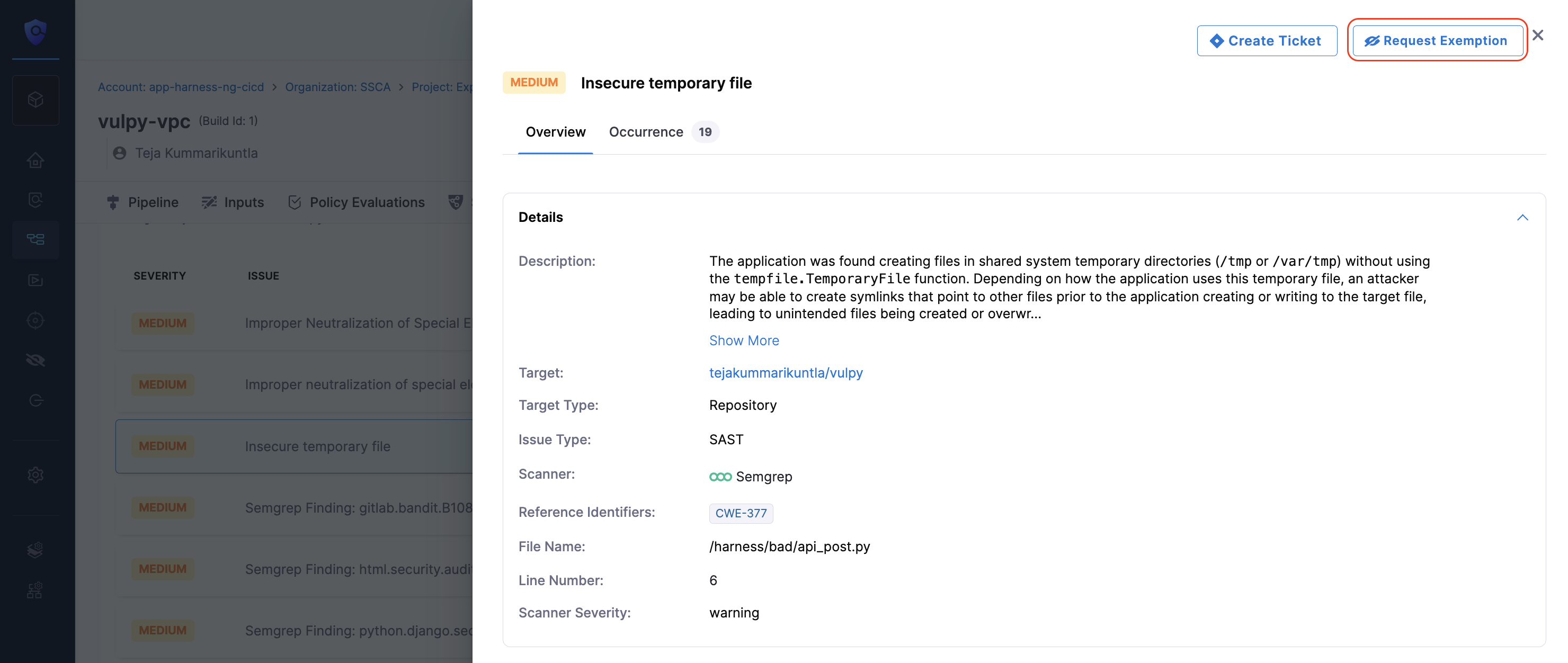
To request an exemption for an entire issue, you can set the exemption scope at the Project, Pipeline, or Target level. To begin, navigate to the Vulnerabilities tab.
-
In the Vulnerabilities tab, locate and select the specific issue for which you want to request an exemption. This action opens the Issue Details pane on the right.
-
In the Issue Details pane, click Request Exemption.
