Generate SBOM for Repositories
A Software Bill of Materials (SBOM) is a comprehensive list of all components, libraries, and dependencies used in a software application. The SBOM Orchestration step in Harness Software Supply Chain (SCS) allows you to generate SBOMs for both code repositories and software artifacts, providing visibility into the components that make up your software.
If you already possess an SBOM and wish to ingest it, please refer to the Ingest SBOM section.
SBOM Orchestration step configuration
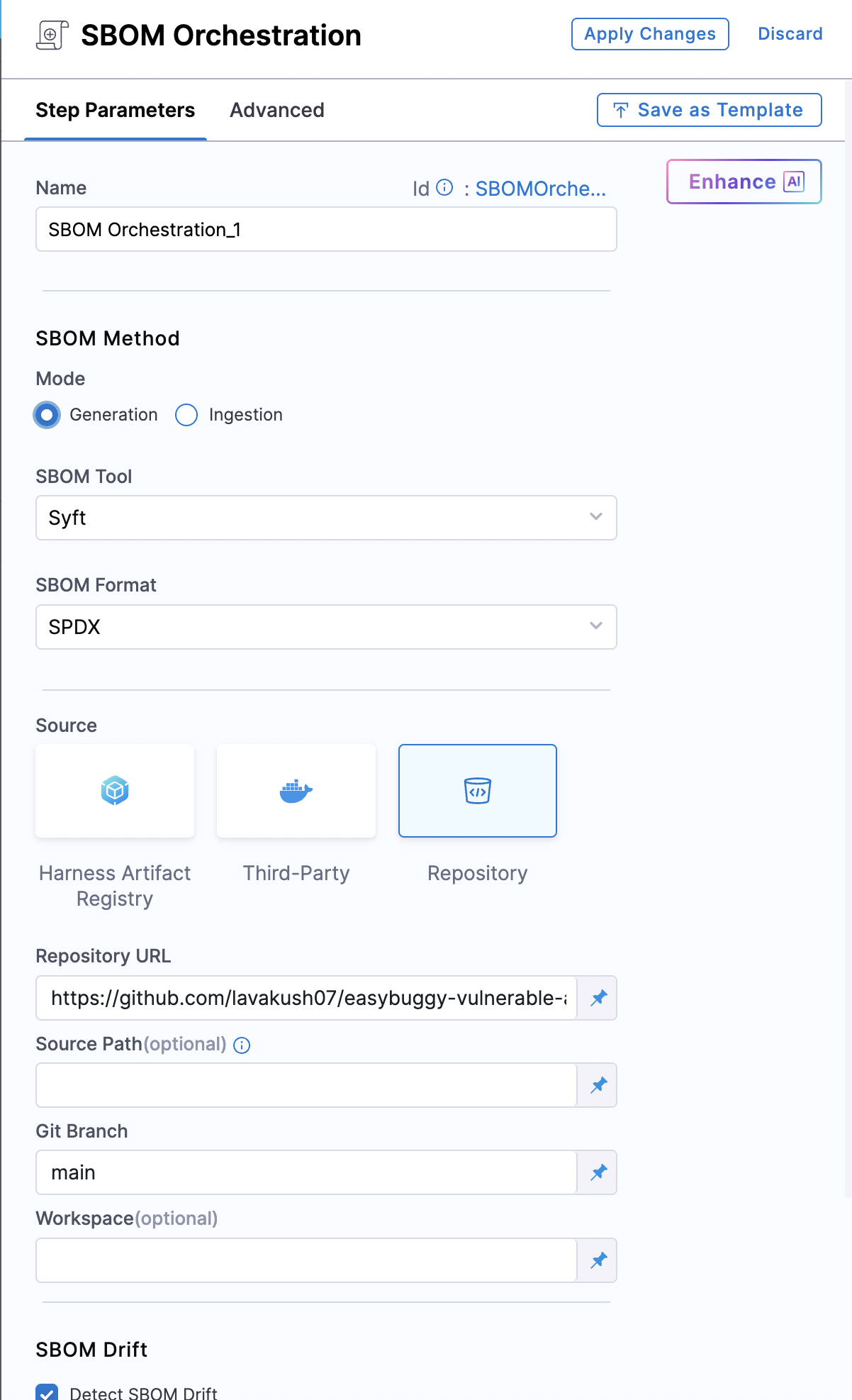
You can use SBOM Orchestration step to generate an SBOM in either the Build or Deploy stage of a Harness pipeline.
