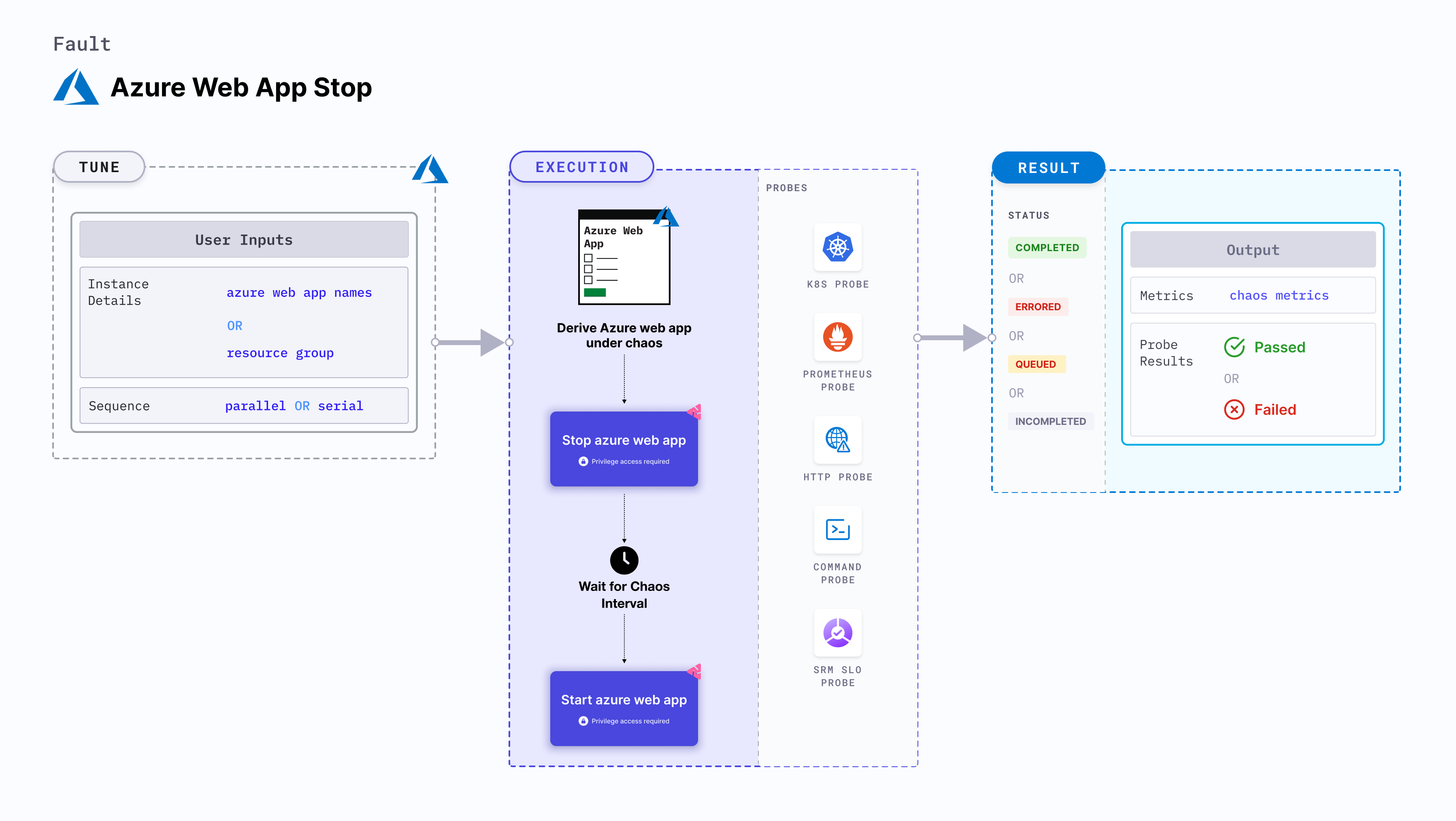
Azure web app stop
Azure web app stop shuts down the application. It checks whether the requests have been re-routed to another instance on the application service.
Use cases
Azure web app stop
- Determines the resilience of a web application to unplanned halts (or stops).
- Determines the resilience based on how quickly and efficiently the application recovers from the failure by re-routing the traffic to a different instance on the same application service.
Prerequisites
- Kubernetes >= 1.17
- Appropriate Azure access to start and stop the web applications.
- The target Azure web application should be in the running state.
- Use Azure file-based authentication to connect to the instance using Azure GO SDK. To generate the auth file, run
az ad sp create-for-rbac --sdk-auth > azure.authAzure CLI command. - Kubernetes secret should contain the auth file created in the previous step in the
CHAOS_NAMESPACE. Below is a sample secret file:
apiVersion: v1
kind: Secret
metadata:
name: cloud-secret
type: Opaque
stringData:
azure.auth: |-
{
"clientId": "XXXXXXXXX",
"clientSecret": "XXXXXXXXX",
"subscriptionId": "XXXXXXXXX",
"tenantId": "XXXXXXXXX",
"activeDirectoryEndpointUrl": "XXXXXXXXX",
"resourceManagerEndpointUrl": "XXXXXXXXX",
"activeDirectoryGraphResourceId": "XXXXXXXXX",
"sqlManagementEndpointUrl": "XXXXXXXXX",
"galleryEndpointUrl": "XXXXXXXXX",
"managementEndpointUrl": "XXXXXXXXX"
}
tip
If you change the secret key name from azure.auth to a new name, ensure that you update the AZURE_AUTH_LOCATION environment variable in the chaos experiment with the new name.
Mandatory tunables
| Tunable | Description | Notes |
|---|---|---|
| AZURE_WEB_APP_NAMES | Name of the Azure web application services to target. | Comma-separated names of web applications. For more information, go to stop Azure web app by name. |
| RESOURCE_GROUP | Name of the resource group for the target web applications. | All the web applications must belong to the same resource group. For more information, go to resource group field in the YAML file. |
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| TOTAL_CHAOS_DURATION | Duration that you specify, through which chaos is injected into the target resource (in seconds). | Defaults to 30s. For more information, go to duration of the chaos. |
| CHAOS_INTERVAL | Time interval between two successive instance power offs (in seconds). | Defaults to 30s. For more information, go to chaos interval. |
| DEFAULT_HEALTH_CHECK | Determines if you wish to run the default health check which is present inside the fault. | Default: 'true'. For more information, go to default health check. |
| SEQUENCE | Sequence of chaos execution for multiple instances. | Defaults to parallel. Also supports serial sequence. For more information, go to sequence of chaos execution. |
| RAMP_TIME | Period to wait before and after injecting chaos (in seconds). | For example, 30s. For more information, go to ramp time. |
Stop web application by name
It specifies a comma-separated list of web application names subject to chaos. Tune it by using the AZURE_WEB_APP_NAMES environment variable.
Use the following example to tune it:
# stop web app for a certain chaos duration
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
chaosServiceAccount: litmus-admin
experiments:
- name: azure-web-app-stop
spec:
components:
env:
# comma-separated names of the Azure web app
- name: AZURE_WEB_APP_NAMES
value: 'webApp-01,webApp-02'
# name of the resource group
- name: RESOURCE_GROUP
value: 'chaos-rg'
- name: TOTAL_CHAOS_DURATION
VALUE: '60'