Add a Google Cloud secret manager
You can link your Google Cloud Secret Manager to Harness and use it to store any sensitive data you use in Harness, including secrets.
Harness also supports Google KMS as a secrets manager. This topic explains how to add a GCP Secrets Manager in Harness.
You can only use Harness Built-in Secret Manager to store authentication credentials for access to the corresponding secret manager.
Storing credentials from one secret manager within another can result in complex and challenging situations. Moreover, these configurations might introduce vulnerabilities, posing potential security risks.
The Harness platform has several validations, including the disabling of self-references.
Before you begin
You need an understanding of:
Google Cloud secret manager important notes
- Inline secrets saved to GCP Secrets Manager must follow the naming limitations of Google Cloud Secret Manager. Secret names can only contain alphabets, numbers, dashes (-), and underscores (_). Google Secret Manager restrictions are subject to change. Go to Secret Manager in the GCP documentation for details.
- The maximum size for encrypted files saved to Google Cloud Secret Manager is 64KiB.
- Inline secrets saved to Google Cloud Secret Manager have a region assignment by default. An automatic assignment is the same as not selecting the Regions setting when creating a secret in Google Cloud Secret Manager.
- Harness does not support Google Cloud Secret Manager labels at this time.
- Versions for reference secrets:
- Any modification to the content of a secret stored by Harness in Google Cloud Secret Manager creates a new version of that secret.