- In a Build stage, add the SBOM Orchestration step after the artifact (image) has been pushed to an artifact repository.
- In a Deploy stage, add the SBOM Orchestration step before the deployment step.
SBOM Orchestration step in deploy stage can only be used in the Containerized Step Groups and ensure you enable the container based execution.
Using SBOM Orchestration step you can generate the SBOM for both Container images and Repositories. Follow the steps to configure the fields for each supported type.
-
Name: Enter a name for the step.
-
Step Mode: Select Generation.
-
SBOM Tool: Select Syft or cdxgen. For other SBOM tools, go to Ingest SBOM.
-
SBOM Format: Select SPDX or CycloneDX.
If you're using Syft to generate the SBOM and want to ensure it includes all component licenses with high accuracy, you'll need to set specific environment variables based on your project's programming language. Here are the relevant variables:
Set variables for enhanced SBOM
| Programming Language | Name of Variable | Value |
|---|---|---|
| Go | SYFT_GOLANG_SEARCH_REMOTE_LICENSES | true |
| Java | SYFT_JAVA_USE_NETWORK | true |
| JavaScript | SYFT_JAVASCRIPT_SEARCH_REMOTE_LICENSES | true |
To add a new environment variable, go to Overview section of your Build stage, and expand the Advanced section.
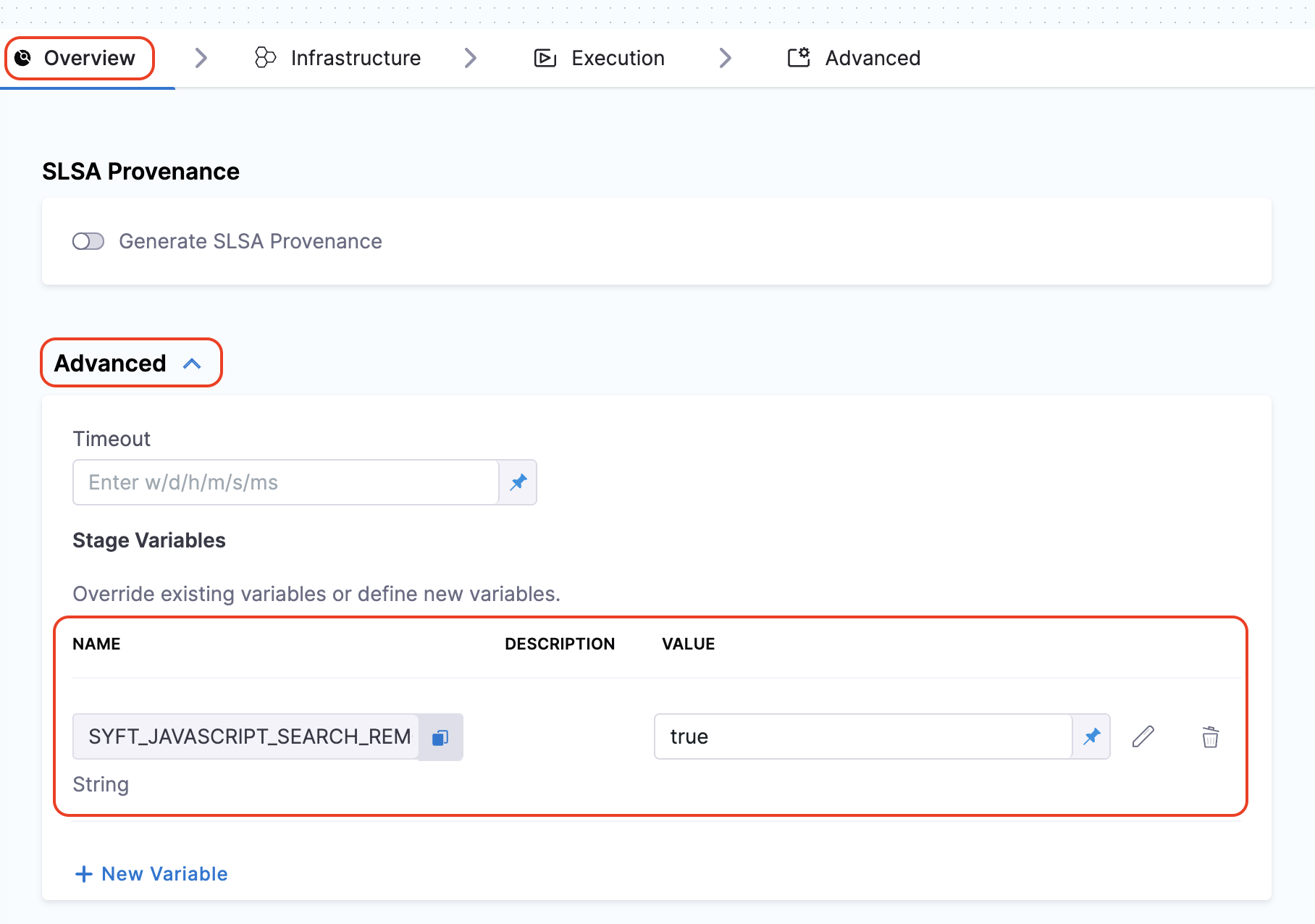
