Ingest Software Bill of Materials (SBOM) data into SCS
Harness SCS offers flexible SBOM management. It can ingest SBOMs generated from Security Testing Orchestration (STO) scanner steps, like the Aqua Trivy STO step, provided the SBOM is in JSON format (SPDX or CycloneDX). This guide details configuring a pipeline to seamlessly ingest SBOMs generated by Trivy. Similarly, you can follow the same steps for the other STO scanners (Blackduck, Snyk).
Alternatively, you can leverage built-in tools in SCS for SBOM generation or ingest SBOMs from any external tool. Refer to our dedicated guides for these functionalities:
Generate the keys for SBOM Attestation - optional
For enhanced trust and verification of your SBOM's integrity, the SBOM Orchestration step offers optional signing and attestation generation feature. This functionality requires a private key, password for attestation and corresponding public key for attestation verification. If you choose to skip the SBOM attestation, you can proceed without generating the and storing these keys.
-
Generate the keys: Begin by generating the keys using Cosign.
- Install Cosign
- Run the command
cosign generate-key-pairto generate the key pair in theecdsa-p256,rsa-2048, orrsa-4096format. - Make sure to note the password used for generating the key pairs. This password is needed along with the private key for performing the attestation.
- This command will generate a private key as a
.keyfile and a public key as a.pubfile.
-
Securely store the keys: Safeguard the generated keys by securely storing them as Harness file secrets. The SCS module also supports HashiCorp Vault, allowing you to use your keys from the vault.
Configure the STO scan step to generate SBOM
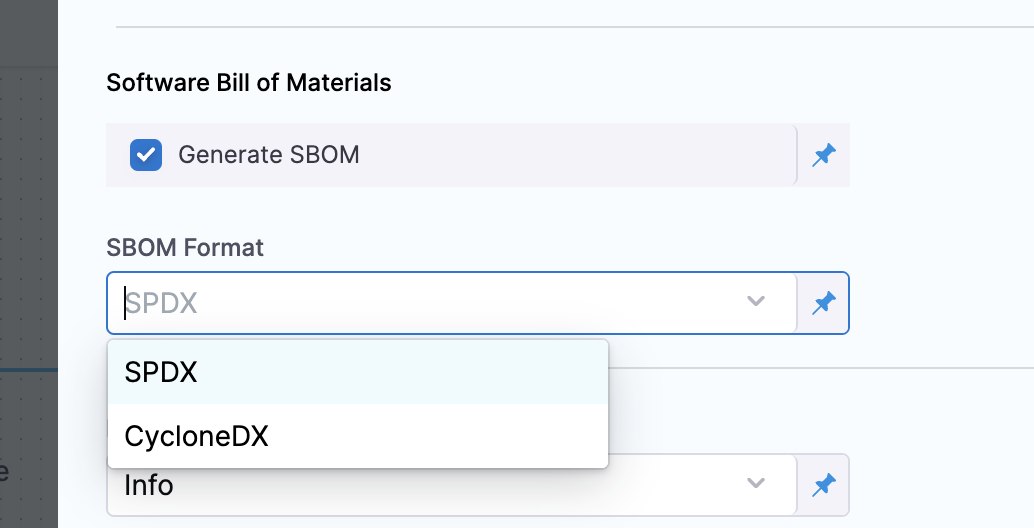
Configure an STO scanner step, such as the Aqua Trivy STO step, and make sure you select Generate SBOM and the SBOM Format.