- When you delete a secret present in Google Cloud Secret Manager from Harness, the entire secret is deleted and not just a version.
- You cannot update the name of an inline or referenced secret stored in the Google Cloud Secret Manager using the Harness Secret Manager.
- Harness does not support changing an inline secret to a reference secret or vice versa in Harness.
Google Cloud secret manager permission requirements
- Make sure you have Create/Edit permissions for Secrets.
- Make sure you have Create/Edit permissions for connectors.
- The GCP Service Account you use in the Google Secrets Manager Credentials File should have the following IAM roles:
roles/secretmanager.adminorroles/secretmanager.secretAccessorandroles/secretmanager.secretVersionManager.
Go to Managing secrets from Google.
Add a Google Cloud secret manager
This topic assumes you have a Harness Project set up. If not, go toCreate Organizations and Projects.
You can add a connector from any module in your project, in the Project setup, or in your organization or account resources.
This topic explains the steps to add a Google Cloud Secrets Manager to the account scope.
-
In your Harness Account, select Account Settings.
-
Select Account Resources.
-
Select Connectors and then select New Connector.
-
In Secret Managers, select GCP Secrets Manager. The GCP Secrets Manager settings appear.
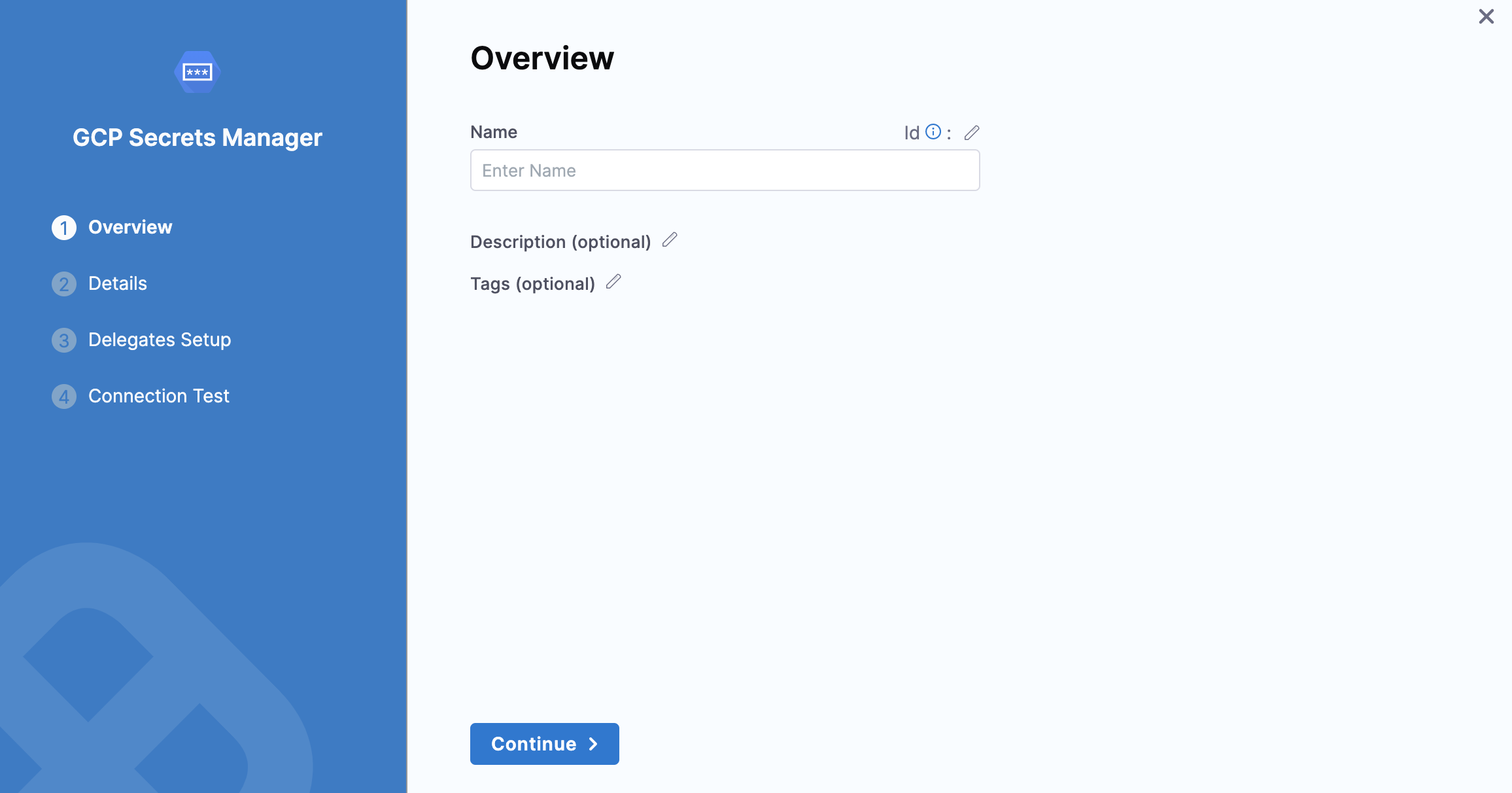
Add overview
- In Name, enter a name for your secret manager.
- You can choose to update the Id or let it be the same as your secret manager's name. For more information, go to Entity Identifier Reference.
- Enter the Description for your secret manager.
- Enter Tags for your secret manager.
- Click Continue.
