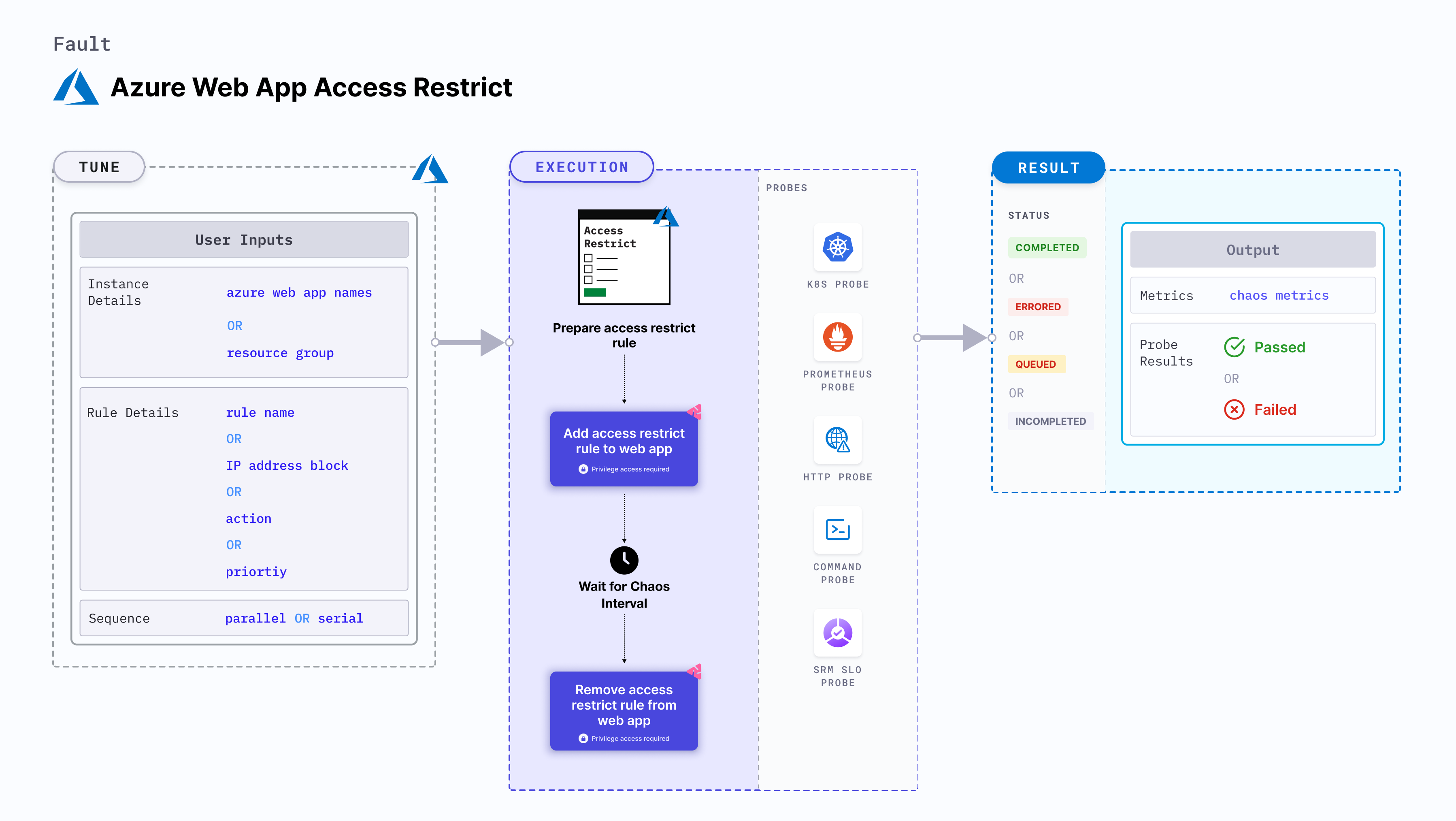
Azure web app access restrict
Azure web app access restrict causes a split brain condition by restricting the access to an application service instance.
- This fault checks if the requests have been serviced and recovery is automated after the restrictions have been lifted.
- It checks the performance of the application (or process) running on the instance.
Use cases
Azure web app access restrict determines the resilience of an application when access to a specific application service instance is restricted.
Prerequisites
- Kubernetes >= 1.17
- Appropriate Azure access to the web applications.
- The target Azure web application should be in the running state.