Submit Exemption Request
Fill out the Request Exemption for Issue form with the following fields:
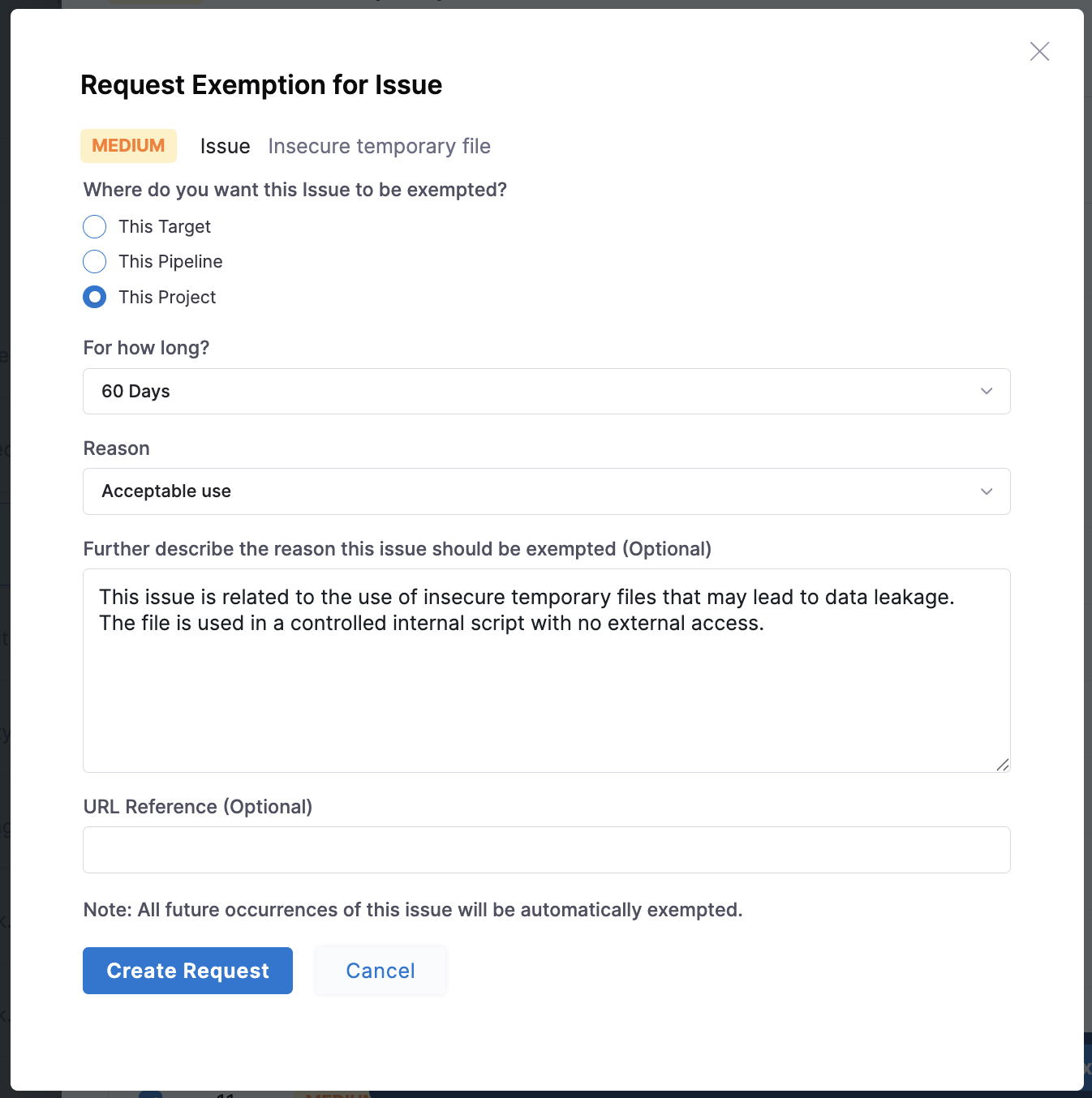
Where do you want this issue to be exempted?
Specify where the exemption should apply:
- This Target: Exempts the issue only for the selected target. The issue remains reported in other targets or pipelines.
- This Pipeline: Exempts the issue only in the current pipeline. The issue is still reported in other pipelines or projects.
- This Project: Exempts the issue across all pipelines and targets within this project. Choose carefully, as the exemption applies broadly within the project.
- While requests can only be created with the scopes mentioned above, reviewers can approve and apply them at the requested scope or at a higher scope - Organization or Account.
- As you create exemption request at the issue level, all the future occurrences part of this issues will be automatically exempted. For exemptions at occurrences level, refer to Create Exemption Request for Occurrences within Issue
- Behind Feature Flag: If your pipeline includes Pipeline stages with child pipelines, an exemption request with the Pipeline scope will apply only to the child pipeline, not the parent pipeline. The feature is currently behind the feature flag
STO_AGGREGATE_CHAIN_EXECUTIONS. Contact Harness Support to enable it.