Configure details
Select one of the following options to configure details for the Google cloud secret manager:
- Specify credentials here
- Use the credentials of a specific Harness Delegate (IAM role, service account, etc)
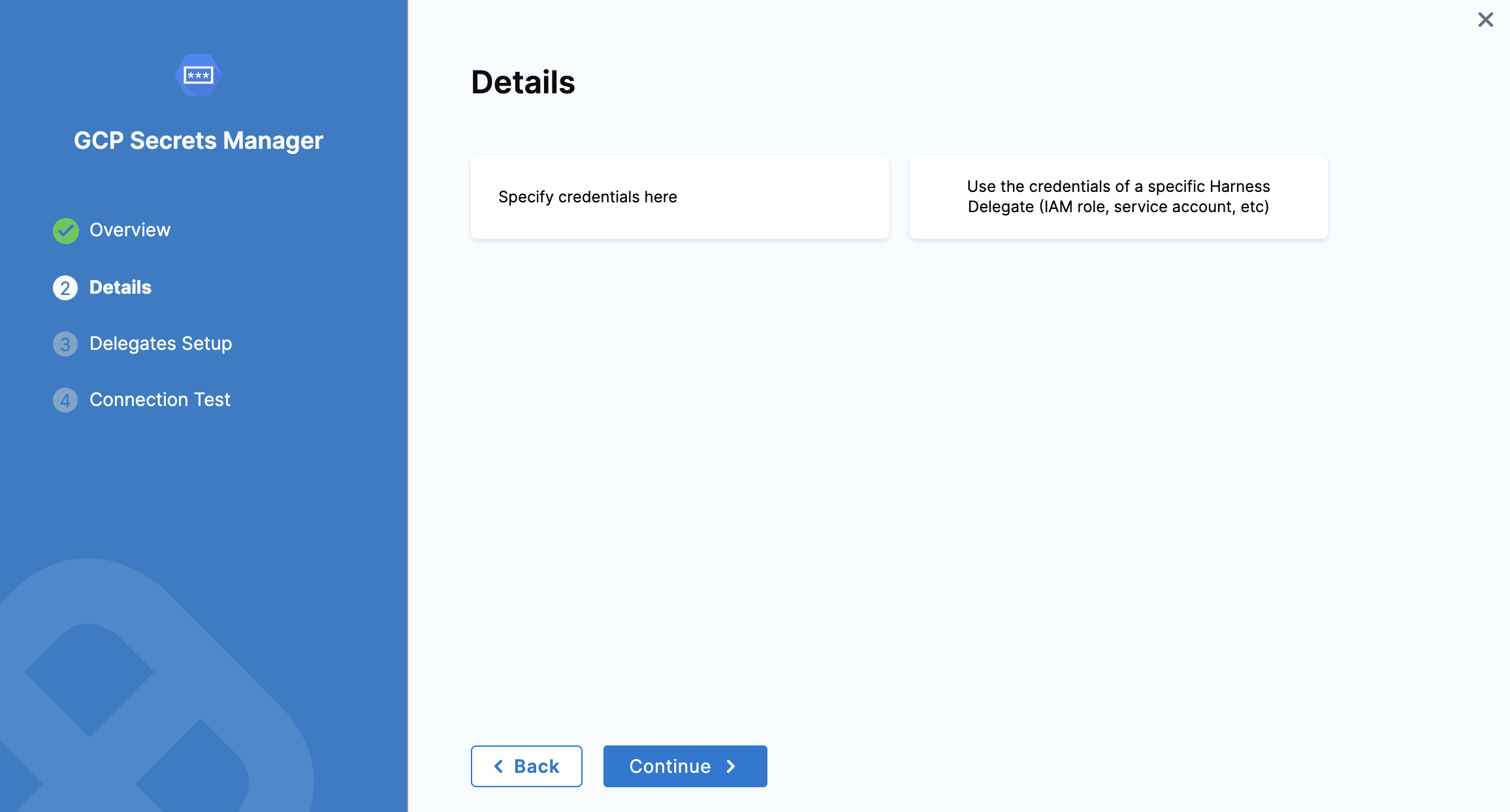
Specify credentials here
Attach a Google Secret Manager credentials file
You must export your Google Cloud service account key and add it as an Encrypted File Secret in Harness.
-
In the Google Cloud console, select IAM & admin > Service account.
-
Scroll to the service account you want to use. If no service account is present, create one.
-
Grant this service account the Google Cloud Secret Manager permissions needed. To do this, edit the service account and select Permissions. Click Roles, and then add the roles needed. Go to Managing secrets in the Google Cloud documentation.
-
Open your service account's Actions ⋮ menu, then select Create key.
-
In the resulting Create private key dialog, select the JSON option, create the key, and download it to your computer.
-
Go back to Harness.
-
In Google Secrets Manager Credentials File, select the encrypted file you just added in Harness.
