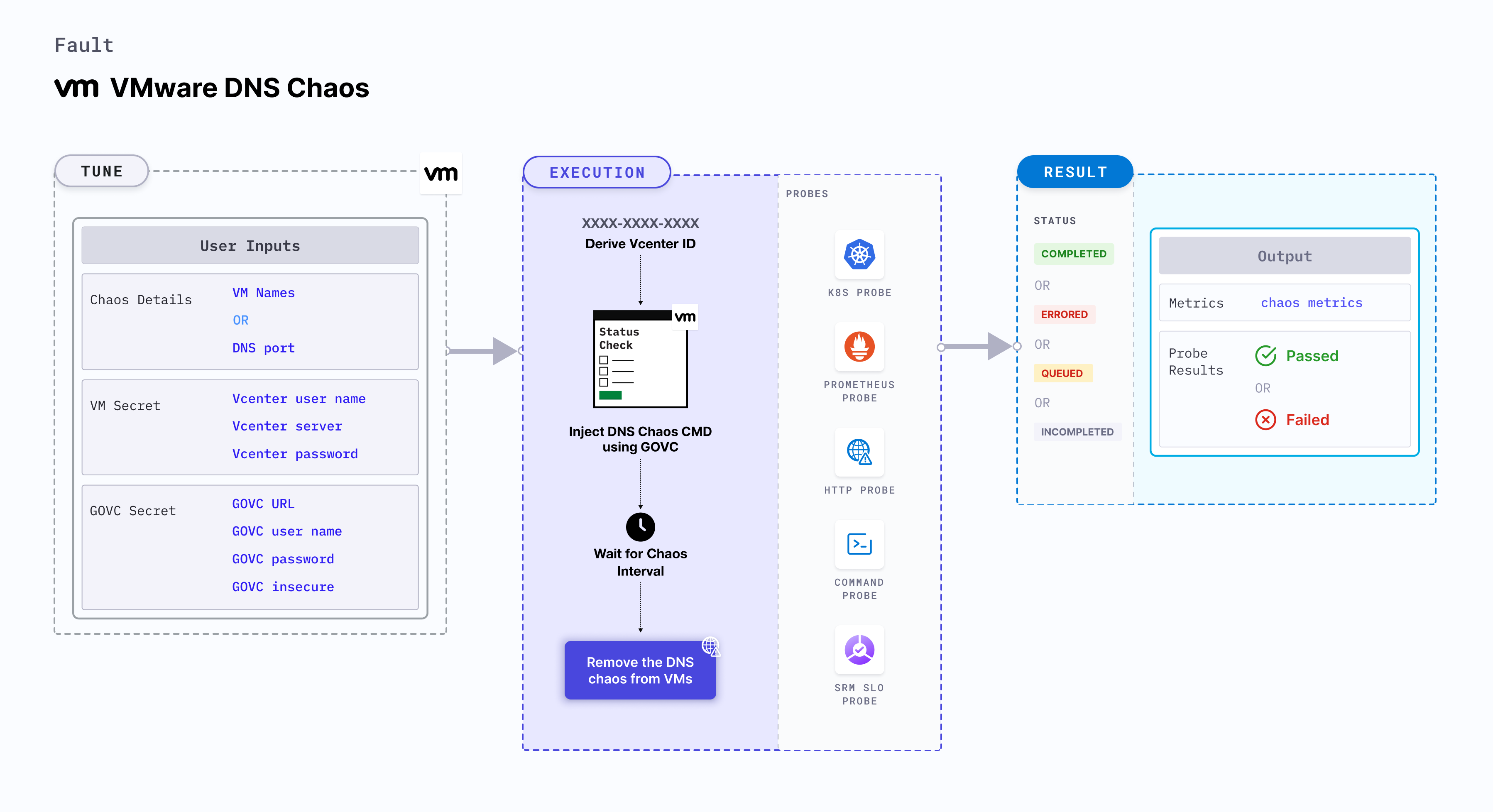
VMware DNS chaos
VMware DNS chaos causes DNS errors in the VMware VMs which results in the DNS server being unavailable or malfunctioning for a specific duration. It checks the performance of the application (or process) running on the VMware VMs.
Use cases
- VMware DNS chaos causes DNS errors on the target VMs which results in unavailability (or distorted) network connectivity from the VM to the target hosts.
- It provides a hypothesis wherein certain services of an application could be unreachable from the VM.
- It determines how DNS errors impact the infrastructure and standalone tasks in the application.
- It simulates unavailability of DNS server, that is, loss of access to any external domain from a given microservice.
- It simulates malfunctioning of DNS server, that is, loss of access to specific domains from a given microservice, loss of access to cloud provider dependencies, and loss of access to specific third party services.
Prerequisites
- Kubernetes > 1.16 is required to execute this fault.
- Execution plane should be connected to vCenter and host vCenter on port 443.
- VMware tool should be installed on the target VM with remote execution enabled.
- The VM should be in a healthy state before and after injecting chaos.
- Appropriate vCenter permissions should be provided to access the hosts and the VMs.
