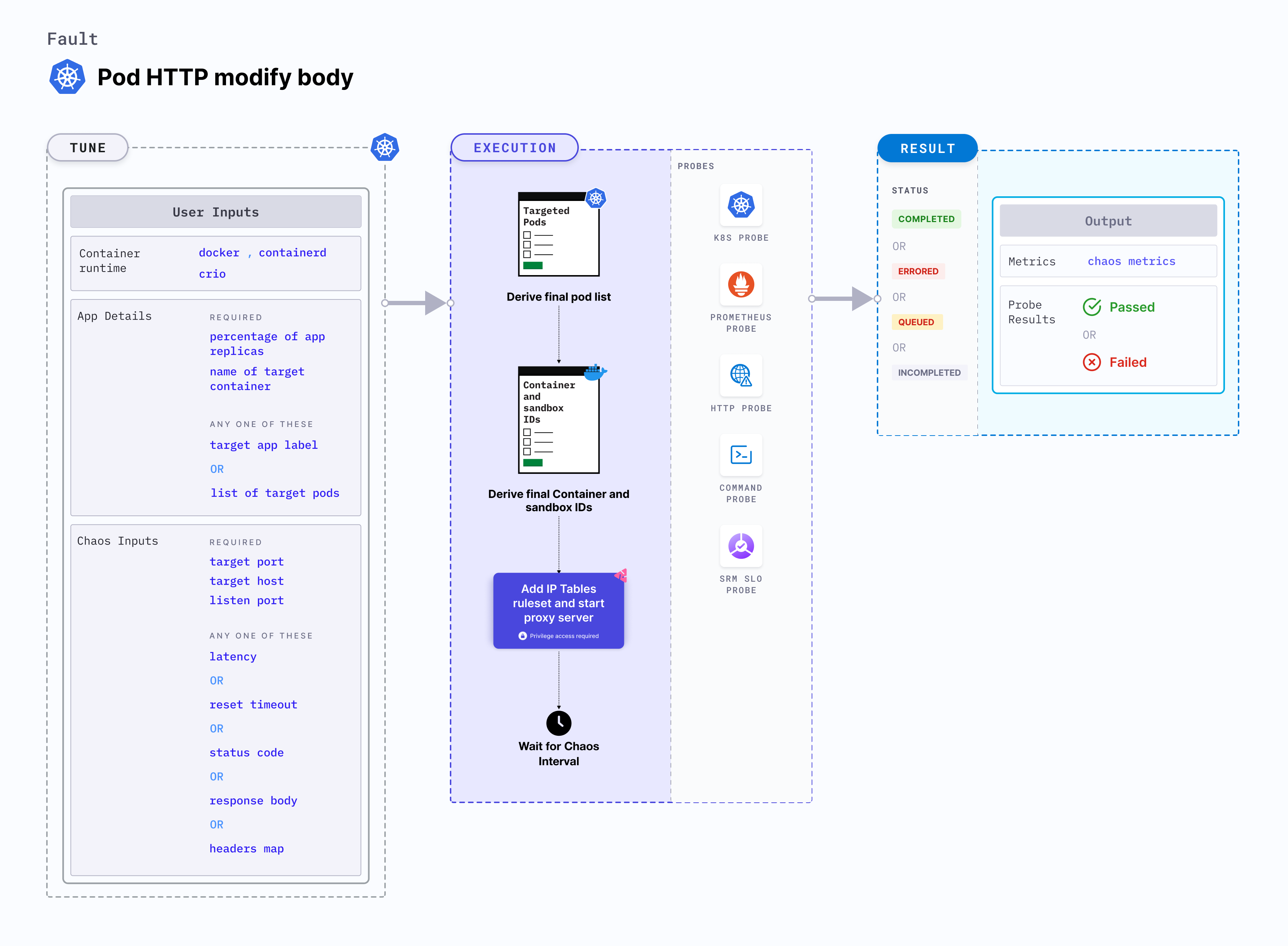
Pod HTTP modify body
Pod HTTP modify body is a Kubernetes pod-level chaos fault that injects chaos on the service whose port is provided using the TARGET_SERVICE_PORT environment variable. This is achieved by starting the proxy server and redirecting the traffic through the proxy server. This fault can be used to overwrite the HTTP response body by providing the new body value as RESPONSE_BODY.
Use cases
Pod HTTP modify body tests the application's resilience to erroneous or incorrect HTTP response body.
Pod HTTP modify body supports HTTP method only.
Permissions required
Below is a sample Kubernetes role that defines the permissions required to execute the fault.
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: hce
name: pod-http-modify-body
spec:
definition:
scope: Cluster # Supports "Namespaced" mode too
permissions:
- apiGroups: [""]
resources: ["pods"]
verbs: ["create", "delete", "get", "list", "patch", "deletecollection", "update"]
- apiGroups: [""]
resources: ["events"]
verbs: ["create", "get", "list", "patch", "update"]
- apiGroups: [""]
resources: ["pods/log"]
verbs: ["get", "list", "watch"]
- apiGroups: [""]
resources: ["deployments, statefulsets"]
verbs: ["get", "list"]
- apiGroups: [""]
resources: ["replicasets, daemonsets"]
verbs: ["get", "list"]
- apiGroups: [""]
resources: ["chaosEngines", "chaosExperiments", "chaosResults"]
verbs: ["create", "delete", "get", "list", "patch", "update"]
- apiGroups: ["batch"]
resources: ["jobs"]
verbs: ["create", "delete", "get", "list", "deletecollection"]
Prerequisites
- Kubernetes > 1.17
- The application pods should be in the running state before and after injecting chaos.