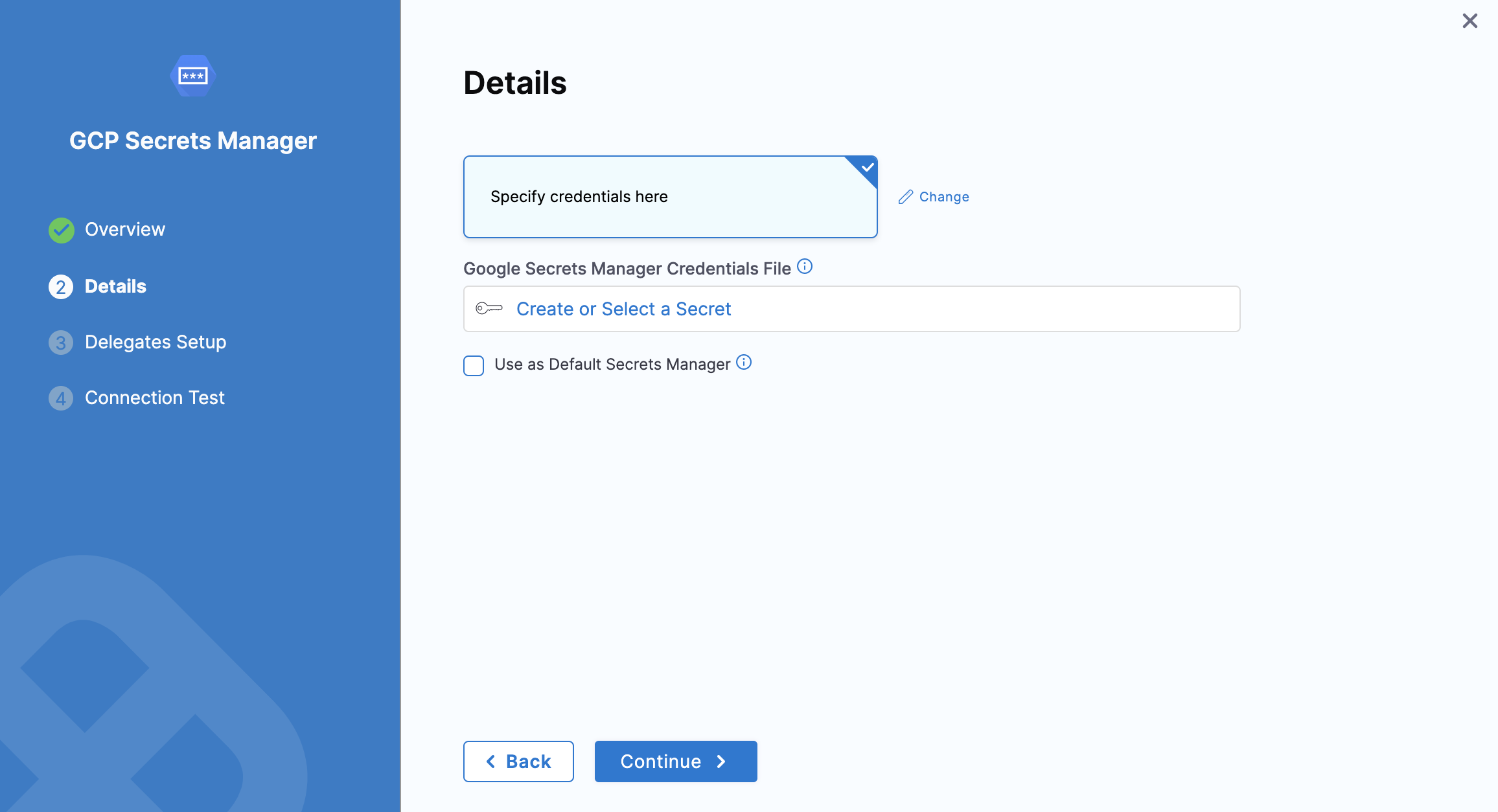
You can also create a new File Secret here and add the Google Cloud service account key that you downloaded.