By setting these variables, Syft can more effectively fetch and populate the licensing data for the components in your SBOM. This not only enhances the quality of the SBOM but also improves its overall SBOM score. If your SBOM contains NOASSERTIONS, it indicates that Syft was unable to retrieve necessary data.
Configure cdxgen with Extended Java Support
If you are using cdxgen to generate an SBOM, the default cdxgen image doesn’t include all Java runtime dependencies.
To resolve this, override the default cdxgen image by providing the tag cdxgen-full in the optional configuration section of the SBOM Orchestration step to enable extended Java support.
Container Registry: By default, Harness pulls cdxgen image from Docker Hub. To pull the image from private registry, select a connector that points to it.
Image tag: Provide the tag cdxgen-full to support environments like Java.
Limit Memory and CPU: Set the minimum memory to 8 Gi and CPU to 4.
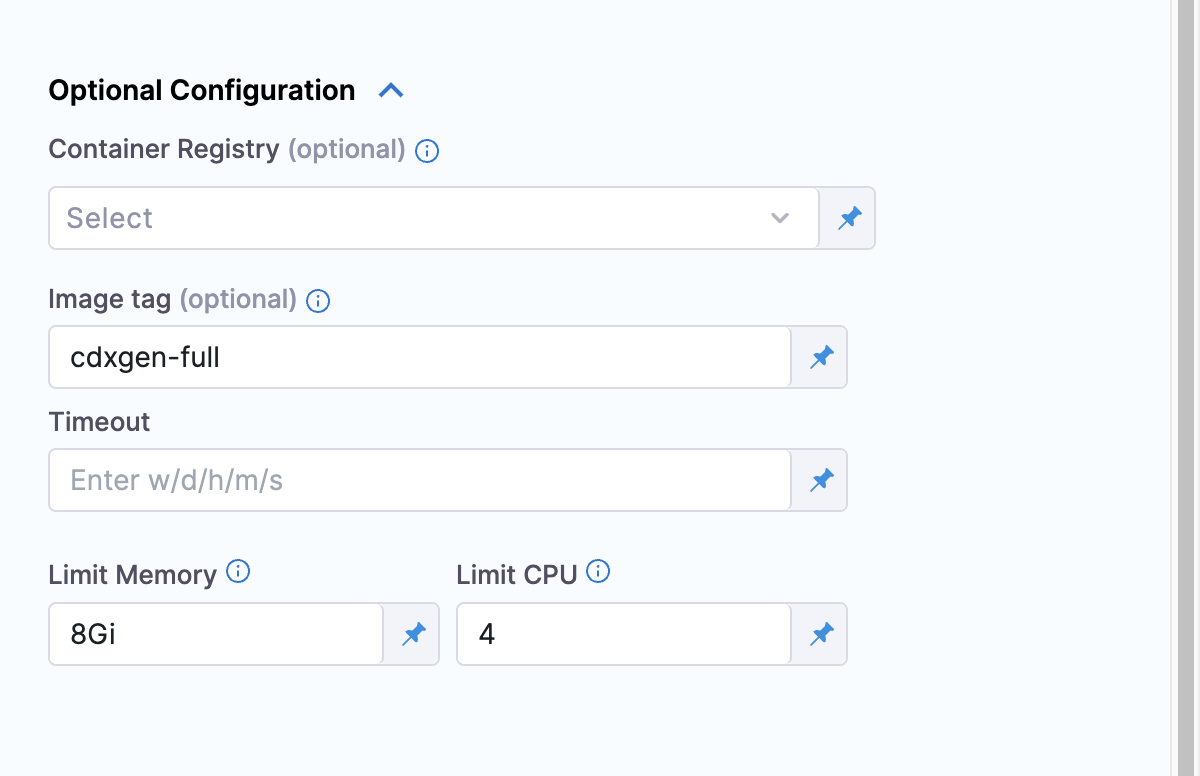
The CocoaPods ecosystem is not fully supported by cdxgen at the moment
-
Source: Select the Source as a Repository to generate the SBOM for source code.
-
Repository URL: The Repository URL you've configured for cloning into the workspace.
-
Source Path: Leave blank or enter a path (in the repository) for which you want to generate SBOM. Use this setting to generate SBOM for a specific section of your code repo, rather than your entire repo. The path must start with
/. For example, if your repository URL ishttps://github.com/username/repo, and you want to generate SBOM forhttps://github.com/username/repo/service-core/source, then enter/service-core/sourcefor Source Path. To generate an SBOM for the entire repository, leave this field empty. -
Git Branch: The branch of the repository for which you want to generate the SBOM.
-
Workspace: If you cloned the codebase to a different directory than the root workspace directory (
/harness), enter the path to the subdirectory using the format/harness/PATH/TO/SUBDIRECTORY. Leave this field empty if you cloned your codebase into the default directory (/harness). Usually, your codebase is only cloned into a non-default directory if you are cloning multiple codebases into a pipeline.
Make sure your repository is cloned into the stage workspace before the SBOM Orchestration step runs. There are several ways you can do this:
- Clone the codebase by default, such as a Build stage's default codebase.
- Add a Git Clone step or Run step to the Deploy stage.
- Add a Git Clone step or Run step to a Build stage.
Configure SBOM Drift
This feature allows you to track changes in SBOMs by comparing them against a Git branch. It provides a detailed analysis of addition or removal of components and licenses, helps you manage and oversee repositories more effectively. You can configure the comparison to be between any two branches. For example, comparing a feature branch against the main branch to identify SBOM drift before merging. However, this is optional and not required for SBOM generation. If you prefer not to detect changes in SBOMs, simply leave this option unchecked.