For how long?
Select the shortest practical time window for the exemption to limit the risk exposure.
Reason
Select one of the following reasons and provide relevant details:
- Compensating controls: Your organization has controls (e.g., firewall, IPS) in place that reduce the risk posed by this issue.
- Acceptable use: The flagged practice is acceptable based on internal security policies.
- Acceptable risk: The risk is low, and remediation would require significant resources or impact functionality.
- False positives: The scanner flagged a non-issue. Confirmed by a security assessor or internal review.
- Fix unavailable: No known fix or remediation steps currently exist for the issue.
- Other: Provide a detailed technical explanation for why the issue should be exempted.
Further Description
Add any technical context, mitigations, or supporting information that will help the reviewer understand why the exemption is justified.
URL Reference
Add a link to supporting documentation, source code, or any relevant resource that provides additional context.
After completing the form, click Create Request to submit the exemption. Once the exemption request is submitted:
Once submitted, the request enters the Pending state. You can set up notifications to automatically alert reviewers of new requests.
Create Exemption Request for Occurrences within Issue
To request an exemption for selected occurrences of an issue, the exemption scope must be set to the Target level. To begin, navigate to the Vulnerabilities tab.
- In the Vulnerabilities tab, locate and select the specific issue for which you want to request an exemption. This opens the Issue Details pane on the right.
- In the Issue Details pane, click the Occurrences tab.
- Select the occurrences for which you want to request the exemption.
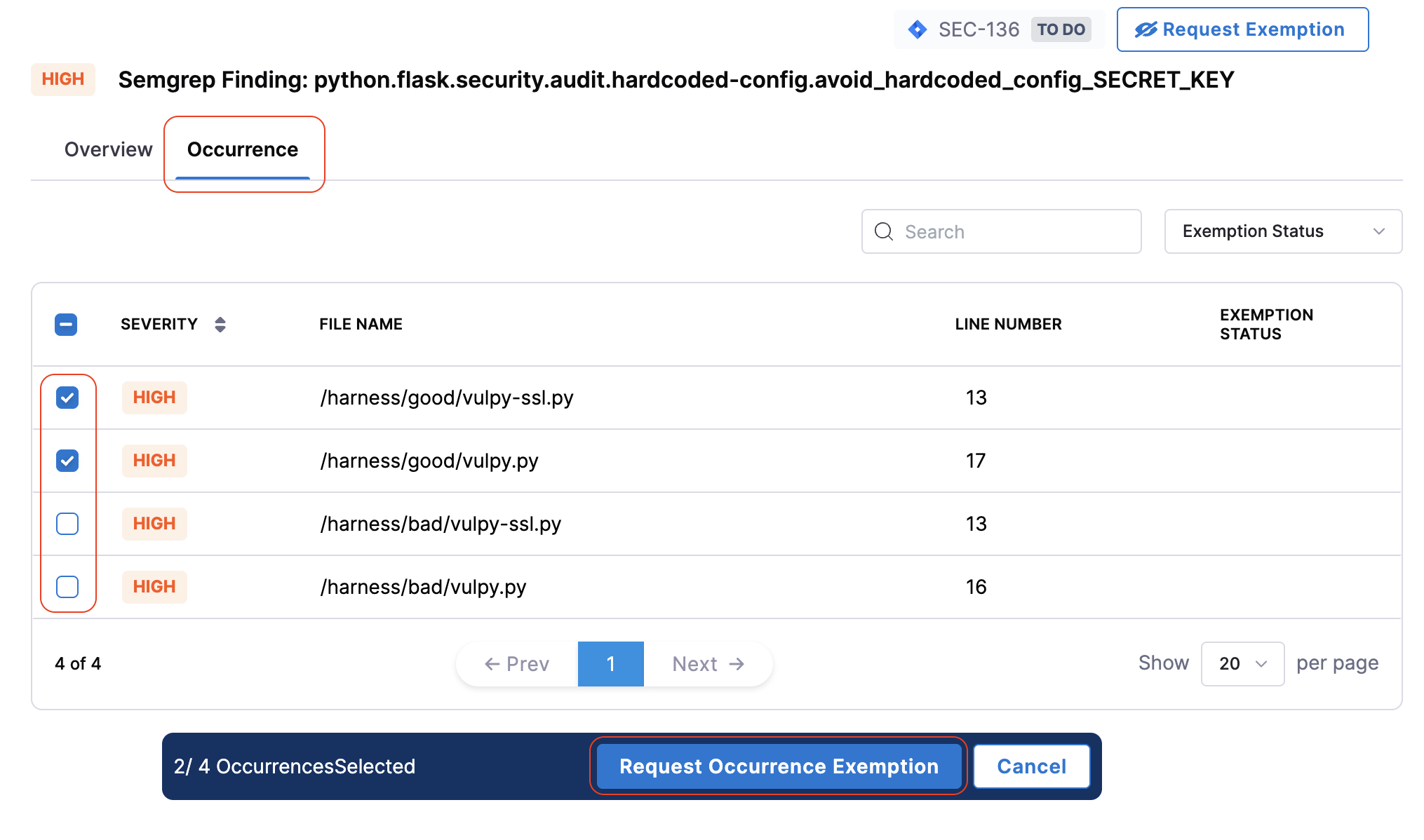
- Review your selections and click the Request Occurrence Exemption button. This opens the Request Exemption dialog box.
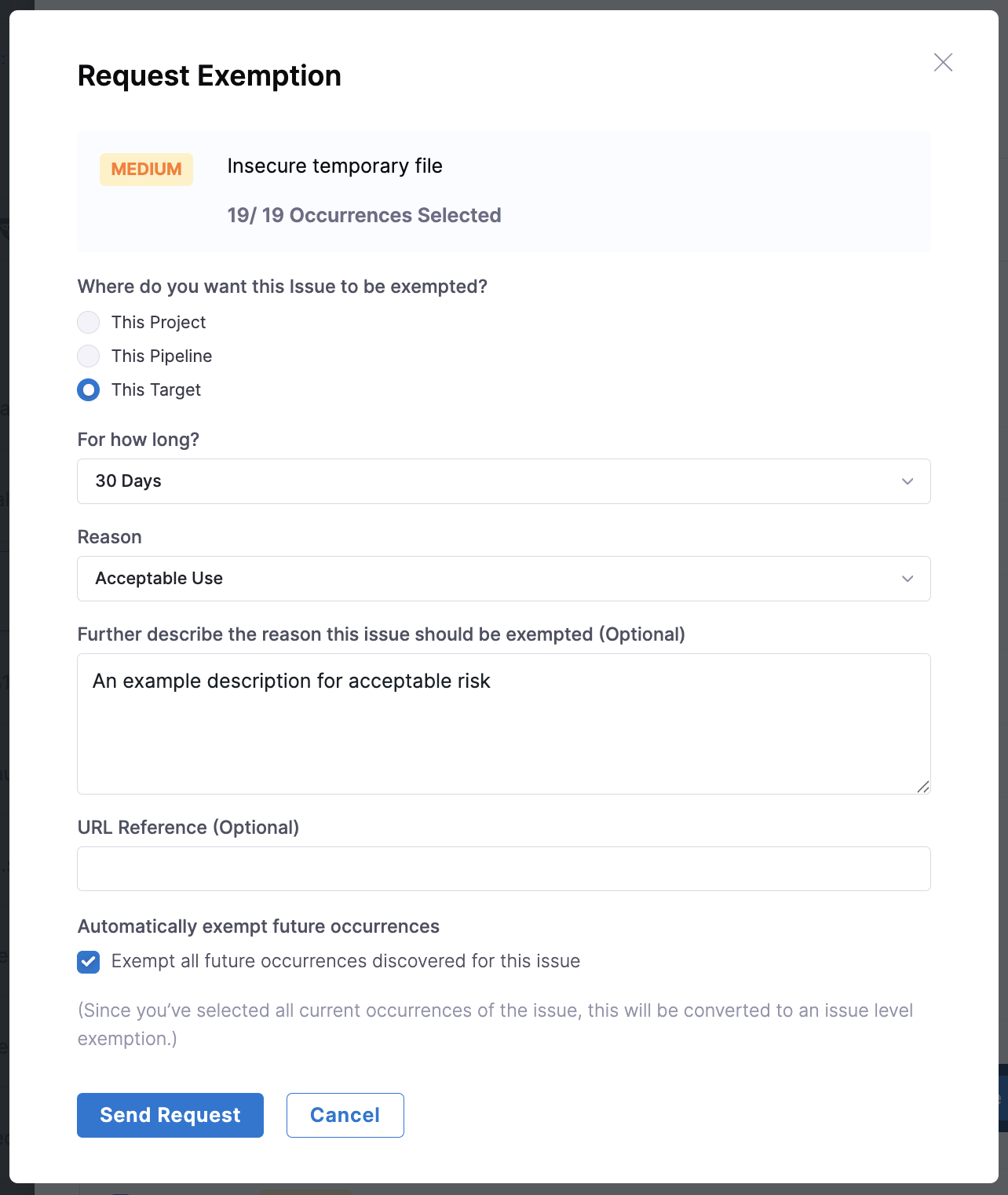
If you select all occurrences of the issue:
- The option Exempt all future occurrences discovered for this issue at the bottom becomes available. Checking this option converts the request from an occurrence-level exemption to an issue-level exemption. This ensures all future occurrences of the issue will automatically be exempted.
