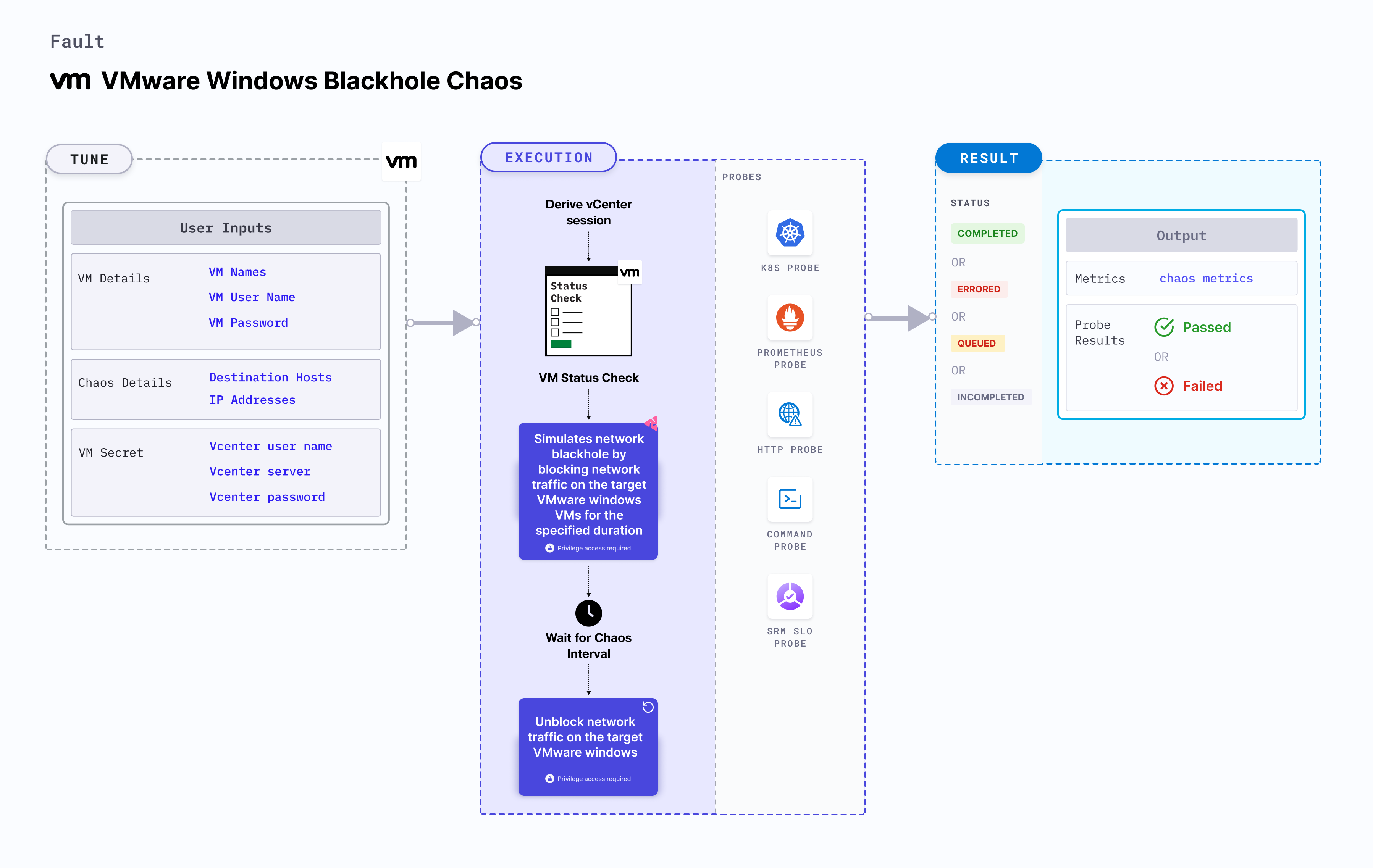
VMware Windows blackhole chaos
VMware Windows blackhole chaos simulates a network blackhole scenario on Windows OS based VMware VM. It checks the performance of the application running on the VMware Windows VMs under network blackhole conditions.
Use cases
VMware Windows blackhole chaos
- Determines the resilience of an application when a network blackhole scenario is simulated on a VMware Windows virtual machine.
- Simulates the situation of network isolation for processes running on the application, which degrades their performance.
- Helps verify the application's ability to handle network failures and its failover mechanisms.
Prerequisites�
- Kubernetes > 1.16 is required to execute this fault.
- Execution plane should be connected to vCenter and host vCenter on port 443.
- VMware tool should be installed on the target VM with remote execution enabled.
- Adequate vCenter permissions should be provided to access the hosts and the VMs.
- Ensure the firewall is active and permissions to modify its rules are granted. Consider using the built-in Administrator user. Learn how to enable it in Windows.
- The VM should be in a healthy state before and after injecting chaos.
- Kubernetes secret has to be created that has the Vcenter credentials in the
CHAOS_NAMESPACE. - VM credentials can be passed as secrets or as a chaos engine environment variable.
apiVersion: v1
kind: Secret
metadata:
name: vcenter-secret
namespace: litmus
type: Opaque
stringData:
VCENTERSERVER: XXXXXXXXXXX
VCENTERUSER: XXXXXXXXXXXXX
VCENTERPASS: XXXXXXXXXXXXX
Mandatory tunables
| Tunable | Description | Notes |
|---|---|---|
| VM_NAME | Name of the target VM. | For example, win-vm-1 |
| VM_USER_NAME | Username of the target VM. | For example, vm-user. |
| VM_PASSWORD | User password for the target VM. | For example, 1234. Note: You can take the password from secret as well. |
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| DESTINATION_HOSTS | Comma separated list of destination hosts to block. | For example, github.com,harness.io. For more information, go to destination hosts. |
| IP_ADDRESSES | Comma separated list of IP addresses to block. | For example, 10.0.0.1,10.0.0.2. For more information, go to IP addresses. |
| TOTAL_CHAOS_DURATION | Duration that you specify, through which chaos is injected into the target resource (in seconds). | Default: 60 s. For more information, go to duration of the chaos. |
| RAMP_TIME | Period to wait before and after injecting chaos (in seconds). | Default: 0 s. For more information, go to ramp time. |
| SEQUENCE | Sequence of chaos execution for multiple instances. | Default: parallel. Supports parallel and serial sequence. For more information, go to sequence of chaos execution. |
| DEFAULT_HEALTH_CHECK | Determines if you wish to run the default health check which is present inside the fault. | Default: 'true'. For more information, go to default health check. |
Destination hosts
The DESTINATION_HOSTS environment variable specifies the destination hosts to block on the target Windows VM.
Use the following example to specify destination hosts:
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
chaosServiceAccount: litmus-admin
experiments:
- name: vmware-windows-blackhole-chaos
spec:
components:
env:
# Name of the VM
- name: VM_NAME
value: 'test-vm-01'
# Destination hosts to block
- name: DESTINATION_HOSTS
value: 'github.com'
IP addresses
The IP_ADDRESSES environment variable specifies the IP addresses to block on the target Windows VM.
Use the following example to specify IP addresses:
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
chaosServiceAccount: litmus-admin
experiments:
- name: vmware-windows-blackhole-chaos
spec:
components:
env:
# Name of the VM
- name: VM_NAME
value: 'test-vm-01'
# IP addresses to block
- name: IP_ADDRESSES
value: '10.0.0.1,10.0.0.2'