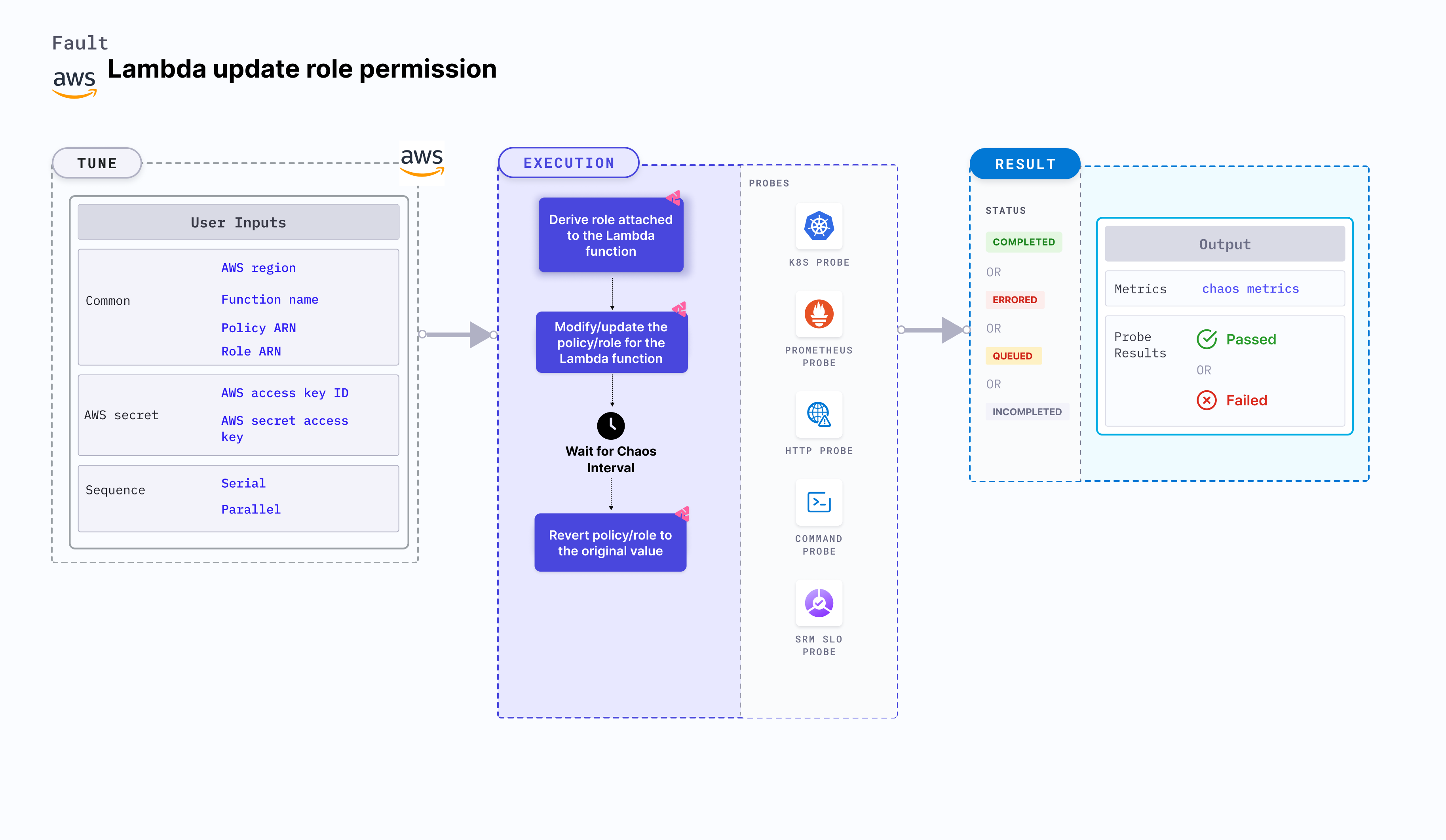
Lambda update role permission
Lambda update role permission is an AWS fault that modifies the role policies associated with a Lambda function. Sometimes, Lambda functions depend on services like RDS, DynamoDB, and S3. In such cases, certain permissions are required to access these services. This fault helps understand how your application would behave when a Lambda function does not have enough permissions to access the services.
Use cases
Lambda updated role permission:
- Verifies the handling mechanism for function failures.