- If any occurrences in the list are already exempted, this option will be disabled to prevent conflicts. To enable it, cancel the existing exemption requests for those occurrences. Once done, select all occurrences again and recreate the exemption request, the option should now be available to check or uncheck.
Follow the steps in the Submit Exemption Request section to complete and submit your request.
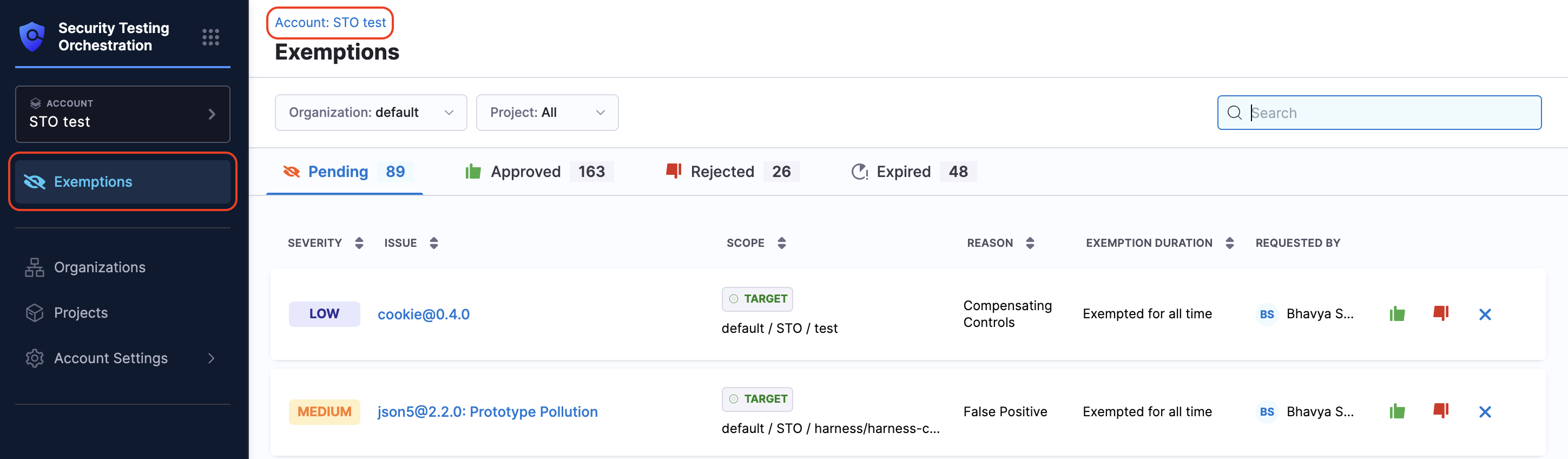
View Issue Exemptions
You can view all exemption requests from the Exemptions section in the left navigation. This section is accessible from your Project, Organization, and Account views. Each scope displays exemption requests relevant to that level:
- The Project-level Exemptions section shows requests submitted for that specific project.
- The Organization-level Exemptions section shows requests across all projects within the organization.