-
Click Continue.
Use the credentials of a specific Harness Delegate (IAM role, service account, etc)
If you select this option, Harness will authenticate using the IAM role assigned to the specific delegate you select. This would be the Application Default Credentials.
For more information, go to Application Default Credentials.
You can select a delegate using a Delegate Selector.
Click Continue.
Step 4: Setup delegates
- In Delegates Setup, enter Selectors for specific delegates that you want to allow to connect to this connector.
- Click Save and Continue.
Step 5: Test connection
Once the Test Connection succeeds, select Finish. You can now see the connector in Connectors.
Add an inline secret to the GCP Secrets Manager
Let us add an inline text secret to the GCP Secrets Manager we just created.
-
In your Harness account, select Account Settings.
-
Select Account Resources and then select Secrets.
-
Select New Secret, and then select Text. The Add new Encrypted Text settings appear.
-
Select the GCP Secrets Manager you just created.
-
Enter a Name for your secret.
-
The default selection is Inline Secret Value.
-
Enter the Secret Value.
-
Select Configure Region to add the region(s) for your secret.
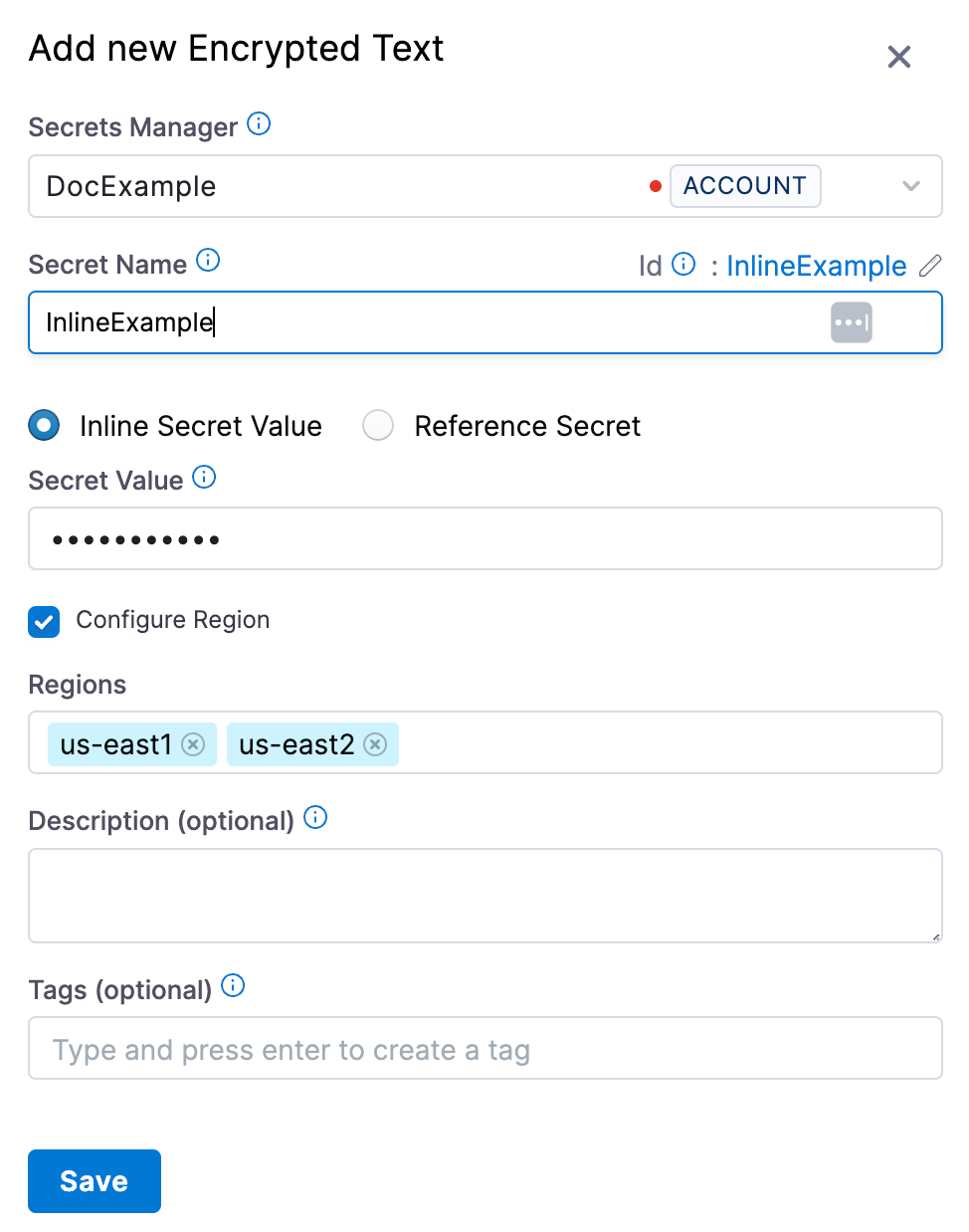
-
Select Save.