- Use Azure file-based authentication to connect to the instance using Azure GO SDK. To generate the auth file, run
az ad sp create-for-rbac --sdk-auth > azure.authAzure CLI command. - Kubernetes secret should contain the auth file created in the previous step in the
CHAOS_NAMESPACE. Below is a sample secret file:
apiVersion: v1
kind: Secret
metadata:
name: cloud-secret
type: Opaque
stringData:
azure.auth: |-
{
"clientId": "XXXXXXXXX",
"clientSecret": "XXXXXXXXX",
"subscriptionId": "XXXXXXXXX",
"tenantId": "XXXXXXXXX",
"activeDirectoryEndpointUrl": "XXXXXXXXX",
"resourceManagerEndpointUrl": "XXXXXXXXX",
"activeDirectoryGraphResourceId": "XXXXXXXXX",
"sqlManagementEndpointUrl": "XXXXXXXXX",
"galleryEndpointUrl": "XXXXXXXXX",
"managementEndpointUrl": "XXXXXXXXX"
}
If you change the secret key name from azure.auth to a new name, ensure that you update the AZURE_AUTH_LOCATION environment variable in the chaos experiment with the new name. AZURE_AUTH_LOCATION is variable that describes path to the authetication file which uses the default value in most cases.
Mandatory tunables
| Tunable | Description | Notes |
|---|---|---|
| AZURE_WEB_APP_NAMES | Name of Athe zure web app services to target. | Comma-separated names of the web applications. For more information, go to restrict by name. |
| RESOURCE_GROUP | The name of the resource group for the target web app | For example, TeamDevops. For more information, go to resource group field in the YAML file. |
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| RULE_NAME | Rule name that is added as a part of the chaos injection. | If this is not provided, the fault uses the default name, i.e. litmus-experiment-rule. For more information, go to restrict with custom rule. |
| IP_ADDRESS_BLOCK | IP address (or CIDR range) for the rule. | Defaults to 0.0.0.0/0. For more information, go to restrict for a CIDR range. |
| ACTION | Action you wish to perfrom with the rule. | Defaults to deny. Also supports allow action. For more information, go to restrict with action. |
| PRIORITY | Priority of the rule, wherein lower the number, higher is the priority and vice-versa. | Defaults to 300. For more information, refer restrict with priority. |
| TOTAL_CHAOS_DURATION | Duration that you specify, through which chaos is injected into the target resource (in seconds). | Defaults to 30s. For more information, go to duration of the chaos. |
| DEFAULT_HEALTH_CHECK | Determines if you wish to run the default health check which is present inside the fault. | Default: 'true'. For more information, go to default health check. |
| CHAOS_INTERVAL | Time interval between two successive instance power offs (in seconds). | Defaults to 30s. For more information, go to chaos interval. |
| SEQUENCE | Sequence of chaos execution for multiple instances. | Defaults to parallel. Also supports serial sequence. For more information, go to sequence of chaos execution. |
| RAMP_TIME | Period to wait before and after injecting chaos (in seconds). | For example, 30s. For more information, go to ramp time. |
Web app access restrict by name
It specifies a comma-separated list of web application names subject to chaos. Tune it by using the AZURE_WEB_APP_NAMES environment variable.
Use the following example to tune it:
# access restrict on target web app by their names
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
chaosServiceAccount: litmus-admin
experiments:
- name: azure-web-access-restrict
spec:
components:
env:
# comma separated names of the target web apps
- name: AZURE_WEB_APP_NAMES
value: 'webApp-01,webApp-02'
# name of the resource group
- name: RESOURCE_GROUP
value: 'chaos-rg'
- name: TOTAL_CHAOS_DURATION
VALUE: '60'
Access restrict for a certain CIDR range
It specifies a CIDR range used in the rule. Tune it by using the IP_ADDRESS_BLOCK environment variable.
Use the following example to tune it:
# restrict the web app for a certain
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
chaosServiceAccount: litmus-admin
experiments:
- name: azure-web-access-restrict
spec:
components:
env:
# provide the value of ip address/CIDR Range
- name: IP_ADDRESS_BLOCK
value: '0.0.0.0/0'
# name of the resource group
- name: RESOURCE_GROUP
value: 'chaos-rg'
- name: TOTAL_CHAOS_DURATION
VALUE: '60'
Access restrict with action
It specifies whether to allow or deny the traffic for the rule provided. Tune it by using the ACTION environment variable. By default, it is set to deny.
Use the following example to tune it:
# defines the action for the given network rule
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
chaosServiceAccount: litmus-admin
experiments:
- name: azure-web-access-restrict
spec:
components:
env:
# Provide the action for a rule
- name: ACTION
value: 'deny'
# duration for the chaos execution
- name: TOTAL_CHAOS_DURATION
VALUE: '60'
Access restrict with priority
It specifies the priority of the network rule created by the fault. Tune it by using the PRIORITY environment variable. By default, it is set to 300.
Use the following example to tune it:
# defines the priority for the network rule
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
chaosServiceAccount: litmus-admin
experiments:
- name: azure-web-access-restrict
spec:
components:
env:
# Provide the priority for a rule
- name: PRIORITY
value: '300'
# duration for the chaos execution
- name: TOTAL_CHAOS_DURATION
VALUE: '60'
Access restrict with custom rule name
It specifies a custom rule name for the chaos. Tune it by using the RULE_NAME environment variable.
Use the following example to tune it:
# defines the rule name for the network rule created
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
chaosServiceAccount: litmus-admin
experiments:
- name: azure-web-access-restrict
spec:
components:
env:
# Provide the name of the rule
- name: RULE_NAME
value: 'chaos-rule'