- Updates the role attached to a Lambda function.
- Determines the performance of the running Lambda application when it does not have enough permissions.
Prerequisites
- Kubernetes >= 1.17
- The Lambda function must be up and running.
- Kubernetes secret must have the AWS access configuration (key) in the
CHAOS_NAMESPACE. Below is a sample secret file:apiVersion: v1
kind: Secret
metadata:
name: cloud-secret
type: Opaque
stringData:
cloud_config.yml: |-
# Add the cloud AWS credentials respectively
[default]
aws_access_key_id = XXXXXXXXXXXXXXXXXXX
aws_secret_access_key = XXXXXXXXXXXXXXX
HCE recommends that you use the same secret name, that is, cloud-secret. Otherwise, you will need to update the AWS_SHARED_CREDENTIALS_FILE environment variable in the fault template with the new secret name and you won't be able to use the default health check probes.
Below is an example AWS policy to execute the fault when ROLE_ARN environment variable is set.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"iam:PassRole",
"lambda:GetFunction",
"lambda:UpdateFunctionConfiguration",
"iam:AttachRolePolicy"
],
"Resource": "*"
}
]
}
Below is an example AWS policy to execute the fault when POLICY_ARN environment variable is set.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"iam:DetachRolePolicy",
"lambda:GetFunction",
"iam:ListAttachedRolePolicies",
"iam:AttachRolePolicy",
"iam:GetRolePolicy"
],
"Resource": "*"
}
]
}
- Go to AWS named profile for chaos to use a different profile for AWS faults.
- Go to superset permission/policy to execute all AWS faults.
- Go to the common tunables and AWS-specific tunables to tune the common tunables for all faults and AWS-specific tunables.
Mandatory tunables
| Tunable | Description | Notes |
|---|---|---|
| FUNCTION_NAME | Name of the target Lambda function. It supports a single function name. | For example, test-function. |
| POLICY_ARN | Provide the policy ARN that you want to detach from the role attached | For more information, go to policy ARN. |
| ROLE_ARN | Provide the role arn that you want to update in the lambda function | ROLE_ARN and POLICY_ARN are mutually exclusive. If both are provided, ROLE_ARN takes precedence. For more information, go to role ARN. |
| REGION | The region name of the target lambda function | For example, us-east-2 |
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| TOTAL_CHAOS_DURATION | Duration that you specify, through which chaos is injected into the target resource (in seconds). | Default: 30 s. For more information, go to duration of the chaos. |
| CHAOS_INTERVAL | The interval (in seconds) between successive policy/role detach/update. | Default: 30 s. For more information, go to chaos interval. |
| AWS_SHARED_CREDENTIALS_FILE | Path to the AWS secret credentials. | Default: /tmp/cloud_config.yml. |
| SEQUENCE | It defines sequence of chaos execution for multiple instance | Default: parallel. Supports serial and parallel. For more information, go to sequence of chaos execution. |
| RAMP_TIME | Period to wait before and after injection of chaos in seconds | For example, 30 s. For more information, go to ramp time. |
Role ARN
Updates the role attached to a Lambda function. Tune it by using the ROLE_ARN environment variable.
The following YAML snippet illustrates the use of this environment variable:
# contains the role arn for the lambda function
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
chaosServiceAccount: litmus-admin
experiments:
- name: lambda-update-role-permission
spec:
components:
env:
# provide the role arn
- name: ROLE_ARN
value: 'arn:aws:iam::ACCOUNT_ID:role/service-role/chaos-role'
# provide the function name
- name: FUNCTION_NAME
value: 'chaos-function'
Policy ARN
Detaches the policies attached to the role of Lambda function. Tune it by using the POLICY_ARN environment variable.
Setting the ROLE_ARN environment variable updates the role attached to the Lambda function. Otherwise, the policy is detached using the POLICY_ARN environment variable.
The following YAML snippet illustrates the use of this environment variable:
# contains the policy arn for the lambda function
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
chaosServiceAccount: litmus-admin
experiments:
- name: lambda-update-role-permission
spec:
components:
env:
# provide the policy arn
- name: POLICY_ARN
value: 'arn:aws:iam::ACCOUNT_ID:policy/service-role/chaos-policy'
# provide the function name
- name: FUNCTION_NAME
value: 'chaos-function'