Add a secret reference to the GCP Secrets Manager
Let us add a secret reference to the GCP Secrets Manager we just created.
-
In your Harness account, select Account Settings.
-
Select Account Resources and then select Secrets.
-
Select New Secret and then select Text. The Add new Encrypted Text settings appear.
-
Select the GCP Secrets Manager you just created.
-
Enter a Name for your secret.
-
Select Reference Secret.
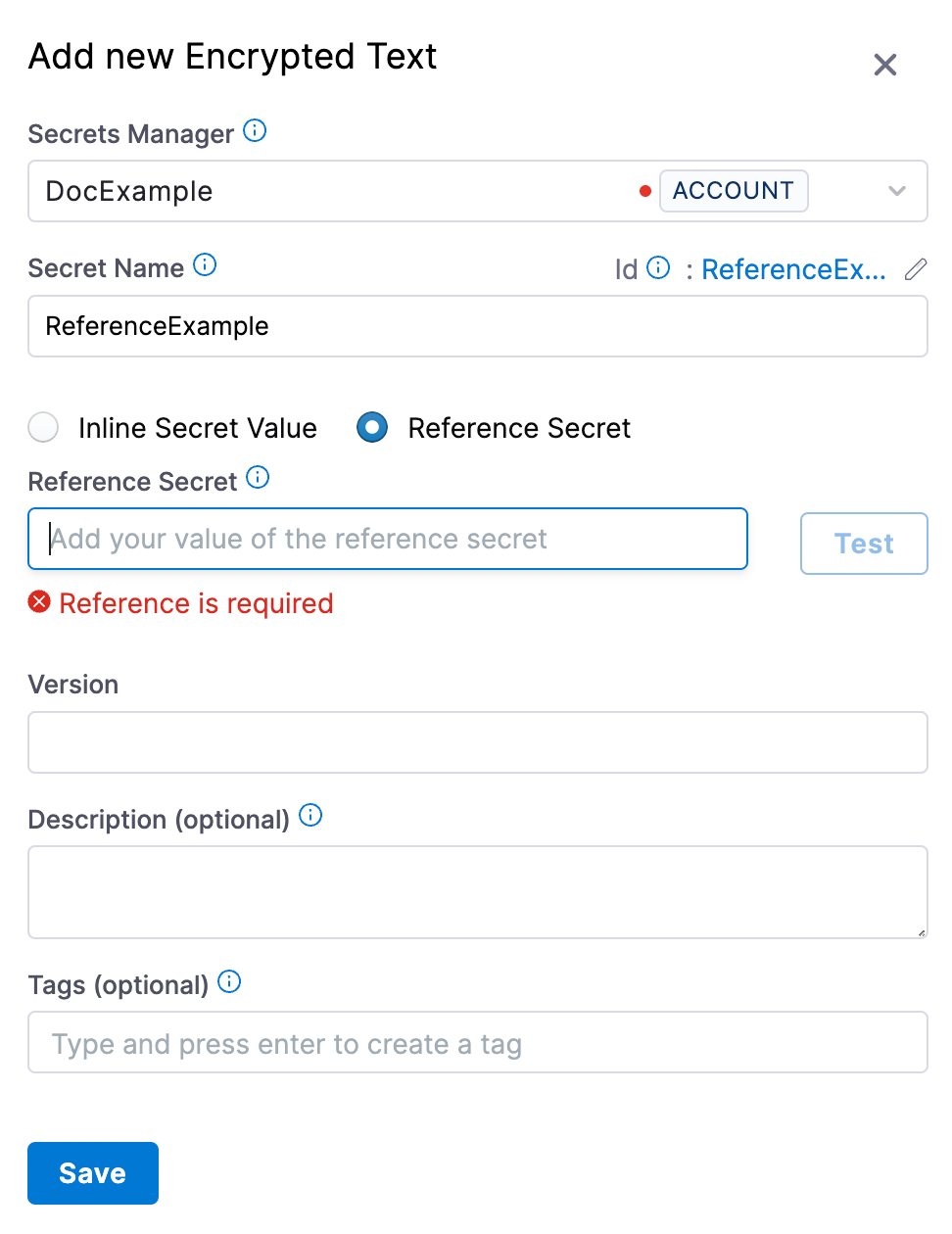
-
Enter your secret identifier in Reference Secret Identifier.
-
In Version, enter the version of your secret that you want to reference. You can either enter a version number like
1,2, or enterlatestto reference the latest version. -
Click Save.
Add an encrypted file secret to the GCP Secrets Manager
Let us add an encrypted file secret to the GCP Secrets Manager we just created.
-
In your Harness account, select Account Settings.
-
Select Account Resources and then select Secrets.
-
Select New Secret and then select File. The Add new Encrypted File settings appear.