- The Account-level Exemptions section lists requests across projects from multiple organizations under the account.
Exemption requests list you see at the Organization and Account views are still subject to your project-level view permissions. Refer to Permissions for exemption requests to learn more.
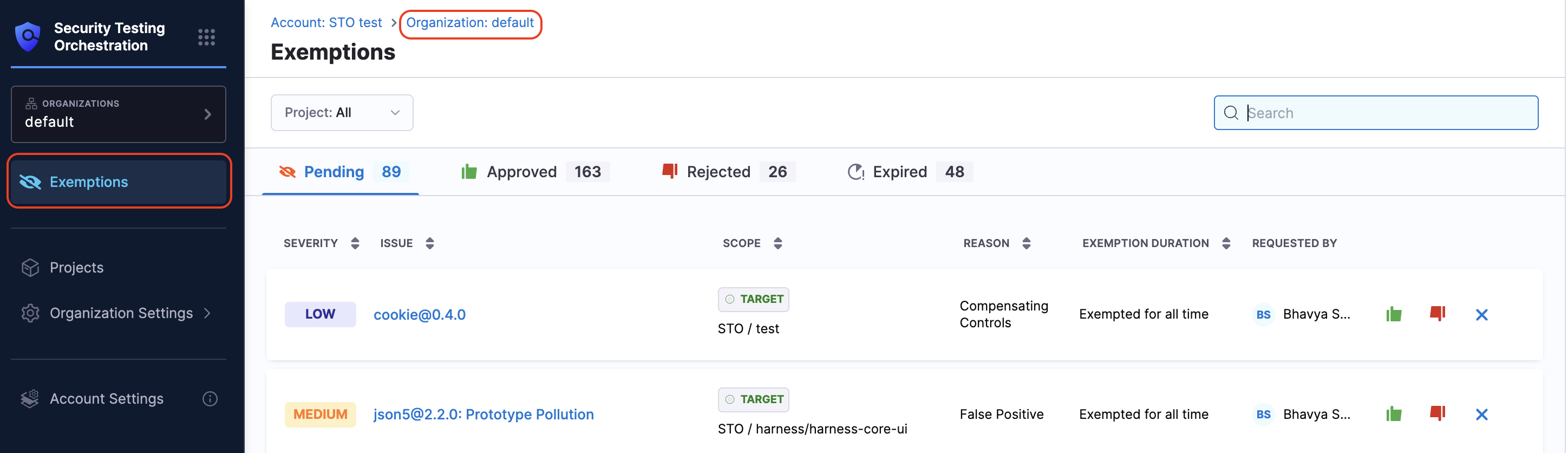
In the Exemptions sections, the requests are displayed in tabs presenting their status, each request in the Pending tab includes:
- Severity: e.g., High
- Issue: e.g.,
json5@2.2.0: Prototype Pollution - Scope: Requested exemption scope – Project, Pipeline, or Target
- Reason: e.g., False Positive, Acceptable Use
- Exemption Duration: e.g., Exempted for all time
- Requested by: User who submitted the request
- Actions: Based on your permissions and request status - Approve, Reject, Cancel, Reopen
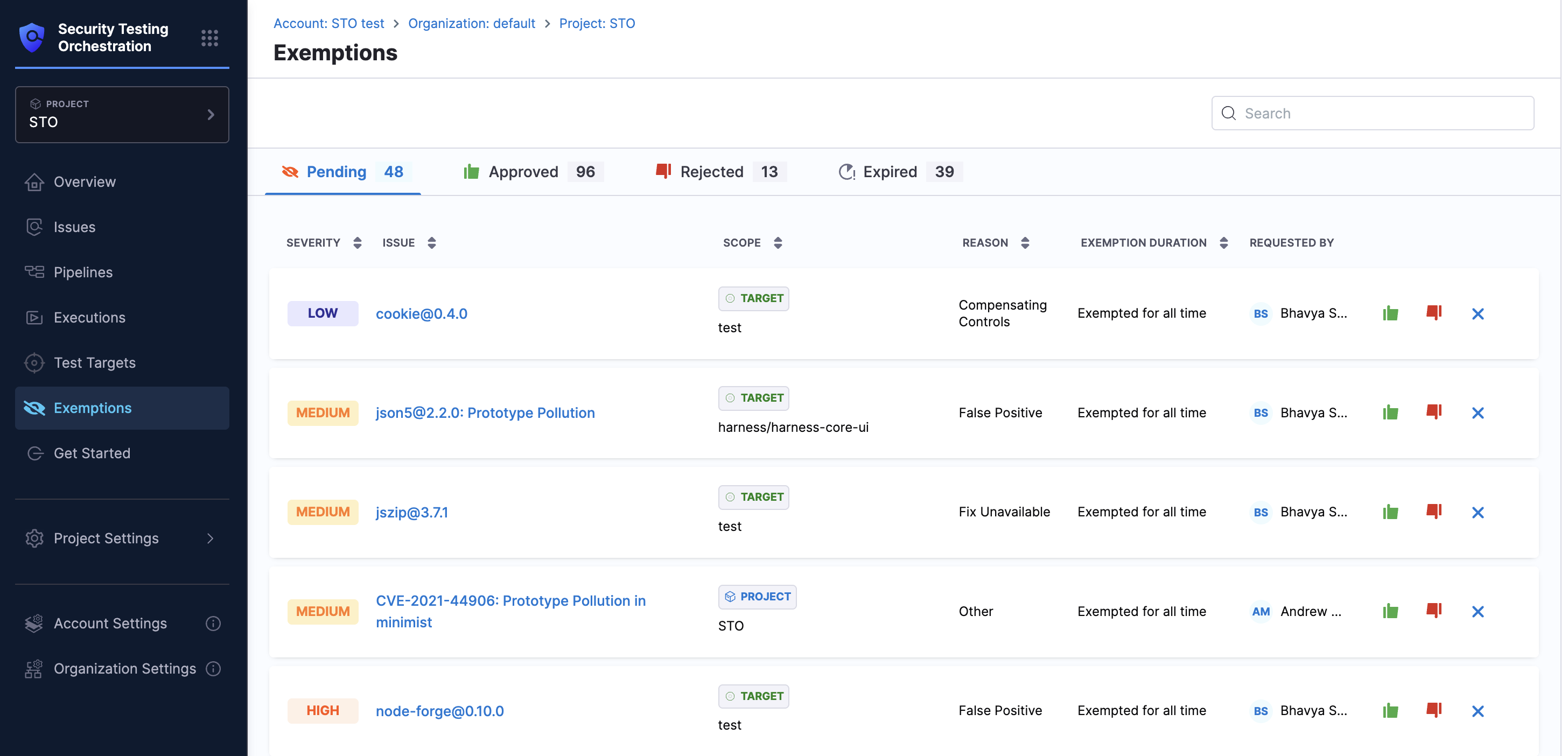
Here are the columns that are specific to status tab.
- Pending: Displays severity, issue, scope, reason, exemption duration, requested by, and action buttons such as Approve, Reject, or Cancel.
- Approved: Shows Approved by, Time remaining, Approved at, Requested by, with actions to Reject or Cancel.
- Rejected: Displays Requested by, Rejected by, and options to Reopen, or Approve and Cancel.
- Expired: Displays Requested by, with options to Approve, Reopen, or Cancel.
For details on exemption request statuses and actions, refer Exemption Request Lifecycle. To learn how to manage requests, refer Manage Issue Exemptions.
Clicking an exemption request opens the Issue Details pane. At the top right of the side panel, you'll see the Exemption Status button, which provides a complete overview of the request along with the actions available to you (based on your permissions).