Run the pipeline
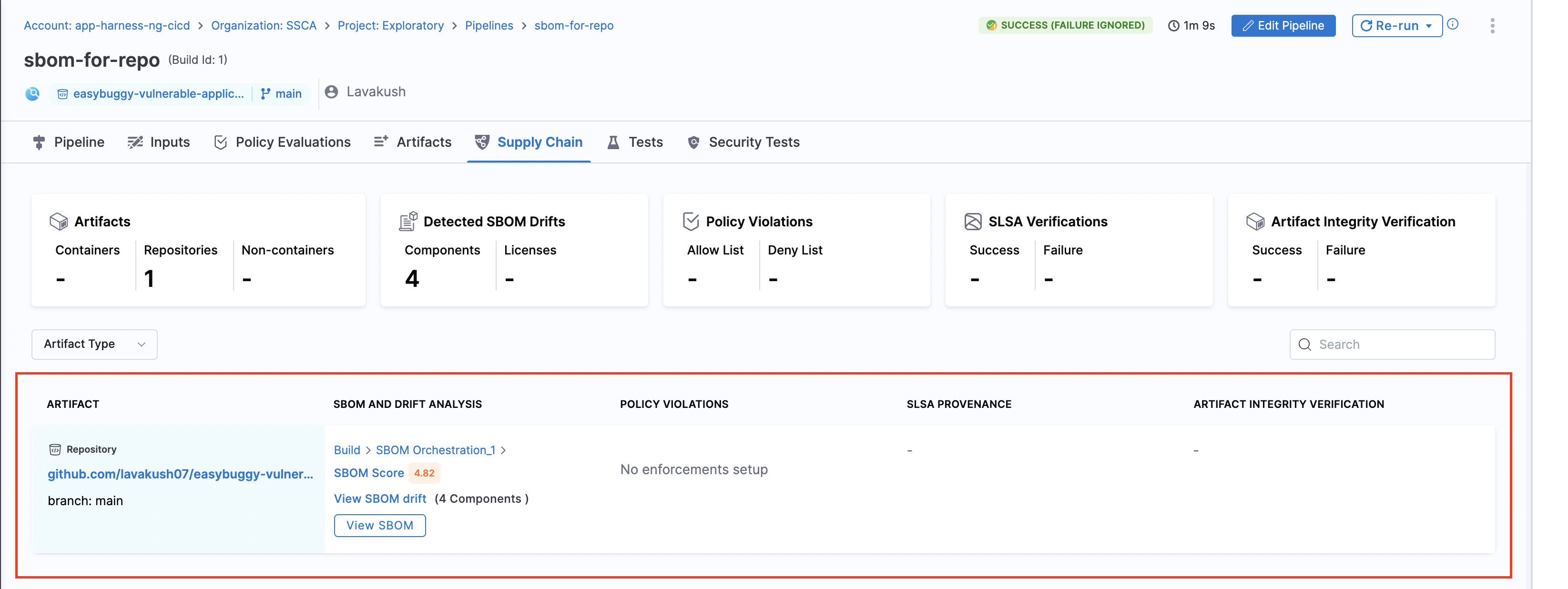
When the pipeline runs, the generated SBOMs for Code Repositories are accessible in the Artifacts view. Additionally, you can locate the SBOM for any artifact on the Supply Chain tab within the Execution Details page in Harness.
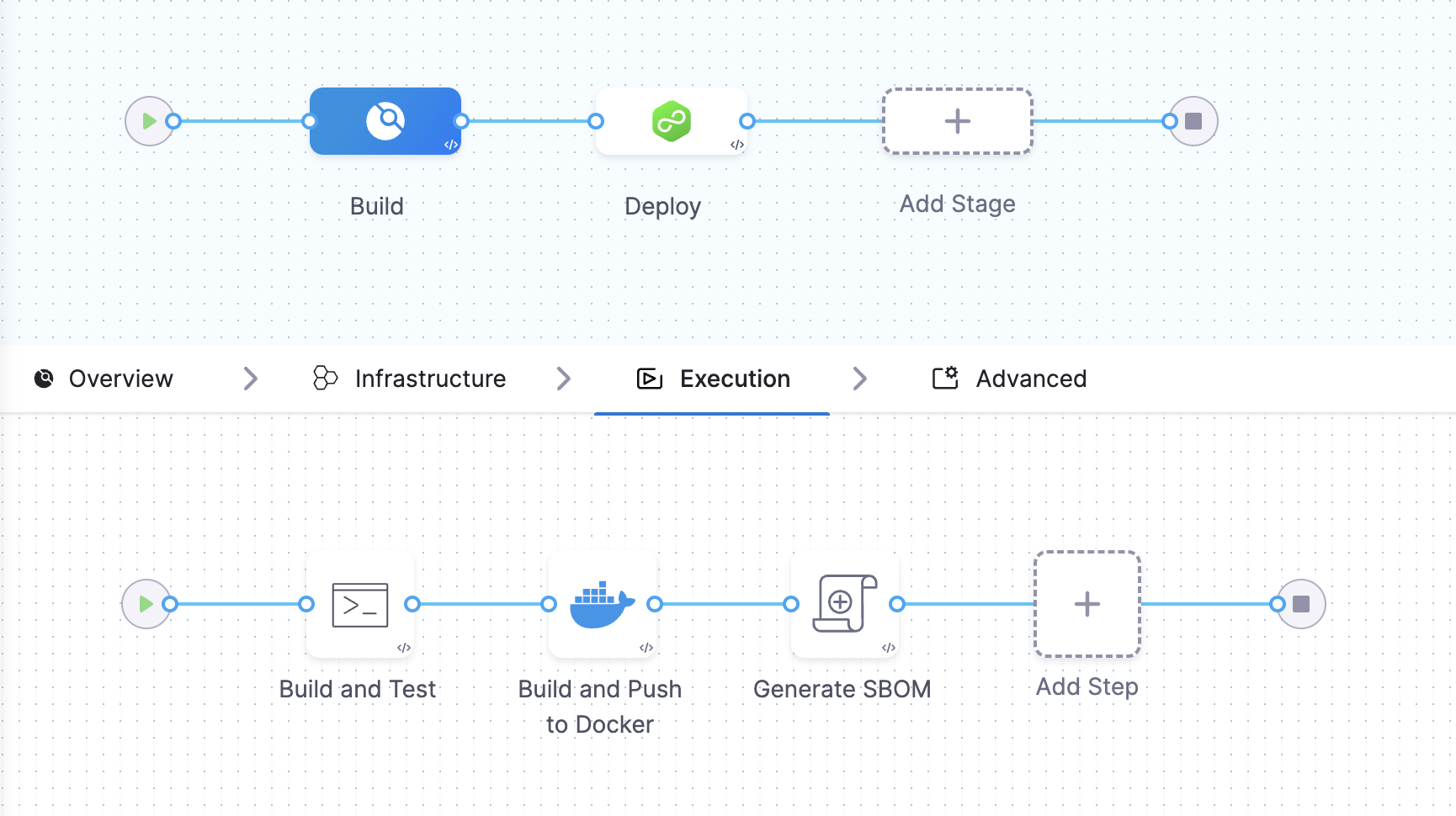
Example Pipeline for SBOM generation
These example demonstrate how you could set up Build and Deploy stages to generate SBOM.
- Build stage
- Deploy stage
This example Build stage has three steps:
- Run step: Build and test an artifact (image).
- Build and Push an image to Docker Registry step: Build and push the image to a Docker registry.
- SBOM Orchestration step: Generate the SBOM.