- Kubernetes secret has to be created that has the Vcenter credentials in the
CHAOS_NAMESPACE. VM credentials can be passed as secrets or as aChaosEngineenvironment variable. Below is a sample secret file:
apiVersion: v1
kind: Secret
metadata:
name: vcenter-secret
namespace: litmus
type: Opaque
stringData:
VCENTERSERVER: XXXXXXXXXXX
VCENTERUSER: XXXXXXXXXXXXX
VCENTERPASS: XXXXXXXXXXXXX
Mandatory tunables
| Tunable | Description | Notes |
|---|---|---|
| VM_NAME | Name of the target VM(s). | Multiple comma-separated names can be provided. For example, vm-1,vm-2. |
| VM_USER_NAME | Username of the target VM(s). | Multiple usernames can be provided as comma-separated values (when there are multiple VMs subject to chaos). It also helps run the govc command. |
| VM_PASSWORD | Password for the target VM(s). | It helps run the govc command. |
| PORT | DNS Port | Defaults to 54. For more information, go to DNS chaos with port. |
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| TOTAL_CHAOS_DURATION | Duration that you specify, through which chaos is injected into the target resource (in seconds). | Defaults to 30s. For more information, go to duration of the chaos. |
| CHAOS_INTERVAL | Time interval between two successive instance terminations (in seconds). | Defaults to 30s. For more information, go to chaos interval. |
| SEQUENCE | Sequence of chaos execution for multiple instances. | Defaults to parallel. Supports serial sequence as well. For more information, go to sequence of chaos execution. |
| RAMP_TIME | Period to wait before and after injecting chaos (in seconds). | For example, 30s. For more information, go to ramp time. |
| TARGET_HOSTNAMES | List of the target host names. If it is not provided, all host names (or domains) are targeted. | For example, '["litmuschaos","chaosnative.com"]'. For more information, go to target host names. |
| MATCH_SCHEME | Determines whether the DNS query should exactly match the targets or can be a substring. | Defaults to exact. For more information, go to DNS chaos with match scheme. |
| UPSTREAM_SERVER | Custom upstream server to which the intercepted DNS requests will be forwarded. | Defaults to the server mentioned in resolv.conf file. For more information, go to DNS chaos with upstream server. |
| DEFAULT_HEALTH_CHECK | Determines if you wish to run the default health check which is present inside the fault. | Default: 'true'. For more information, go to default health check. |
Secret tunables
| Tunable | Description | Notes |
|---|---|---|
| GOVC_URL | vCenter server URL used to perform API calls using the govc command. | It is derived from a secret. |
| GOVC_USERNAME | Username of the vCenter server used for authentication purposes. | It can be set up using a secret. |
| GOVC_PASSWORD | Password of the vCenter server used for authentication purposes. | It can be set up using a secret. |
| GOVC_INSECURE | Runs the govc command in insecure mode. It is set to true. | It can be set up using a secret. |
Run DNS chaos with port
It specifies the DNS port where DNS chaos is injected. Tune it by using the PORT environment variable.
Use the following example to tune it:
# induces DNS chaos on the VMware VM
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: VMware-engine
spec:
engineState: "active"
chaosServiceAccount: litmus-admin
experiments:
- name: VMware-DNS-chaos
spec:
components:
env:
- name: PORT
value: '54'
- name: VM_NAME
value: 'vm-1,vm-2'
- name: VM_USER_NAME
value: 'ubuntu,debian'
- name: VM_PASSWORD
value: '123,123'
Run DNS chaos with target host names
It specifies the list of the target host names into which DNS chaos is injected. Tune it by using the TARGET_HOSTNAMES environment variable.
Use the following example to tune it:
# induces DNS chaos on the VMware VMs
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
chaosServiceAccount: litmus-admin
experiments:
- name: VMware-DNS-chaos
spec:
components:
env:
# list of target host names
- name: TARGET_HOSTNAMES
value: '["litmuschaos","chaosnative.com"]'
- name: VM_NAME
value: 'vm-1,vm-2'
- name: VM_USER_NAME
value: 'ubuntu,debian'
- name: VM_PASSWORD
value: '123,123'
Run DNS chaos with match scheme
It specifies whether the DNS query should exactly match the targets or can be a substring. Tune it by using the MATCH_SCHEME environment variable.
Use the following example to tune it:
# induces DNS chaos on the VMware VMs
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
chaosServiceAccount: litmus-admin
experiments:
- name: VMware-DNS-chaos
spec:
components:
env:
# match scheme type
- name: MATCH_SCHEME
value: 'exact'
- name: VM_NAME
value: 'vm-1,vm-2'
- name: VM_USER_NAME
value: 'ubuntu,debian'
- name: VM_PASSWORD
value: '123,123'
Run DNS chaos with upstream server
It specifies the custom upstream server to which the intercepted DNS requests are forwarded. It defaults to the server mentioned in the resolv.conf file. Tune it by using the UPSTREAM_SERVER environment variable.
Use the following example to tune it:
# induces DNS chaos on the VMware VMs
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
chaosServiceAccount: litmus-admin
experiments:
- name: VMware-DNS-chaos
spec:
components:
env:
# name of the upstream server
- name: UPSTREAM_SERVER
value: '8.8.8.8'
- name: VM_NAME
value: 'vm-1,vm-2'
- name: VM_USER_NAME
value: 'ubuntu,debian'
- name: VM_PASSWORD
value: '123,123'