-
Select the GCP Secrets Manager you just created.
-
Enter a Name for your secret.
-
In Select File, browse, and select your file.
-
Select Configure Region to add the region(s) for your secret.
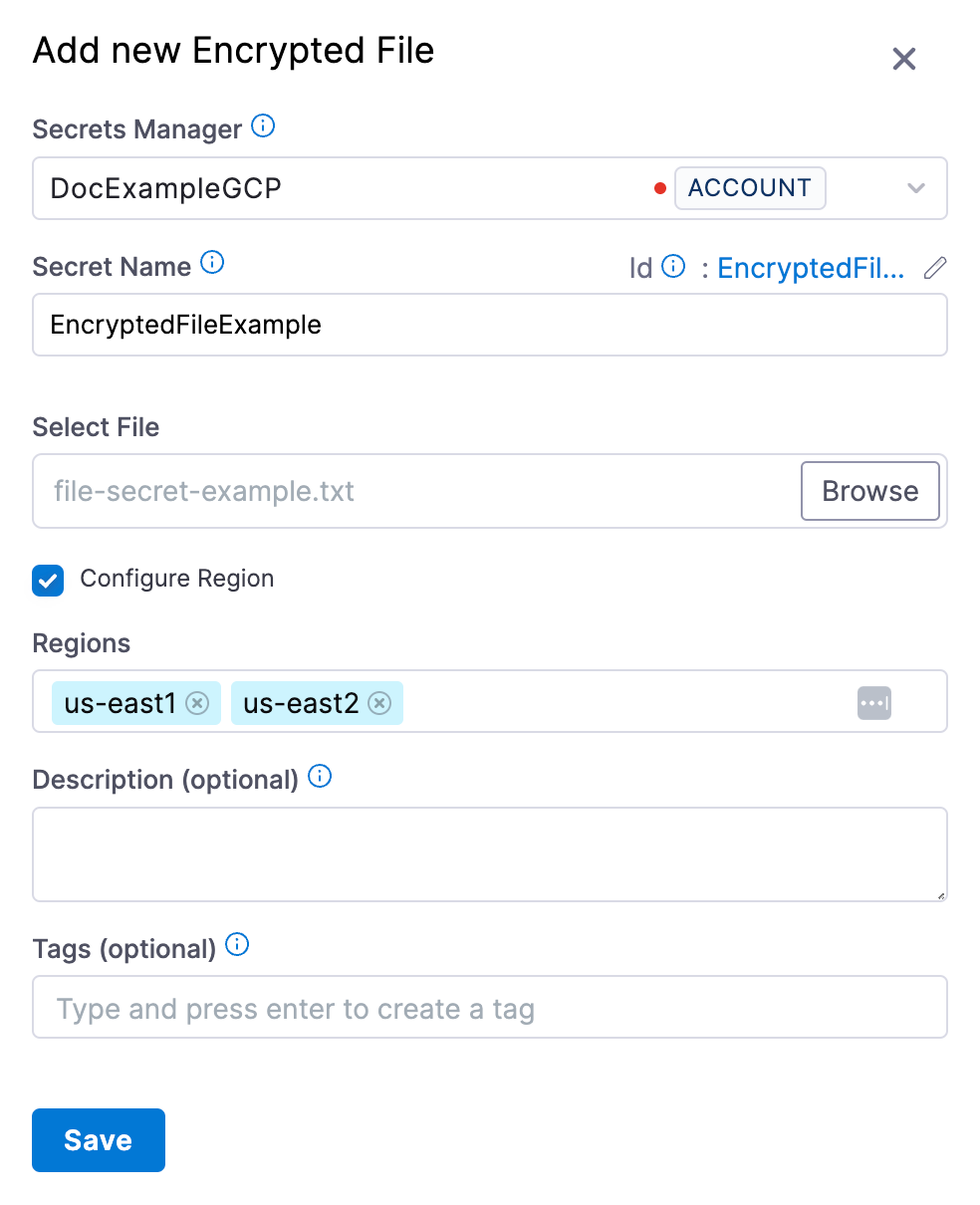
-
Click Save.
Reference JSON secrets
Harness allows you to manage the lifecycle of your secrets independently by referencing JSON secrets in the vault.
For example, you can store a secret in vault with the following JSON.
{
"key1": "value1",
"key2": {
"key21": "value21",
"key22": "value22"
},
"key3": {
"key31": {
"key311": "value311"
}
}
}
Here are sample outputs for the respective JSONPath from the above JSON file:
test-secret (without any # key)
{
"key1": "value1",
"key2": {
"key21": "value21",
"key22": "value22"
},
"key3": {
"key31": {
"key311": "value311"
}
}
}
test-secret#key1
"value1"
test-secret#key2
{
"key21": "value21",
"key22": "value22"
}
test-secret#key3
{
"key31": {
"key311": "value311"
}
}
test-secret#key3.key31
{
"key311": "value311"
}
test-secret#key3.key31.key311
"value311"
You cannot use a JSON XPath for nested keys in expressions. For example, <+secrets.getValue("account.YOUR_SECRET_MANAGER://myVault/harness/testpath/example")>.
Harness provides limited support for keys that include dots. Keys with dots only work when the key is present at first level in the JSON. For example:
{
"key.abc": "some-value",
"key": {
"nested.key1": "some-value"
},
"key.pqr": {
"nestedKey": "some-value"
},
"pqr.xyz": "some-value",
"pqr": {
"xyz": "some-nested-value"
}
}
Here are sample outputs for the respective JSONPath from the above JSON file:
/path/to/secret#key.abcreturnssome-value./path/to/secret#key.pqrreturns{"nestedKey": "some-value"}./path/to/secret#key.nested.key1andkey.pqr.nestedKeyare not supported./path/to/secret#pqr.xyzreturnssome-nested-valueand notsome-value. (Hierarchical paths take precedence over keys with dots.)
Harness does not recommend using keys that include dots and might deprecate support in future releases.