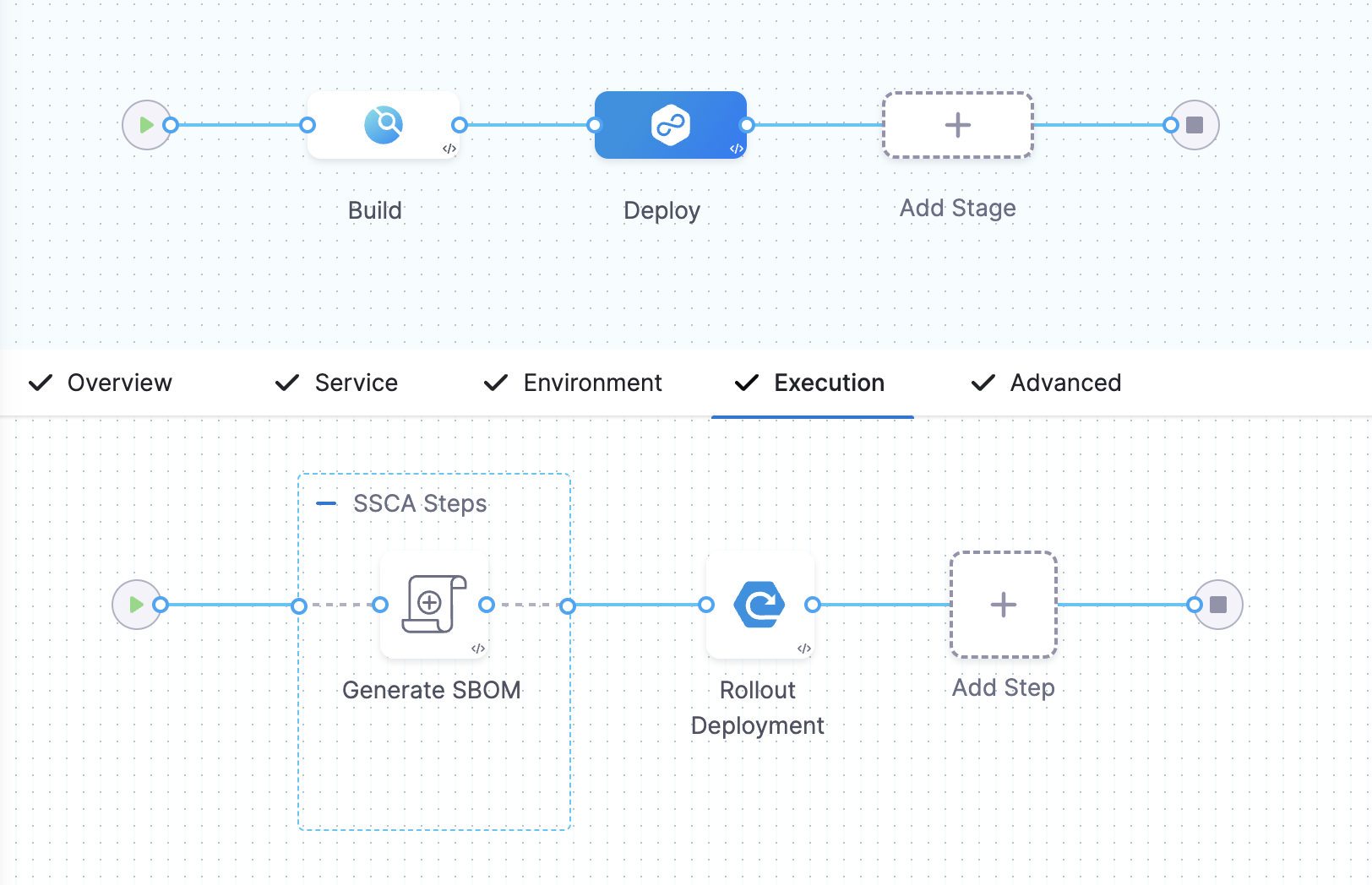
SBOM Orchestration in deploy stage can only be used in the Containerized Step Groups This example Deploy stage has two steps:
- SBOM Orchestration step: Generate the SBOM.
- Rolling deployment step: Deploy the image.
View vulnerabilities in the SBOM
After you run the SBOM orchestration step followed by the STO Snyk scan, the SBOM tab on the Code Repositories page displays vulnerabilities for the components identified by Snyk. This helps you effectively identify and prioritize open source risks.