Mandatory tunables
| Tunable | Description | Notes |
|---|---|---|
| TARGET_SERVICE_PORT | Port of the target service. | Defaults to port 80. For more information, go to target service port |
| NODE_LABEL | Node label used to filter the target node if TARGET_NODE environment variable is not set. | It is mutually exclusive with the TARGET_NODE environment variable. If both are provided, the fault uses TARGET_NODE. For more information, go to node label. |
| RESPONSE_BODY | String body to overwrite the HTTP response body. | If no value is provided, response will be an empty body. Defaults to empty body. For more information, go to response body |
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| CONTENT_ENCODING | Encoding type to compress or encode the response body. | Accepted values include gzip, deflate, br, identity. Defaults to none (no encoding). For more information, go to content encoding |
| CONTENT_TYPE | Content type of the response body. | Default: text or plain. For more information, go to content type |
| PROXY_PORT | Port where the proxy listens for requests. | Default: 20000. For more information, go to proxy port |
| NETWORK_INTERFACE | Network interface used for the proxy. | Default: eth0. For more information, go to network interface |
| TOXICITY | Percentage of HTTP requests to be affected. | Default: 100. For more information, go to toxicity |
| CONTAINER_RUNTIME | Container runtime interface for the cluster | Default: containerd. Support values: docker, containerd and crio. For more information, go to container runtime |
| SOCKET_PATH | Path of the containerd or crio or docker socket file. | Default: /run/containerd/containerd.sock. For more information, go to socket path |
| TOTAL_CHAOS_DURATION | Duration of chaos injection (in seconds). | Default: 60 s. For more information, go to duration of the chaos |
| TARGET_PODS | Comma-separated list of application pod names subject to pod HTTP modify body. | If not provided, the fault selects target pods randomly based on provided appLabels. For more information, go to target specific pods |
| PODS_AFFECTED_PERC | Percentage of total pods to target. Provide numeric values. | Default: 0 (corresponds to 1 replica). For more information, go to pod affected percentage |
| RAMP_TIME | Period to wait before and after injecting chaos (in seconds). | For example, 30 s. For more information, go to ramp time |
| SEQUENCE | Sequence of chaos execution for multiple target pods. | Default: parallel. Supports serial and parallel. For more information, go to sequence of chaos execution |
Target service port
Port of the targeted service. Tune it by using the TARGET_SERVICE_PORT environment variable.
The following YAML snippet illustrates the use of this environment variable:
## provide the port of the targeted service
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-http-modify-body
spec:
components:
env:
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
# provide the body string to overwrite the response body
- name: RESPONSE_BODY
value: "2000"
Proxy port
Port on which the proxy server listens for requests. Tune it by using the PROXY_PORT environment variable.
The following YAML snippet illustrates the use of this environment variable:
## provide the port for proxy server
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-http-modify-body
spec:
components:
env:
# provide the port for proxy server
- name: PROXY_PORT
value: "8080"
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
Response body
String body that overwrites the HTTP response body. Tune it by using the RESPONSE_BODY environment variable.
The following YAML snippet illustrates the use of this environment variable:
## provide the response body value
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-http-modify-body
spec:
components:
env:
# provide the body string to overwrite the response body
- name: RESPONSE_BODY
value: "2000"
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
Toxicity
Percentage of the total number of HTTP requests to be affected. Tune it by using the TOXICITY environment variable.
The following YAML snippet illustrates the use of this environment variable:
## provide the toxicity
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-http-modify-body
spec:
components:
env:
# toxicity is the probability of the request to be affected
# provide the percentage value in the range of 0-100
# 0 means no request will be affected and 100 means all request will be affected
- name: TOXICITY
value: "100"
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
Content encoding and content type
Content encoding and content type of the response body. Tune it by using the CONTENT_ENCODING and CONTENT_TYPE environment variables, respectively.
The following YAML snippet illustrates the use of these environment variables:
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-http-modify-body
spec:
components:
env:
# provide the encoding type for the response body
# currently supported value are gzip, deflate
# if empty no encoding will be applied
- name: CONTENT_ENCODING
value: "gzip"
# provide the content type for the response body
- name: CONTENT_TYPE
value: "text/html"
# provide the body string to overwrite the response body
- name: RESPONSE_BODY
value: "2000"
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
Network interface
Network interface that is used for the proxy. Tune it by using the NETWORK_INTERFACE environment variable.
The following YAML snippet illustrates the use of this environment variable:
## provide the network interface for proxy
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-http-modify-body
spec:
components:
env:
# provide the network interface for proxy
- name: NETWORK_INTERFACE
value: "eth0"
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
# provide the body string to overwrite the response body
- name: RESPONSE_BODY
value: "2000"
Container runtime and socket path
The CONTAINER_RUNTIME and SOCKET_PATH environment variable to set the container runtime and socket file path, respectively.
CONTAINER_RUNTIME: It supportsdocker,containerd, andcrioruntimes. The default value iscontainerd.SOCKET_PATH: It contains path of containerd socket file by default(/run/containerd/containerd.sock). Fordocker, specify path as/var/run/docker.sock. Forcrio, specify path as/var/run/crio/crio.sock.
The following YAML snippet illustrates the use of these environment variables:
## provide the container runtime and socket file path
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
appinfo:
appns: "default"
applabel: "app=nginx"
appkind: "deployment"
chaosServiceAccount: litmus-admin
experiments:
- name: pod-http-modify-body
spec:
components:
env:
# runtime for the container
# supports docker, containerd, crio
- name: CONTAINER_RUNTIME
value: "containerd"
# path of the socket file
- name: SOCKET_PATH
value: "/run/containerd/containerd.sock"
# provide the port of the targeted service
- name: TARGET_SERVICE_PORT
value: "80"
# provide the body string to overwrite the response body
- name: RESPONSE_BODY
value: "2000"