Get the SBOM file path
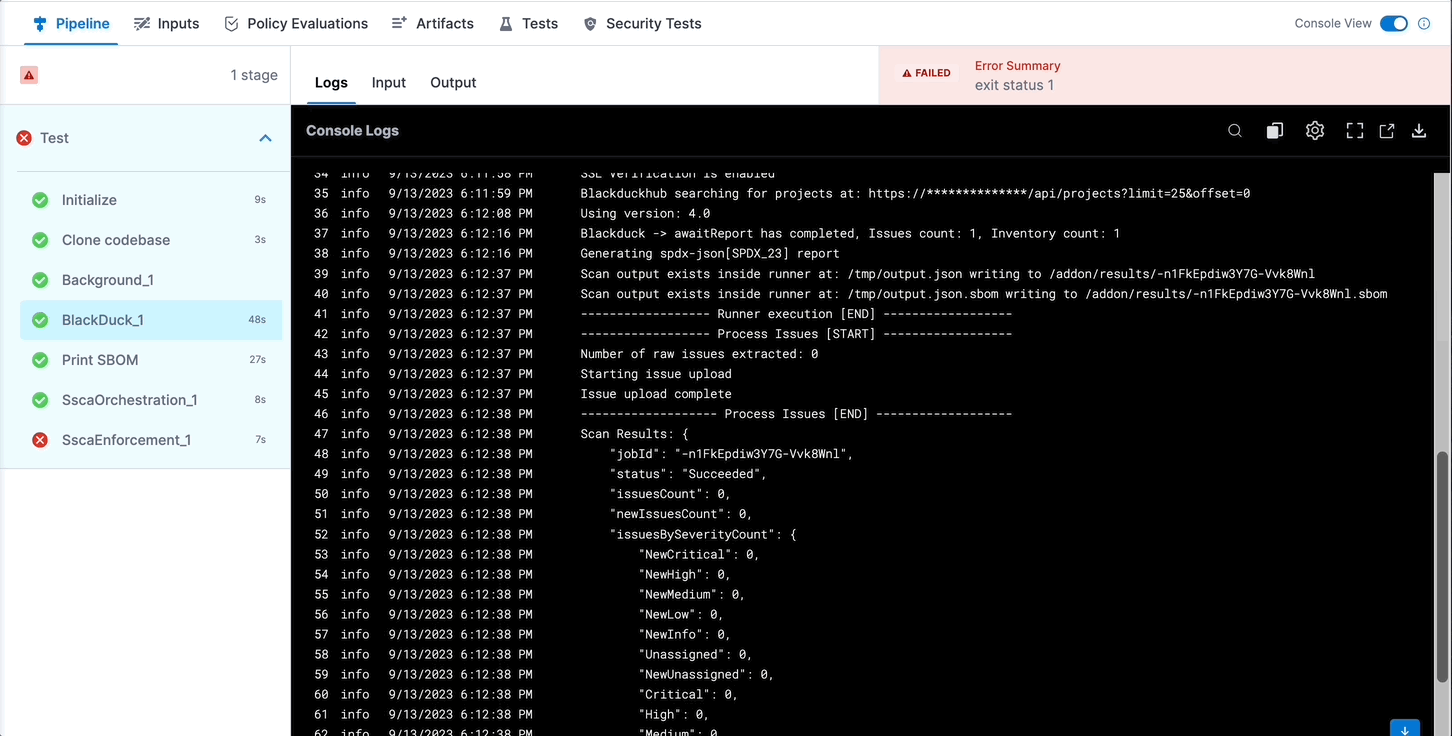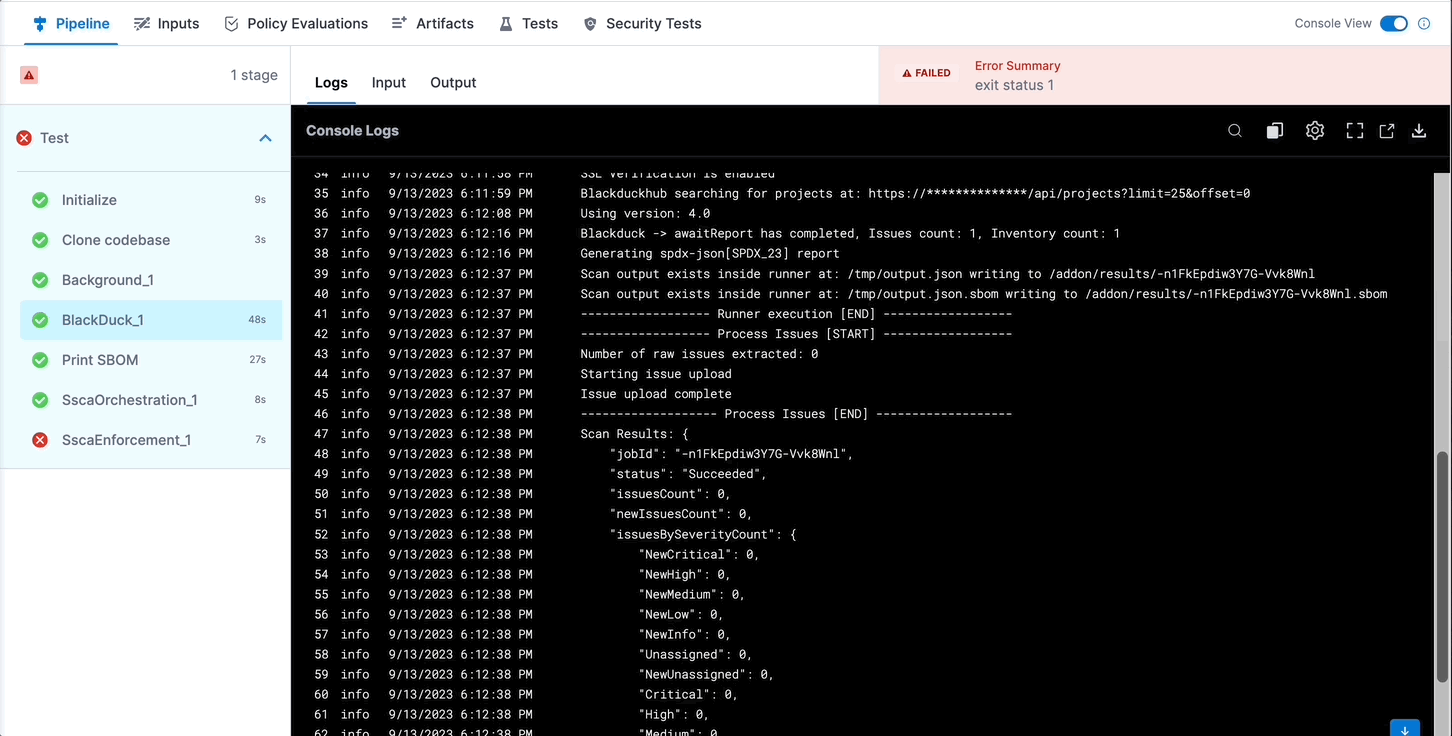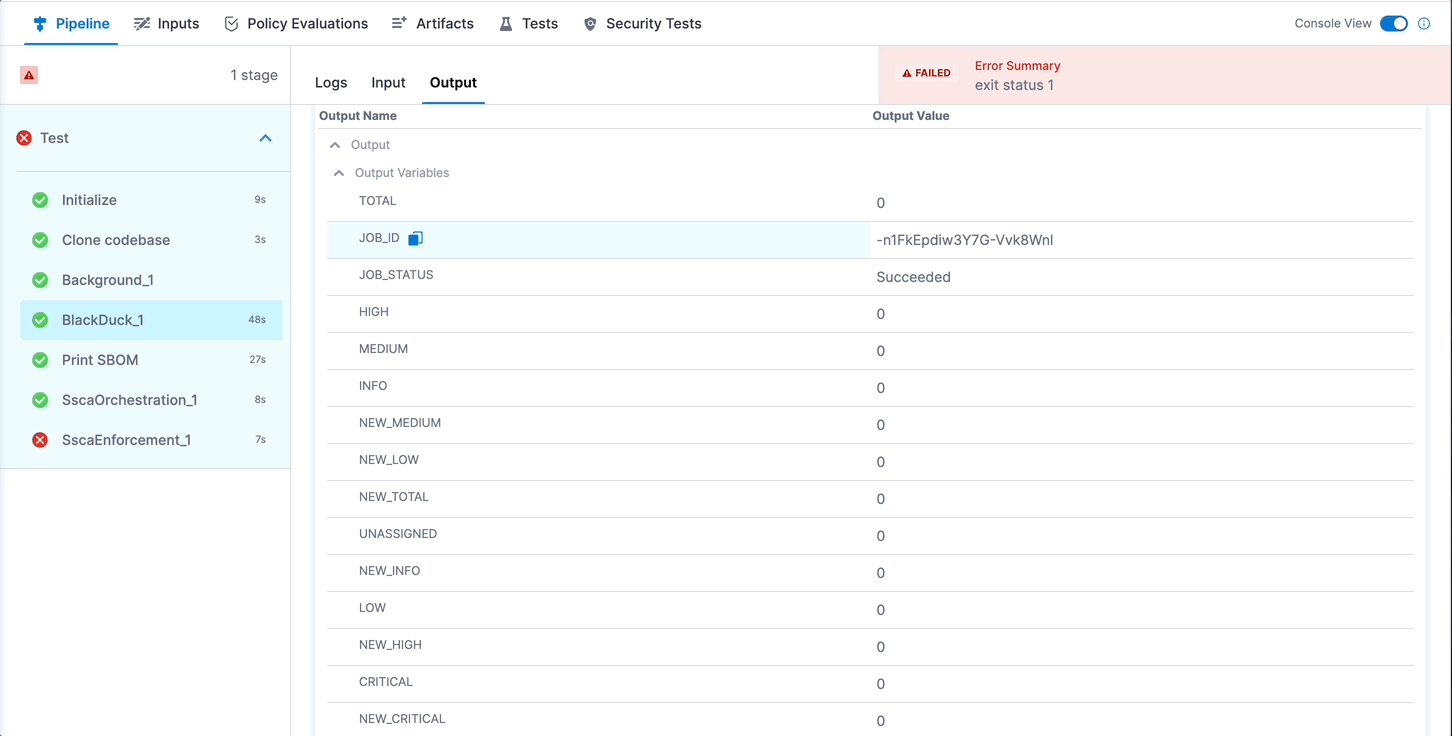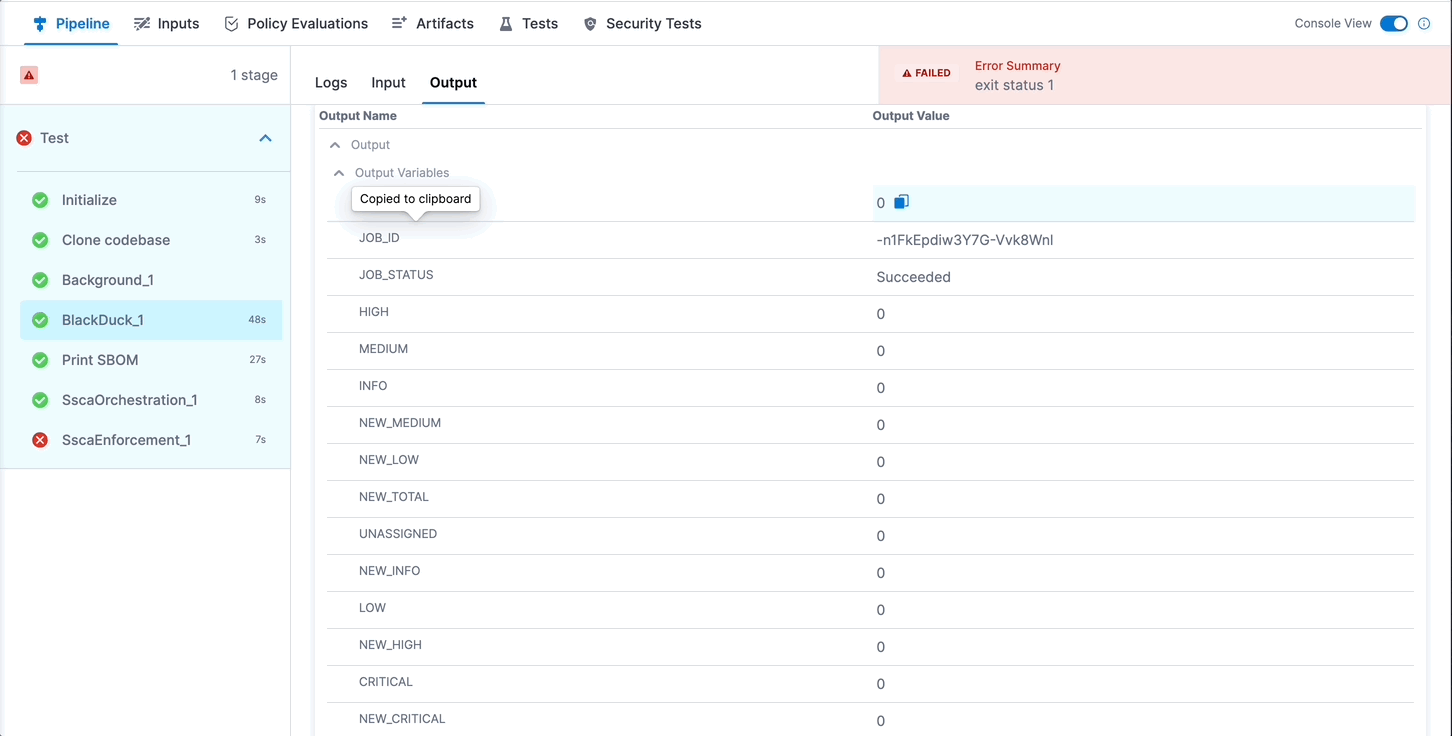
The Aqua Trivy STO step creates a JOB_ID output variable that you can use to reference the SBOM file path in the SBOM Orchestration step.
-
Replace
STAGE_IDandSTEP_IDin the following Harness expression with the stage ID and step ID for your Aqua Trivy STO step.<+pipeline.stages.STAGE_ID.spec.execution.steps.STEP_ID.output.outputVariables.JOB_ID> -