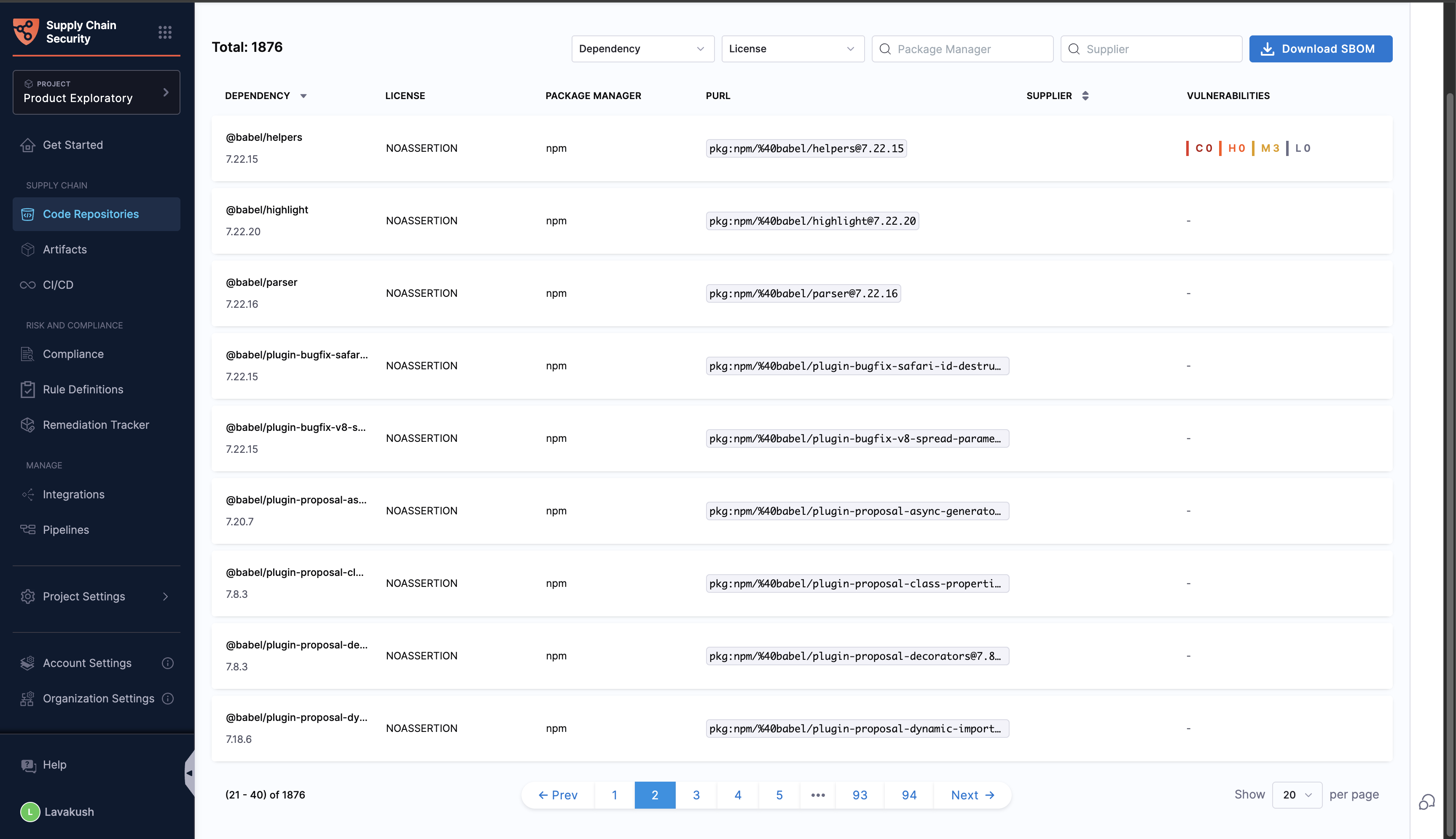
Publish SBOM
After you run the SBOM Orchestration step, you can download or publish SBOM through multiple ways depending on your workflow:
- Via Harness API
- Use the Download SBOM button available on the Code Repositories page.
- Download the SBOM score for repository via Harness API
- Access the SBOM file directly from the pipeline output at the specified path
/harness/sbom/{sbom_<sbom_orchestration_step_execution_id>}.json.
Next steps
After generating an SBOM, you can apply SBOM Policy Enforcement to achieve open source governance.