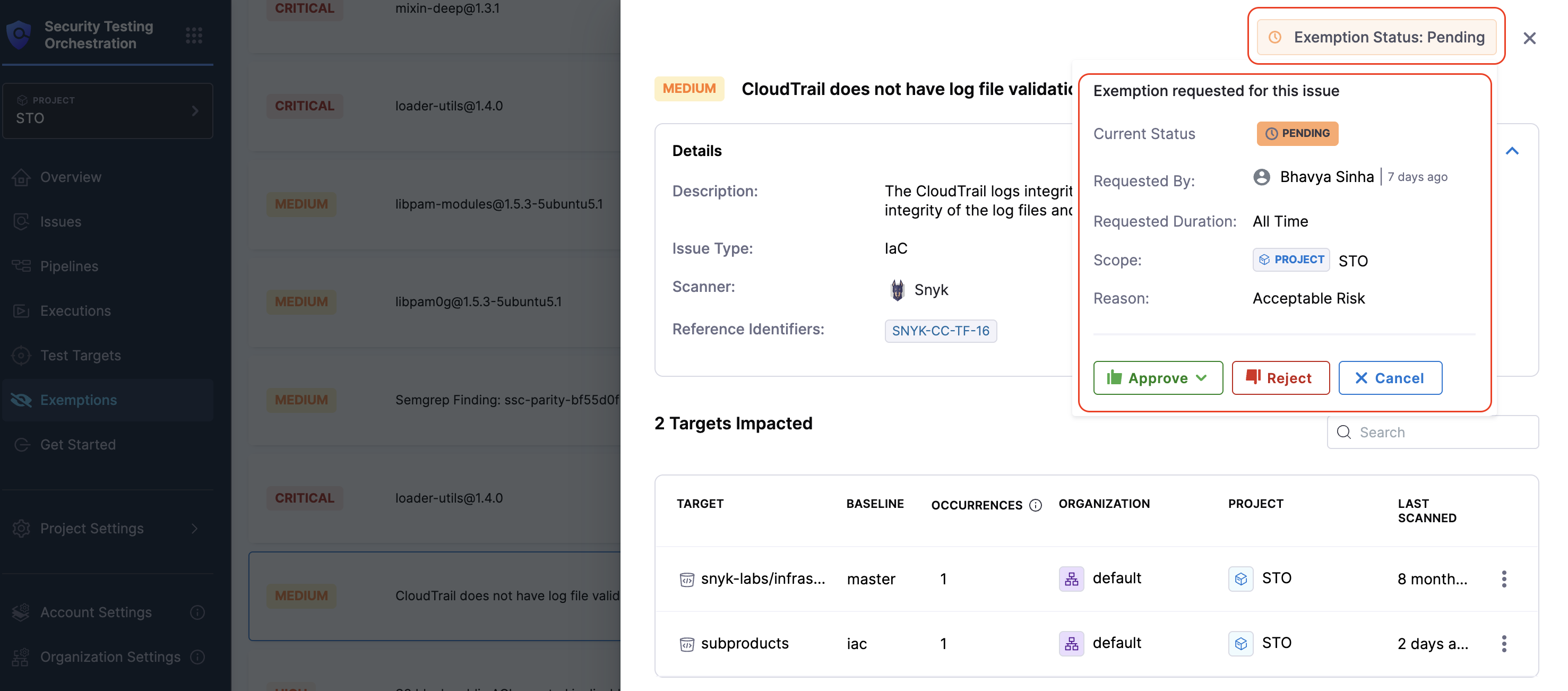
Clicking on the Exemption Status button shows:
- Current Status: Indicates the state of the request —
Pending,Approved,Rejected. - Requested By: Displays the user who created the exemption request and the relative time since it was submitted (e.g.,
David · 7 days ago). - Requested Duration: Shows the time period for which the exemption is requested (e.g.,
7 days,30 days). - Scope: Indicates the exemption's intended application scope, such as Target-level, Pipeline-level, or Project-level.
- Reason: Selected justification category provided during request creation (e.g.,
Acceptable Risk,False Positive,Not Exploitableetc.). - Comments: Displays the latest comment added by a reviewer during the approval or rejection process.
- Description: Optional detailed context added by the requester.
- Response Actions: If you have the required permissions, available actions include Approve, Reject, Cancel, or Re-open, depending on the current request state.
View exemptions at the Project level
- Make sure you have the required permissions to view the requests.
- In your Harness project, go to the left navigation and click Exemptions.
This page displays exemption requests from the selected project.
View exemptions at the Organization level
To view all exemption requests across projects in an organization:
- Make sure you have the required permissions to view the requests.
- In Harness, select the Organization from the top breadcrumb.
- In the left navigation, click Exemptions.
This page displays exemption requests from all projects within the selected organization that you have access to.
View exemptions at the Account level
To view exemption requests across the entire account:
- Make sure you have the required permissions to view the requests.
- In Harness, select the Account from the top breadcrumb.
- In the left navigation, click Exemptions.
This page displays exemption requests from all projects across the organizations you have access to.