Use the expression in your SBOM file path. The exact path depends on where your scanner outputs SBOM files. For example, this filepath references an Aqua Trivy STO step with the ID
myaquatrivystepin a stage with the IDmybuildstage:/addon/results/<+pipeline.stages.mybuildstage.spec.execution.steps.myaquatrivystep.output.outputVariables.JOB_ID>.sbom
Alternately, you can get the output path and output variable expression from a previous run of the same pipeline. To do this, go to the execution details page, select the stage with the STO scanner step, and then select the STO scanner step. In the step's logs, you can find the output path, and you can get the output variable from the Output tab.
Configure the SBOM Orchestration step
Add an SBOM Orchestration step and configure to ingest the SBOM.
SBOM Orchestration step in deploy stage can only be used in the Containerized Step Groups
-
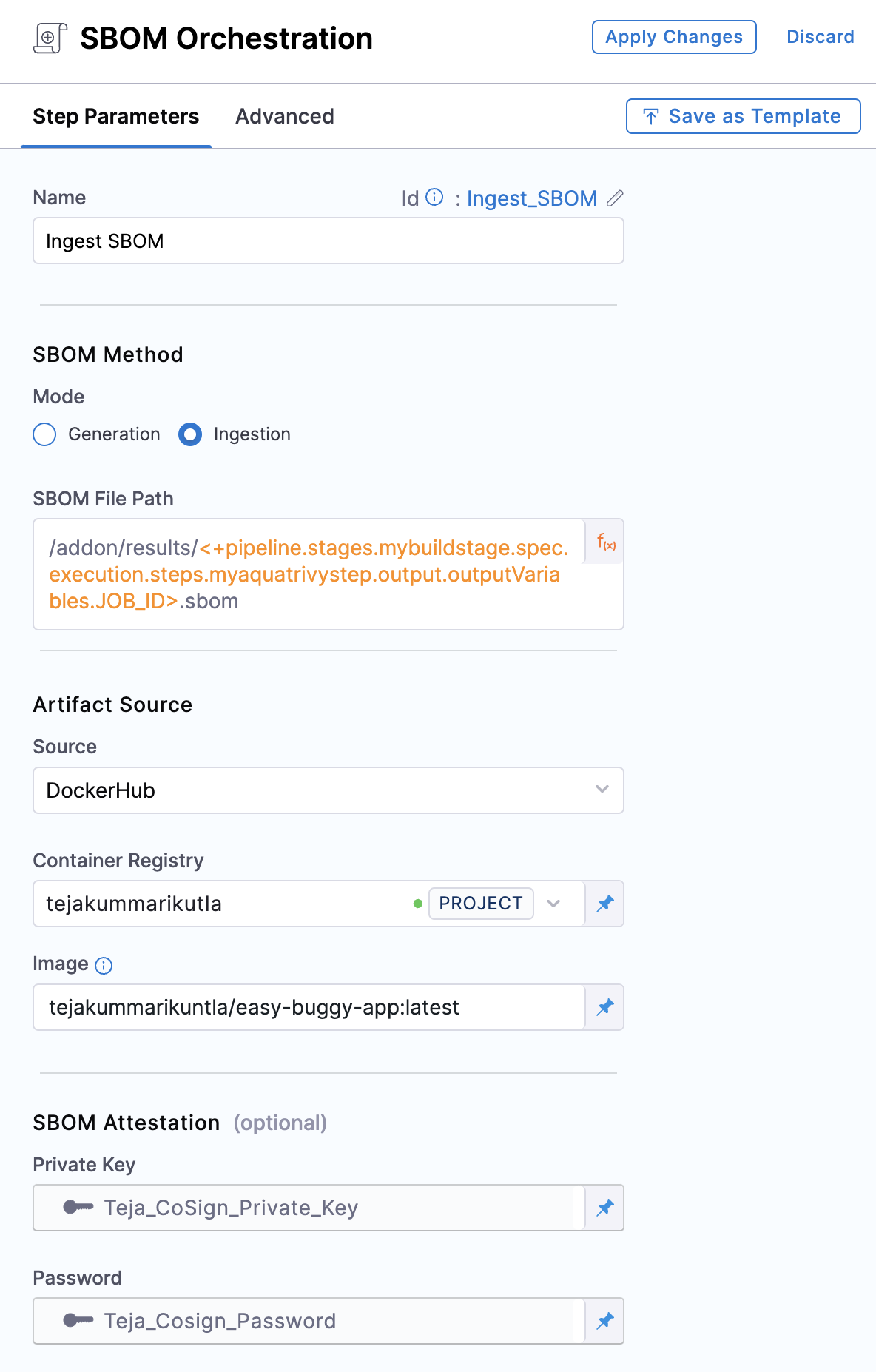
Step Mode: Set the step mode to Ingestion.
-
SBOM File Path: enter the SBOM file path that uses the
JOB_IDvalue, as detailed in Get the SBOM file path. -
Source: Set the source, which can be DockerHub, ECR, GCR, ACR or Repository. Depending on your selection, a unique set of fields will appear, each specific to the source you've chosen. Address these fields as required, this is similar to configuring the source in SBOM Orchestration step. For more details of what each field entails, please refer to the documentation on SBOM Orchestration. If you are using DockerHub, you can follow along.
-
Image:, Enter the name of your image with tag, such as
my-docker-org/repo-name:tag.Generate key pairs using Cosign for SBOM Attestation
To perform the attestation process, you need to input the private key and password. Use Cosign to generate the keys in the ecdsa-p256 format. Here’s how to generate them:
- Install Cosign
- Run the command
cosign generate-key-pairto generate the key pairs. - Make sure to note the password used for generating the key pairs. This password is needed along with the private key for performing the attestation.
- This command will generate a private key as a
.keyfile and a public key as a.pubfile. To securely store these files, use Harness file secret.
-
Private Key (optional): Input your Private key from the Harness file secret.
-
Password (optional): Input your Password for the Private key from the Harness file secret.